BOOK THIS SPACE FOR AD
ARTICLE AD
On Wednesday, the KDE team warned Linux users to exercise "extreme caution" when installing global themes, even from the official KDE Store, because these themes run arbitrary code on devices to customize the desktop's appearance.
The KDE Store currently allows anyone to upload new themes and various other plugins or add-ons without any checks for malicious behavior.
However, as KDE said, it currently lacks the resources to review the code used by each global theme submitted for inclusion in its official store. If the themes are faulty or malicious, this can result in unexpected consequences.
"Global themes and widgets created by 3rd party developers for Plasma can and will run arbitrary code. You are encouraged to exercise extreme caution when using these products," KDE cautioned.
"Global themes do not only change the look of Plasma, but also the behavior. To do this they run code, and this code can be faulty, as in the case mentioned above. The same goes for widgets and plasmoids."
Code execution is needed because global themes are designed to change everything on a Plasma desktop, from icons to windows decorations, lock screens, splash screens, wallpapers, color schemes, and so on, using executable bash scripts.
Global theme wipes user's files using 'rm -rf'
According to a Reddit post quoted by KDE, at least one user had their files wiped after installing one such global Plasma theme.
After it was installed, the theme deleted all personal data from mounted drives using 'rm -rf', a very dangerous UNIX command that forcefully and recursively deletes a directory's contents (including files and other folders) without any warnings and prompting for confirmation.
When this command is used to delete files, they are permanently wiped and can only be recovered using data recovery software or restored from backups.
While the faulty global theme has since been removed from KDE's store, any other global themes available through KDE's official plugin repository could cause data loss if the developers haven't thoroughly tested them before submission.
"It executes rm -rf on your behalf [and] deletes all personal data immediately. No questions asked," the KDE user warned. "I canceled this when it asked for my root password, but it was too late for my personal data. All drives mounted under my user were gone, down to 0 bytes. [G]ames, configurations, browser data, [and the] home folder [are] all gone."
"Then it threw some sort of error, [and] my plasma kind of got stuck. [T]hen I checked and my two hard-drives were fully erased, games, configurations, personal data, all gone. Any drive mounted with user permissions also wiped out," the user added in a separate Reddit post.
KDE promises to start vetting store content
In light of the risks behind installing unvetted Plasma plugins, KDE asked the community to report faulty software already available through the KDE Store.
The team also promised to curate store content and improve the warnings shown to users before installing community-developed themes and plugins on their systems.
"[W]e need to communicate clearly what security expectations Plasma users should have for extensions they download onto their desktops," said David Edmundson, a Software Engineer and Project Lead at KDE. "Then, we can look at providing curation and auditing as part of the store process in combination with slowly improving sandbox support."
"If you install content from the store, I would advise checking it locally or looking for reviews from trusted sources."
"Nevertheless, this will take time and resources. We recommend all users to be careful when installing and running software not provided directly by KDE or your distros," the KDE team added.
Until then, users will still be warned when installing global themes from the KDE system settings: "The content available here has been uploaded by users like you and has not been reviewed by your distributor for functionality or stability."
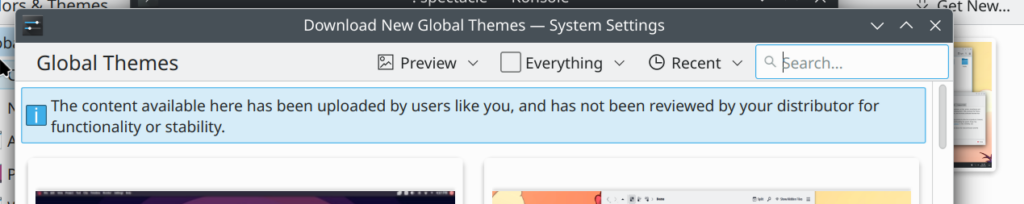 Warning before installing a global theme in KDE (David Edmundson)
Warning before installing a global theme in KDE (David Edmundson).png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·