BOOK THIS SPACE FOR AD
ARTICLE ADWe take a look at the latest additions to security researchers’ armory

The early months of 2022 are behind us and, as security professional prepare for the upcoming conference season, it’s high time to load up the security tools arsenal.
During the dark and dank northern hemisphere winter security researchers have been hard at work putting together a stockpile of new tools and utilities – many of which have been released as open source software.
So, without further ado, here’s our latest quarterly round-up of hacking tools available to pen testers, enterprise security specialists, and other infosec professionals at the start of the second quarter of 2022.
Lab environment for learning about API security

A test platform designed to help users learn about API security has been released to the open source community.
API security has moved to the frontline in the fight to improve enterprise web security over recent years.
vAPI, also known as the ‘Vulnerable Adversely Programmed Interface’, is designed to showcase OWASP’s API Top Ten, creating a safe environment to observe their behaviors.
Developed by researchers at Holm Security, vAPI offers an open source, PHP-based interface, available on GitHub, which can run as a self-hosted API through PHP, MySQL, and PostMan, or as a Docker image.
Read more about the vAPI API security test platform
Non-commercial phishing email analysis tool

A non-commercial tool which automates the process of analyzing phishing emails has the potential to help organizations systematically safeguard themselves against scams.
ThePhish extracts indicators from suspect emails including IP addresses, email addresses, domains, URLs, and file attachments. This information is fed into Cortex, an active response engine.
The tool, put together by Emanuele Galdi, a researcher at Italian cybersecurity firm SecSI, integrates with the incident response platform, TheHive. Positive results obtained by ThePhish are exchanged through the Malware Information Sharing Platform (MISP).
Read more about The Phish scam email analysis tool
Fuzzing tool to speed up testing of network applications

A prototype tool to speed up the process of testing networking applications and protocols has been developed by researchers from Imperial College, London.
SnapFuzz is designed to overcome timing constraints that can inhibit the process of putting network applications through their paces.
As a fuzzing framework, it tries a wide variety of input values and monitors the output for anomalies that can reveal potential bugs.
Read more about the SnapFuzz network application testing tool
Protecting JavaScript applications from malicious NPM packages

The task of shielding applications from the instruction of malicious packages may be eased with the introduction of three bespoke utilities.
The tools – npm-secure-install, package-checker, and npm_issues_statistic – are designed to validate whether package versions can be trusted as well as monitoring applications for the inclusion of problematic dependencies.
The genesis for the utilities’ development by software firm JFrog came from a recent incident in which a developer intentionally made changes to two NPM packages, hobbling these apps and disrupting any application that depended on them as a result.
Read more about JFrog’s NPM security tools
Uncover a weak-text-redaction decloaking tool
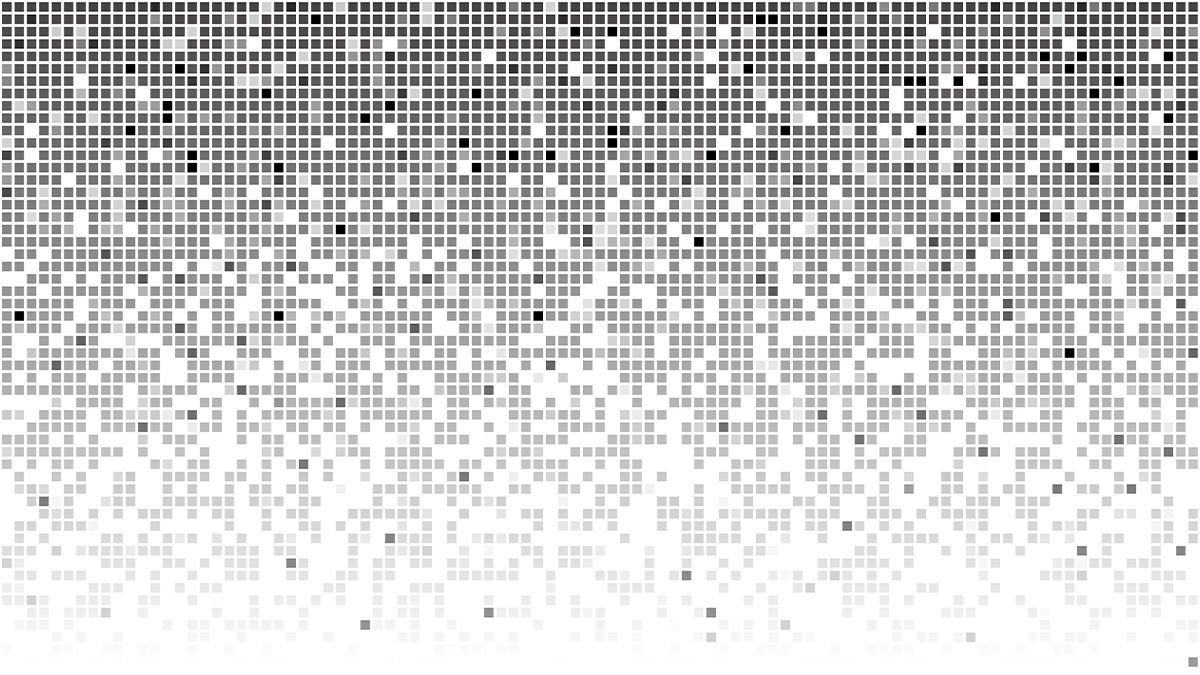
Anyone who thought that pixelating text offers an effective method to obscure or redact content will have their illusions dispelled by a new hacking tool.
Unreadctor is able to take redacted pixelized text and uncover the ‘clear text’ the flimsy security technique is supposed to hide.
Develops Bishop Fox said that the tool demonstrates that pixilation is “a no-good, bad, insecure, surefire way to get your sensitive data leaked”.
Read more about the Unreadctor weak redaction uncloaking tool
AWS utility protects against dangling elastic IP takeovers

Answering the question ‘who are you going to call?’ to deal with a troublesome class of AWS security problems comes Ghostbuster.
Ghostbuster, a tool developed by Australian cybersecurity firm Assetnote, enumerates all public IPs associated with an organization’s AWS accounts before checking with DNS records that point towards elastic IPs that an organization doesn’t own.
The approach offers a “foolproof way” of detecting dangling elastic IP takeovers, a class of subdomain takeover attack.
As well as hosting malicious content or leveraging a ‘trusted’ domain for phishing attacks, attackers might attempt to use the tactic in bids to claim a subdomain’s SSL certificates and other such shenanigans.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·