BOOK THIS SPACE FOR AD
ARTICLE ADAnyone involved in or even significantly interested in cybersecurity has probably heard of Kali Linux. Since its early days as BackTrack, it has been considered the standard in penetration testing and security analysis platforms. In my opinion, it also happens to be one of the best Debian GNU/Linux distributions available.
SEE: An IT pro's guide to robotic process automation (free PDF) (TechRepublic)
It is based on Debian stable (currently 10/buster), but with a much more current Linux kernel (currently 5.9 in Kali, compared to 4.19 in Debian stable and 5.10 in Debian testing).

Kali Linux 2020.4 with Xfce desktop.
Image: J.A. Watson
Kali is available for installation in a number of different formats, for a number of different systems, and that variety can sometimes be a bit intimidating. So I am going to run down some of the possibilities, in hopes of clearing it up a bit.
The installation images available on the Kali Downloads page are:
32-bit (i386) and 64-bit (amd64) versions: Some distributions have dropped 32-bit support, but not KaliFull Installer: This is a slightly modified version of the Debian GNU/Linux installer. Yes, I can hear a lot of users out there going "Ugh". It is a very old installer, primarily text-based, with no spiffy GUI interface. But the important thing is that it does the job very, very well in almost every situation and on almost every kind of system, without having to worry about graphic adapters, display resolution or much of anything else. The basic "Installer" is text-only, and the "Graphic Installer" is the same thing with mouse support added (but still no other graphics or GUI). The installation image includes the complete Kali system, so it can be installed without having an Internet connection. It weighs in at just over 4GB.NetInstaller: This is the same installation program as the full installer, but the downloaded image includes only enough to get the computer booted and connected to the Internet, and the rest of the packages are downloaded as needed during installation. It is a very svelte 471MB.Live: This is a bootable image that can be run from the USB stick (or DVD). As with other Linux Live distributions, you can use it to check that your hardware works properly with Kali Linux, but you can go even further than that. When it is copied to a USB stick, you can add a partition for "persistence", where data created or modified while running the Live image will be saved across shutdown and rebooting – and that persistence data can even be encrypted. So you can use the USB stick as a conveniently portable Kali Linux platform.
Virtual Images for VMware and VirtualBox: Just download and import the image, and you're ready to go.ARM Images: Tailored and tested images for the Raspberry Pi, Pine 64, ODROID and others. Download the image, copy it to appropriate media, and it's ready to go.
Each of the download links is accompanied by the SHA256 checksum for that image. Be SURE to validate the checksum before installing the image!
Full Installer / NetInstaller
As mentioned above, the only difference between these two is where the installer gets the packages from, so the following description applies equally to either one.
After booting the installation medium, you are presented with a series of screens:
 Image: J.A. Watson
Image: J.A. Watson

Network ConfigurationUser Account creation
Disk PartitioningSystem Software selection
Please be aware that after you complete software selection, the installer immediately begins installation. There is no "last chance / are you sure" prompt!
I have included a screen shot of the Software Selection step to show what these "text-based" screens look like, and because I find this particular screen interesting and amusing. First (interesting) the default desktop is Xfce, but if you prefer Gnome 3 or KDE Plasma, you may select them here (I still wish they would offer the i3 desktop here...). Second (amusing) the "Kali Software" options include "Collection of tools (selecting this item has no effect)". Huh? Hmmm... Well... Does not selecting this item have any effect? I don't know... Anyway, you can get just a bare-bones Debian system by clearing the "top-10", "default" and "large" choices.
SEE: Raspberry Pi 400: Its designer reveals more about the faster Pi 4 in the $70 PC's keyboard
One other interesting note. Kali uses only their own repositories, and they do not have the Debian concept of OSS and Non-Free packages. But this hasn't been entirely removed from the installer dialog, because if your system has a wireless network adapter which requires non-free firmware (such as the Intel wireless adapters), the installer will ask you if you want to install them from a separate medium, but if you simply say no, when the installation completes the drivers will be installed and wireless networking will be working.
One very significant change that Kali made not long ago was to stop using the root login with a well-known default password (hooray!), and actually disabling login to the root account, so you have to login to the account you created during the installation, and then use sudo to execute privileged commands.
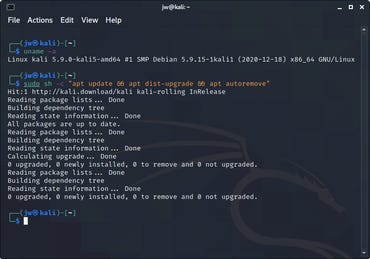 Image: J.A. Watson
Image: J.A. Watson

Also, Kali recently changed to using the zsh command interpreter by default, rather than bash. Long-time Linux (and Unix) users like me might find this disconcerting at first, and of course if you know enough for it to bother you, then you certainly know enough to change it back (bash is also included in the base installation), but give zsh a chance and you will probably like it – or at least not be disturbed by it. As one of my students once said to me, "It's time to join the 21st century".
If you use the NetInstaller, when the installation is complete your system will be up to date (because it installs from the latest packages in the Kali repository). If you use the stand-alone Installer, when you boot the installed system you will need to install the latest updates. The command that I use to get everything done at once is:
sudo sh -c "apt update && apt dist-upgrade && apt autoremove"
This simply combines the three necessary commands (update the package list, install all upgrades and remove unused packages) in a single command line, which makes it easy to repeat from the command history list when necessary.
Live System
The Kali Live download is an ISO image which can be written to a USB stick or DVD, and you can then boot that medium and run a full Kali Linux system from it without disturbing whatever is currently installed on the disk drive. When you boot this image, there are a number of boot options:
Live SystemLive System (fail safe mode)Live System (forensic mode)Live System (persistence)Live System (encrypted persistence)InstallerInstaller (with speech synthesis)The "forensic mode" boot is basically a normal "Live System" boot with just a couple of significant changes related to the way that it uses disk drives. First, it never touches any disk drive other than the USB stick in any way. That means it doesn't auto-mount any partition of an internal drive, and if there is a swap partition on the internal drive it is not used. The idea here is that you don't have to worry about accidentally modifying or corrupting the drive, and you don't have to worry about anything from the internal drive modifying, infiltrating or otherwise affecting the operation of your Kali Live operation. Second, auto-mounting of all removable media is disabled. This includes USB drives, CD and DVD drives, Zip drives and anything else. Again, the idea is the same – nothing gets mounted, modified, or accessed in any way unless you, the user, specifically command it. Forensic mode has a long history with Kali (and BackTrack Linux), and I know that a lot of cybersecurity professionals always boot this mode.
The "persistence" options are useful if you plan to work from the USB stick repeatedly, as it allows you to store information that will not be lost when you reboot. Even though this option is included in the standard boot list, this does not "just work" after you have created the Live USB stick. If you do nothing else and then just boot persistence mode, what you will get is actually just the normal Live boot, with no extra features, no persistent storage of files, and no error messages telling you that you aren't getting what you probably expected.
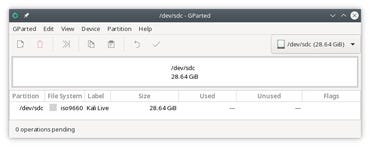
gparted view of a Kali Live USB stick.
Image: J.A. Watson
To actually use persistence mode, you have to carefully follow the instructions given on the web page Adding Persistence to a Kali Linux "Live" USB Drive. This will walk you through creating, formatting and labeling another partition on the USB stick, and configuring it so that it is overlaid on the Live filesystem.
This process can be a bit confusing, especially if you aren't familiar with dealing with ISO filesystems. The Kali Live image actually creates two partitions on the USB drive, one for the UEFI boot partition and one for the Linux root partition. But some Linux tools, most notably the gparted utility, don't understand this and they simply show the entire device as one large ISO block which you can't modify (or add to) in any way.
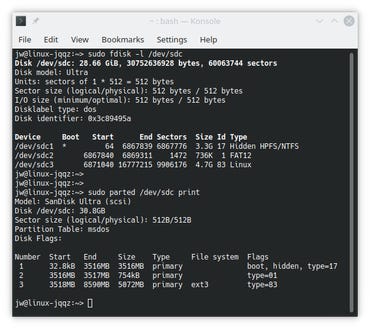
parted and fdisk views of a Kali Live USB stick
Image: J.A. Watson
The Linux utilities used in the Adding Persistence instructions are able to read and modify the USB stick, as shown here. One other tip – in the parted command to create the persistence partition, the end value that you give is where the actual end of the new partition will be on the disk, not the size of the new partition. So using the example command given in the document, with end=7GiB, you will actually create a partition about 4GB in size (because the Kali Live system is already using about the first 3GB of the drive). That surprised me at first.
You can also install Kali Linux from the Live system image, in much the same way that it is installed from the previously described full Installer and NetInstaller images, by simply choosing one of the Installer options from the boot menu. I have also read that it should be possible to install from a running Live image by first installing the Calamares utility (sudo apt install calamares), but I have not tried this myself, and I honestly wouldn't recommend it.
One last tip about the Live System. It normally boots directly to the Kali desktop, so you don't actually have to login. This sometimes leads to a trap because you don't actually know your current account credentials. If you get into a situation where you need them, for example by logging out or if the screen lock activates, the default credentials are kali/kali.
Virtual Images
If you already have VirtualBox or VMware installed, then this is probably the fastest/easiest was to get Kali Linux running. Both 32-bit and 64-bit images are available on the Kali Linux Custom Image Downloads web page. Just download the image, import it into your VM management utility, and you're ready to go.
SEE: Hands-On: Adventures with Ubuntu Linux on the Raspberry Pi 4
It is important to note that these images are provided on a "best effort" basis, which means that although they are likely to work, they may occasionally have temporary problems, and they may not be kept up to date as well as the normal installer images are. My experience with the Virtual Box images has been that they are generally good, but on one occasion last year they actually had a problem that caused them to fail to boot, even though they were downloaded successfully and the checksum validated. This was particularly unfortunate because some of my students wanted to use Kali on VirtualBox for an assignment, and it was quite a while before that download image was fixed. So I would not recommend building a critical system on these images.
Raspberry Pi Installation
I covered this in detail in my recent post Hands-On: Kali Linux on the Raspberry Pi 4. Basically you just download the Kali Linux ARM Image for the Raspberry Pi, copy it to a microSD card, and you're ready to go. You don't have to go through the installer dialog described above, but that means if you actually need to change any of those things (user account, keyboard layout, time zone, disk partitioning and such) you have to use the normal Raspberry Pi OS (Linux) utilities to do so. What you end up with is a Kali system with the top10 group of tools installed, and account login credentials of kali/kali.
Summary
So that's the high points. I have personally had Kali installed on my desktop, laptops, netbooks, Raspberry Pi 2-4 and 400, on Live USB sticks and in VirtualBox. Installation is not at all difficult, and it is an unbeatable penetration testing and security analysis platform. I strongly recommend it. If you are interested in learning about Linux installation and management, as well as penetration testing and security analysis, their reference book Kali Linux Revealed is excellent – and it is available as a PDF via the preceding link, or in paperback.
.png)
 3 years ago
122
3 years ago
122 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·