BOOK THIS SPACE FOR AD
ARTICLE AD
Offices of multiple Japanese agencies were breached via Fujitsu's "ProjectWEB" information sharing tool.
Fujitsu states that attackers gained unauthorized access to projects that used ProjectWEB, and stole some customer data.
It is not yet clear if this breach occurred because of a vulnerability exploit, or a targeted supply-chain attack, and an investigation is ongoing.
Attackers accessed at least 76,000 email addresses
Yesterday, the Ministry of Land, Infrastructure, Transport and Tourism and the National Cyber Security Center (NISC) of Japan announced that attackers were able to obtain inside information via Fujitsu's information-sharing tool.
Fujitsu also said that attackers had gained unauthorized access to projects that used ProjectWEB, and stolen proprietary data.
Fujitsu's ProjectWEB enables companies and organizations to exchange information internally, with project managers and stakeholders, for example.
By gaining unauthorized access to government systems via ProjectWEB, attackers were able to obtain at least 76,000 e-mail addresses, and proprietary information, including the e-mail system settings, as confirmed by the Ministry of Land, Infrastructure, Transport, and Tourism.
As of 2009, the tool was in widespread use by approximately 7,800 projects, according to a Fujitsu document seen by BleepingComputer:
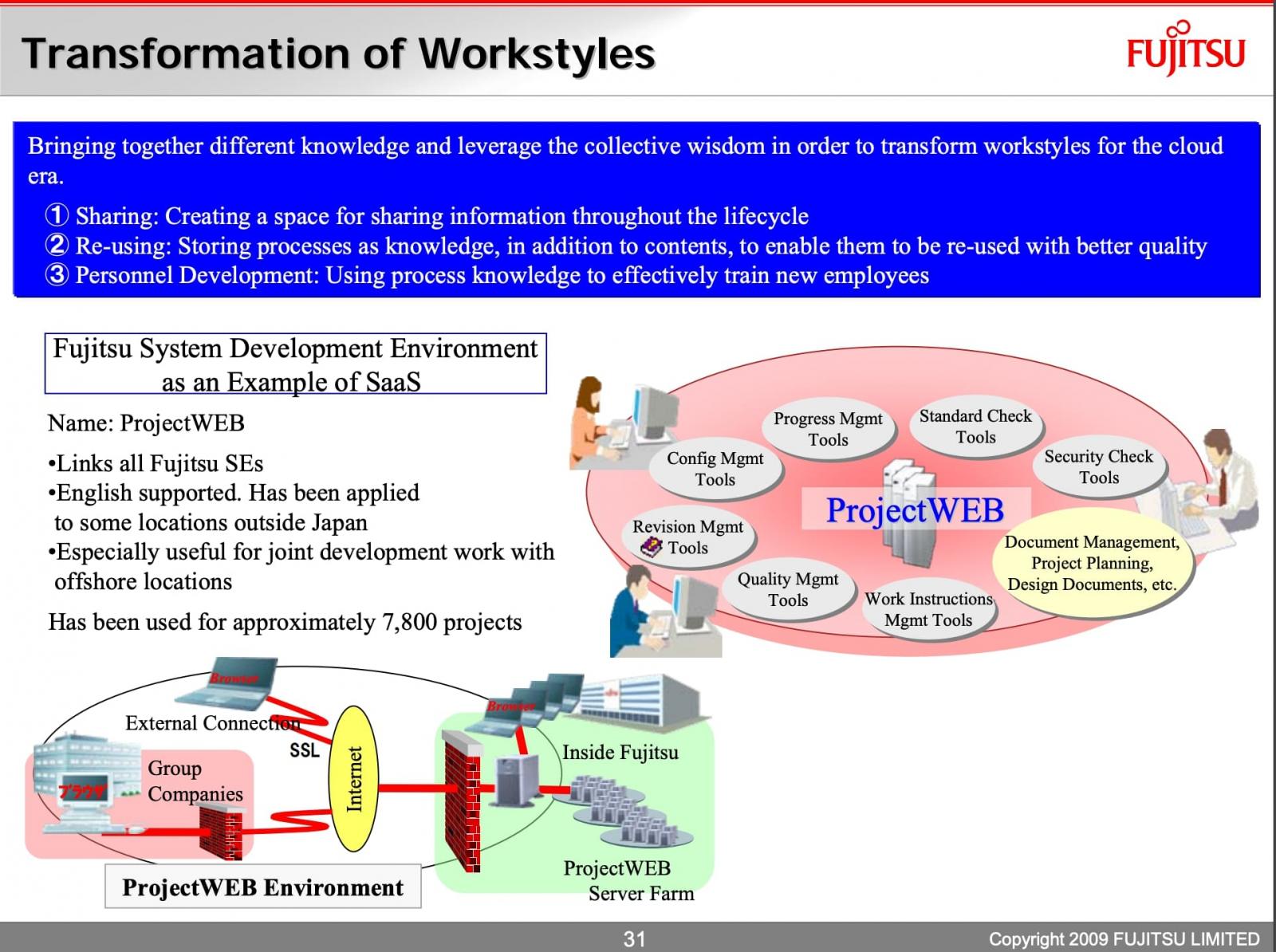 Fujitsu ProjectWEB overview illustrating different use cases of the info-sharing tool
Fujitsu ProjectWEB overview illustrating different use cases of the info-sharing tool The exposed email addresses included those of external parties, such as members of the Council of Experts, who have been individually notified.
Japanese press also reported Narita International Airport, located near Tokyo, was impacted as well since Fujitsu attackers managed to steal air traffic control data, flight schedules, and business operations.
Additionally, Japan's Ministry of Foreign Affairs also suffered from a data leak to unauthorized actors.
As such, Cabinet Secretariat's national cybersecurity center (NISC) issued multiple advisories [1, 2] alerting government agencies and critical infrastructure organizations using Fujitsu's tool to check for signs of unauthorized access and information leakage.
Fujitsu suspends ProjectWEB online portal
As seen by BleepingComputer, Fujitsu has suspended its ProjectWEB portal while the scope and cause of this incident are being fully investigated.
The URL to the login portal has been timing out when access is attempted:
https://pjshr170.soln.jp/IJS02E8/pjwebroot/login.jsp
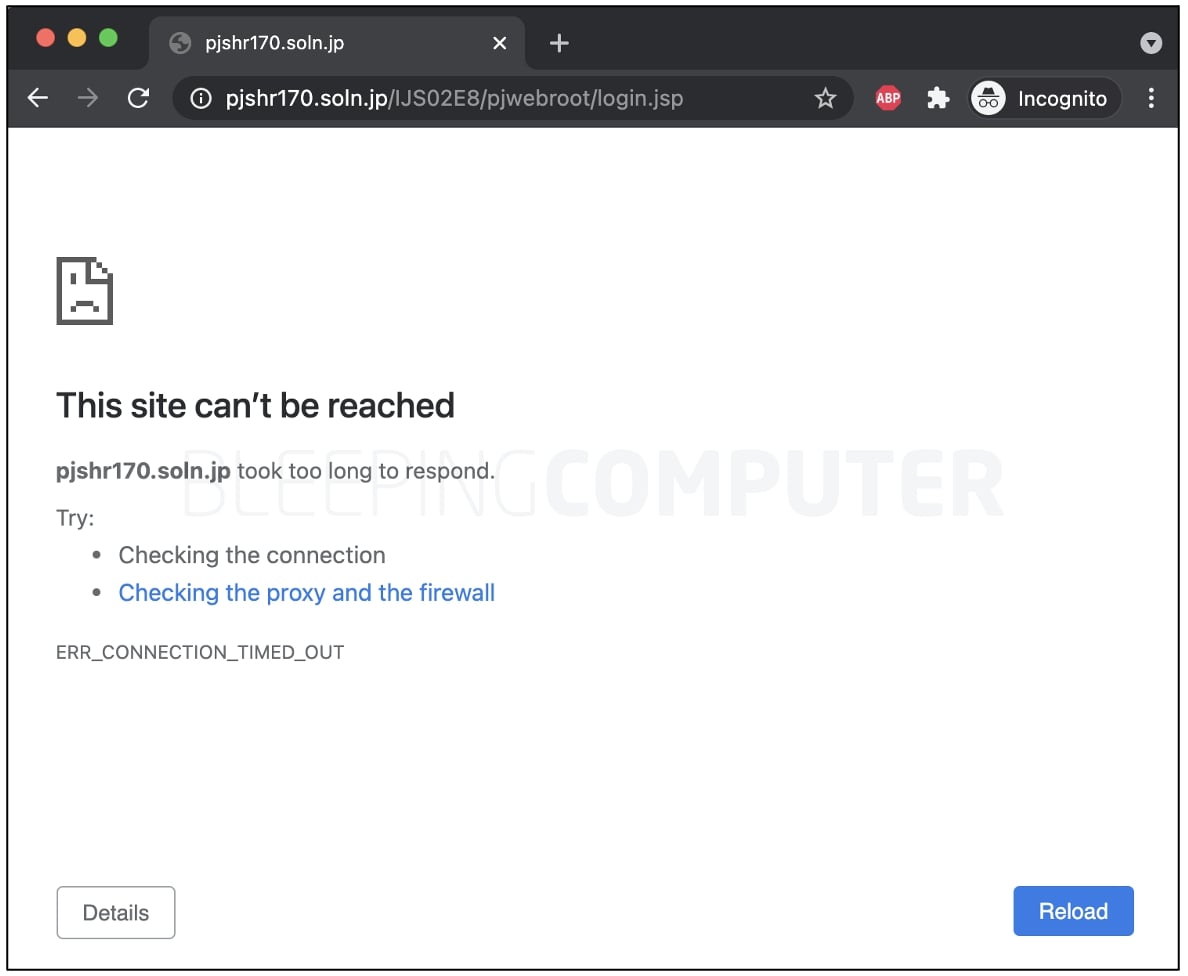 Fujitsu ProjectWEB portal shut down after the breach
Fujitsu ProjectWEB portal shut down after the breachSource: BleepingComputer
Since the ProjectWEB portal was hosted on the "soln.jp" domain, one way to check if your organization has been impacted, or was a customer at some point, is to look for traces of the domain or the aforementioned URL in your network logs.
Fujitsu states they will be notifying the relevant authorities and work with their customers to identify the cause of the breach, in a press release.
Although disclosure of technical details behind this attack is pending, the incident has echoes of the Accellion file sharing tool hack which impacted hundreds of customer organizations.
BleepingComputer has reached out to Fujitsu with some questions before publishing and we are awaiting their response.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·