BOOK THIS SPACE FOR AD
ARTICLE ADFirst of all, I want to clarify that I am not fluent in English, so mistakes will happen during the reading :) If tou have some question dm me on
Twitter
Hey, what’s up?
In this article I will explain a little trick to exploit CSRF in Json applications.
Some people think that because they are using json applications they are exempt from CSRF attacks, but it’s not totally truly, in some cases you can exploit then.
How to exploit?
Ok, now i’m going to show how to exploit it.
In this example I will use this request as example:
This request simulate a reset password feature.
{
“user”:{
“password”:”Nice_Passw0rd”,
“password_confirmation”:”Nice_Passw0rd”
}
}
How to forge a json request using html forms?
Not everything is the way we want it, when we are going to create Json requests from an HTML form we are limited to using GET and POST methods and we can’t use enctype=application/json. :/
So in this case we are going to use “POST” method and “text/plain” enctype.
Now, after understanding the limitations we can create an exploit.html file.

We can see in line 10 that the name of form is the bulk of the payload, and the “value” field is just the end. Ok, let’s intercept the request.

We can see that the request is relatively broken. There is an equal sign before the value of the value parameter. It’s occours beacuse the correct sintax is name=value.
To bypass it we need to add an another field to the request.
The final exploit looked like this.
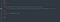
Was added “a” field in the request.
The final request looked like this.

We can note that the “=” was added as key value in the request.
We can note that exploit JSON CSRF token is relatively limited, but in some cases it works fine :)
Thanks for reading, if you have any question dm on twitter.
.png)
 3 years ago
185
3 years ago
185 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·