BOOK THIS SPACE FOR AD
ARTICLE ADLapsus$ added IT giant Globant plus 70GB of leaked data – including admin credentials for scads of customers’ DevOps platforms – to its hit list.
The Lapsus$ data extortionists are back from a week-long “vacation,” they announced on Telegram, posting ~70GB worth of data purportedly stolen from software development giant Globant.
“We are officially back from a vacation,” the gang wrote on their Telegram channel, posting images of exfiltrated data and admin credentials. The credentials, purportedly belonging to Globant’s customers, unlock several of the company’s Atlassian suite DevOps platforms, including GitHub, Jira, Confluence and the Crucible code-review tool.
The shared, 70GB torrent file purportedly also contains Globant’s source code, as well as the Atlassian admin passwords. Security researchers shared the images today, on Wednesday.
Screenshots show a folder directory of what looks like scads of companies from across the world, including tech bigwigs Arcserve, Facebook, the Apple Health app, DHL, Citibank, BNP Paribas Cardiff and Citibanamex, among others: just a teaser of the Globant data Lapsus$ has promised to leak.
This is bad with all the keys, codes and damaging databases to go through to find corporate exposure and liability and to secure digital assets. https://t.co/FHcs88V3nM
— Dominic Alvieri (@AlvieriD) March 30, 2022
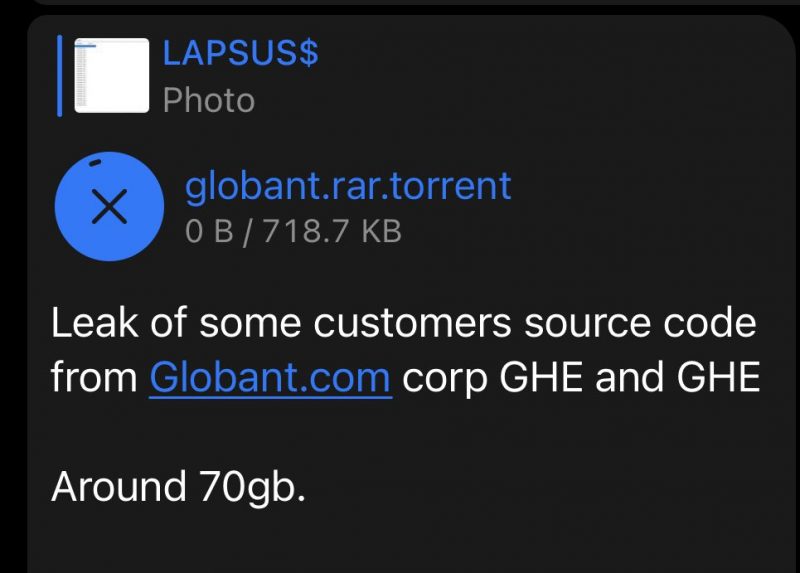
The folders could be evidence of client data having been exposed, or they might just refer to Globant backups. But Lapsus$ followed up by posting a 718.8KB torrent file to Telegram – a file that allegedly contains the leaked data. The post says: “Leak of some customers source code from Globant[.]com corp GHE and GHE.”
But as GovInfoSecurity pointed out, even if Globant’s source code wasn’t directly affected, the source code of the software it provides to its customers may be.
About Those Admin Credentials
Vx-underground – an internet collection of malware source code, samples and papers – cited security researcher Dominic Alvieri in tweeting that Lapsus$ threw Globant’s sysadmins “under the bus” by exposing their passwords to Confluence and other DevOps platforms.
That shouldn’t come as a surprise: It’s not like the data extortion group has a collection of kid gloves. It has, rather, slapped around the likes of Brazil’s Ministry of Health, the gaming giant Ubisoft, Portuguese media kingpin Impresa, and, in recent weeks, eviscerated tech giants including Samsung, Nvidia, Microsoft and Okta.
Vx-underground censored those admin passwords, but its whiteout treatment can’t hide the fact that the passwords were pretty stubby and, hence, pretty guessable, as well as being reused. “We have censored the passwords they displayed. However, it should be noted these passwords are very easily guessable and used multiple times,” the collection noted.
LAPSUS$ also threw their System Admins under the bus exposing their passwords to confluence (among other things). We have censored the passwords they displayed. However, it should be noted these passwords are very easily guessable and used multiple times… pic.twitter.com/gT7skg9mDw
— vx-underground (@vxunderground) March 30, 2022
In fact, after reviewing the admin passwords, GovInfoSecurity found that a similar-looking password was reused for the Confluence and Jira platforms, while the one used for GitHub “appears similar to ones on the list of 200 most commonly used passwords.”
So Much for the Arrests
Lapsus$’s “vacation” may have been in Tahiti, for all we know, or it may have been time spent reshuffling. At any rate, last week, the City of London Police arrested seven people suspected of being connected to the gang.
The bust came within hours of Bloomberg having published a report about a teenage boy living at his mother’s house near Oxford, England who’s suspected of being the Lapsus$ mastermind. The police didn’t verify whether or not they nabbed the Oxford teen, per se, but given that he’s a minor, they legally couldn’t divulge that detail anyway.
All of the suspects arrested by London police were released, but the law isn’t going to let up.
As of a week ago, March 21, the FBI had slapped Lapsus$ onto its Most Wanted list.
“On March 21, 2022, individuals from a group identifying themselves as Lapsus$ posted on a social media platform and alleged to have stolen source code from a number of United States-based technology companies,” the FBI said. “These unidentified individuals took credit for both the theft and dissemination of proprietary data that they claim to have illegally obtained. The FBI is seeking information regarding the identities of the individuals responsible for these cyber intrusions.”
Ken Westin, director, security strategy at Cybereason, told Threatpost on Wednesday that Lapsus$’s quick resurface after its short hiatus isn’t surprising, given the fact that cybercriminal networks are often spread around the world.
“Cybercrime groups, like hacktivist groups, often work in a decentralized fashion, with many members not even knowing each other’s true identities,” he said via email. “The fact this group is made up of members in many different countries presents challenges for law enforcement as they will need to collaborate with different countries with varying levels of capabilities to go after the perpetrators.”
Westin noted that the Globant breach “seems a bit different on the surface,” given that the resources that were allegedly compromised were around Globant’s DevOps processes. It raises the question of where the initial compromise was and what Lapsus$ did with the access. Wha”t is also concerning regarding this compromise is that potential source code for some of their customers appears to have been exposed and Lapsus$ is going after organizations via Globant’s technology and now services partners,” he added.
033022 12:40 UPDATE: Added input from Ken Westin.
Moving to the cloud? Discover emerging cloud-security threats along with solid advice for how to defend your assets with our FREE downloadable eBook, “Cloud Security: The Forecast for 2022.” We explore organizations’ top risks and challenges, best practices for defense, and advice for security success in such a dynamic computing environment, including handy checklists.
.png)

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·