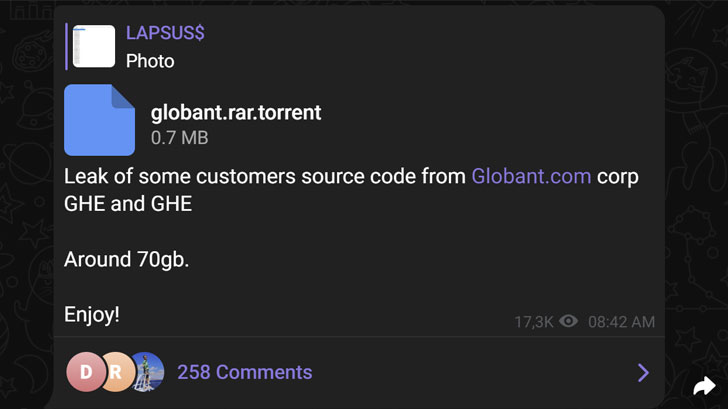
The LAPSUS$ data extortion gang announced their return on Telegram after a week-long "vacation," leaking what they claim is data from software services company Globant.
"We are officially back from a vacation," the group wrote on their Telegram channel – which has nearly around 54,000 members as of writing – posting images of extracted data and credentials belonging to the company's DevOps infrastructure.
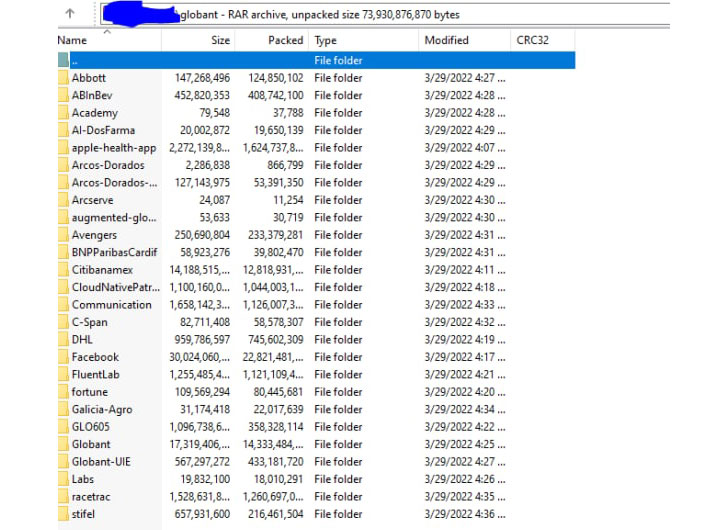
The screenshots depict a folder listing for what appears to be different companies from across the world, including Arcserve, Banco Galicia, BNP Paribas Cardif, Citibanamex, DHL, Facebook, Stifel, among others.
Also shared is a torrent file purported to contain around 70GB of Globant's source code as well as administrator passwords associated with the firm's Atlassian suite, including Confluence and Jira, and the Crucible code review tool.
As malware research group VX-Underground points out, the passwords are not only easily guessable, but they have also been reused multiple times, prompting LAPSUS$ to call out the "poor security practices in use" at the company.
When reached for a response, Globant confirmed the incident stating it "recently detected that a limited section of our company's code repository has been subject to unauthorized access," adding it's currently "conducting an exhaustive investigation" and that it's "taking strict measures to prevent further incidents."
"According to our current analysis, the information that was accessed was limited to certain source code and project-related documentation for a very limited number of clients," the Luxembourg-headquartered company stated. "To date, we have not found any evidence that other areas of our infrastructure systems or those of our clients were affected."
The LAPSUS$ extortion group, since their emergence in December 2021, have been in the spotlight for their headline-grabbing hacks on Impresa, NVIDIA, Samsung, Vodafone, Ubisoft, Microsoft, and Okta.
The latest data heist arrives as The City of London Police said it arrested and released seven alleged operatives of the criminal cartel aged between 16 and 21 under investigation last week. But if the latest leak is any indication, the law enforcement actions have not put a stop to their operations.
The U.S. Federal Bureau of Investigation, on March 21, added the group to its "Most Wanted" list, seeking information regarding the identities of the individuals responsible for cyber intrusions targeting U.S.-based technology companies and for disseminating the illegally obtained proprietary data.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
227
2 years ago
227 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·