BOOK THIS SPACE FOR AD
ARTICLE ADVulnerability management continues to challenge businesses, as they face tens of thousands of bugs with every scan.
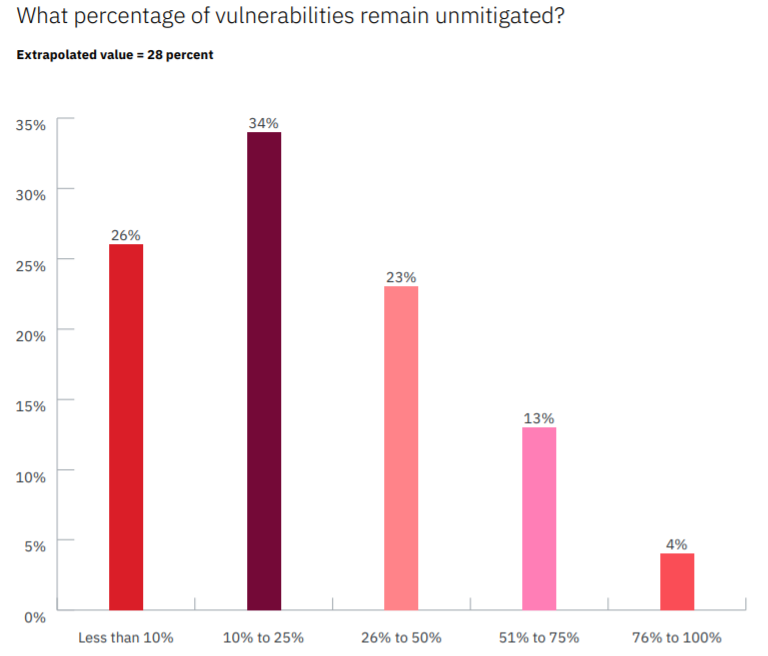
Large companies find an average of 779,935 individual security bugs when running routine vulnerability scans; and over the course of six months, an average of 28 percent of those vulnerabilities will remain unmitigated. This leaves many of these organizations in a sitting-duck position for cybercriminals, rearchers said.
That’s according a study from the Ponemon Institute, The State of Vulnerability Management, which surveyed 1,800+ IT professionals at companies with more than 1,000 employees. The survey found that the average backlog of bugs for these companies totals a whopping 57,555 identified vulnerabilities.
Clearly, prioritization becomes critical to vulnerability management in this scenario; however, the survey also found that organizations have difficulty in achieving that. A full 57 percent of respondents said their organizations don’t know which vulnerabilities pose the highest risk to their businesses.
And only a quarter (25 percent) said they’re able to prioritize patching based on which assets are the most important to the business.
About 37 percent of respondents said their primary method for prioritization is the identification of which vulnerabilities are weaponized. This isn’t a bad strategy on the surface given that criminal external attacks were the most common cited root cause of data breaches in the survey (34 percent). External attacks were followed by human error (24 percent), and system glitches and malicious insider threats accounted for the rest.
“Even if they prioritize vulnerabilities accurately, the process of remediation can become a headache as teams try to process the information — who owns the vulnerable asset, is there a patch, what if the patch doesn’t work, when is an appropriate time for patching, etc.,” explained researchers from IBM X-Force, in the report, released Monday. They added, “Every enterprise has an immense amount of data, much of which is siloed, giving each team a different perspective of risk. The fragmented viewpoints prevent seeing the full risk picture, which can also lead to important vulnerabilities being deprioritized or overlooked.”
Only 21 percent of respondents said their organizations are “highly effective” in patching vulnerabilities in a timely manner. According to the research, it can take almost a month (28 days) to patch once a critical or high-risk vulnerability is detected on-premises, and 19 days if it is detected in the cloud.
All of this leaves a broad swath of businesses at risk for compromise from known bugs. And in fact, out of the 53 percent of respondents who said their organizations have had a data breach in the past two years, 42 percent of them said they occurred because a patch wasn’t applied for a known vulnerability.
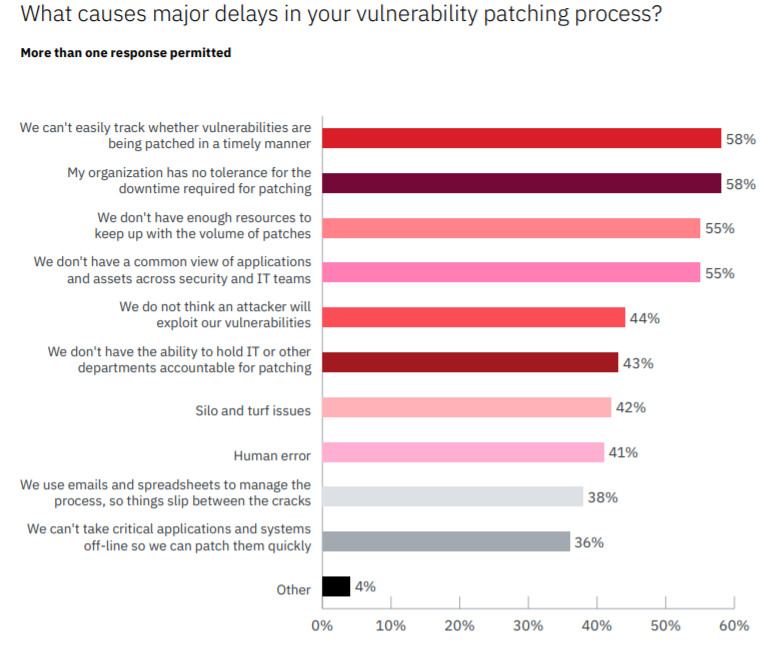
As to the obstacles to getting on top of vulnerability management, Ponemon found that the use of manual processes for patching remains a bugbear. Half of respondents said their organizations are at a disadvantage in responding to vulnerabilities because they use manual processes; and more than half (53 percent) said that IT staff spends more time navigating manual processes than responding to vulnerabilities.
Also, the survey uncovered that most organizations do not have a single view of the full vulnerability management lifecycle, including exception handling. Only 27 percent of respondents say they have visibility into the vulnerability management lifecycle, making it difficult to ascertain how well their organizations are prioritizing, remediating and patching vulnerabilities.
Then there’s the issue of staffing and the ongoing cybersecurity skills gap: Only about half (49 percent) of respondents said their organizations have enough personnel to patch in a timely manner, while just 41 percent said the IT security team has the necessary patching skills and training to fix vulnerabilities.
“Instead of taking a programmatic approach to vulnerability management, many organizations take an anecdotal approach,” according to X-Force. “They divvy up and plow through an Excel spreadsheet, which may contain thousands to millions of vulnerabilities. The spreadsheet method may work for one team in the organization, but when it’s rolled out across an entire enterprise, chaos can ensue.”
Cloud Issues
Against this general backdrop, the Ponemon survey also found that organizations face special challenges when storing business-critical applications in containers in the cloud (on average, 38 percent of mission-critical applications are in containers).
Of those respondents that have those applications in the cloud, 56 percent said they’re uncertain as to whether the applications in the containers were tested to find and fix high-risk vulnerabilities that an attacker may exploit.
And yet, only 38 percent of respondents said identifying vulnerabilities in cloud environments is more difficult and complex than identifying vulnerabilities on-premises. And 35 percent of respondents said patching in the cloud is more difficult and complex than on-premises.
“Organizations tend to have different teams and policies when it comes to cloud security versus on-premises security,” according to X-Force in the report. “Because the cloud footprint can expand so rapidly and have a different governance structure, the cloud security teams are drowning. Often, when applications are moved into the cloud environment, they do not receive the same level of attention — less frequent penetration testing, vulnerability scanning, etc.”
It’s the age of remote working, and businesses are facing new and bigger cyber-risks – whether it’s collaboration platforms in the crosshairs, evolving insider threats or issues with locking down a much broader footprint. Find out how to address these new cybersecurity realities with our complimentary Threatpost eBook, 2020 in Security: Four Stories from the New Threat Landscape, presented in conjunction with Forcepoint. We redefine “secure” in a work-from-home world and offer compelling real-world best practices. Click here to download our eBook now.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·