BOOK THIS SPACE FOR AD
ARTICLE ADThe North Korean-linked APT’s latest campaign shows that it is shifting focus to target the cryptocurrency and financial verticals.
The nation-state threat operator Lazarus Group is being tied to a recent phishing campaign that targeted admins at a cryptocurrency firm via LinkedIn messages.
Researchers say that the recently identified a series of incident that were part of a broader campaign targeting businesses worldwide through LinkedIn messages sent to targets’ personal LinkedIn accounts. The goal of the campaign appears to be financially motivated, with the attackers harvesting credentials necessary for accessing cryptocurrency wallets or online bank accounts.
“Lazarus Group’s activities are a continued threat: the phishing campaign associated with this attack has been observed continuing into 2020, raising the need for awareness and ongoing vigilance amongst organizations operating in the targeted verticals,” said researchers with F-Secure in a Tuesday post [PDF].
The attackers targeted system administrators in an unnamed cryptocurrency company with a phishing document, which was attached to a message sent to their personal LinkedIn accounts. The document masqueraded as a legitimate job advertisement for a role in a blockchain technology company, which matched the employee’s skills, researchers said.
Once the target clicked on the malicious document, the document claimed to be protected by General Data Protection Regulation (GDPR) restrictions, and that the user needed to enable macros in Microsoft Word for further access. Once the target enabled the macros, malicious embedded macro code would then execute. The macro in the document creates an LNK file that results in the execution of mshta.exe.
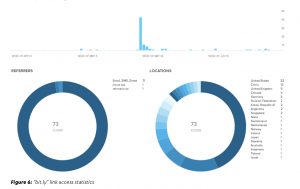
This then calls out to a “bit.ly” link created in early May 2019, researchers said. Upon further inspection of the link used in the phishing attack, researchers found that it was accessed 73 times from at least 19 countries – including the U.S., China and the UK – leading researchers to conclude that this is a “widely-targeted lure document.”
The “bit.ly” link then redirects to a domain that executes a VBScript to perform checks on the host and collect further information, which is then sent to a second Command and Control (C2) domain. This eventually leads to the download and execution of a PowerShell script that retrieves a further payload from a third C2, researchers said.
 This payload finally downloads several main implants on the victim’s system, which contain the abilities to download additional files, decompress data in memory, initiate C2 communication, execute arbitrary commands, and steal credentials from a number of sources (via a custom version of Mimikatz; an open-source application that allows users to view and save authentication credentials). The implants were also observed being used to connect to the network backdoor implants on other target hosts, researchers said.
This payload finally downloads several main implants on the victim’s system, which contain the abilities to download additional files, decompress data in memory, initiate C2 communication, execute arbitrary commands, and steal credentials from a number of sources (via a custom version of Mimikatz; an open-source application that allows users to view and save authentication credentials). The implants were also observed being used to connect to the network backdoor implants on other target hosts, researchers said.
Researchers also made note of various tactics utilized by the APT to avoid detection. For instance, Lazarus Group disabled Windows Defender monitoring as one of their first actions on each host they accessed. Despite these attempts to avoid detection, researchers note that the large number of commands executed through cmd.exe give blue teams “significant opportunities for detection.”
“One distinctive trait common across the majority of the commands executed by Lazarus Group was the appending of the string “2>&1″ to commands; which whilst used by some tooling should be anomalous when filtered by parent child process relationship, and provide good detection opportunities,” they said.
Shift to Cryptocurrency
Lazarus Group, a.k.a. Hidden Cobra or APT 38, has been around since 2009. The APT has been linked to the highly destructive WannaCry attack that caused millions of dollars of economic damage in 2017, the SWIFT banking attacks, as well as the high-profile attack against Sony Pictures Entertainment in 2014. Lazarus is also constantly evolving: In December, it was seen hooking up with Trickbot operators, which run a powerful trojan that targets U.S. banks and others. In May, it was seen adding macOS spyware to a two-factor authentication app; and earlier in July, it added Magecart card-skimming code to its toolbag.
More recently it has debuted an advanced, multi-purpose malware framework (MATA) that targets Windows, Linux and MacOS operating systems; and has been linked to a recent strain of ransomware, called VHD.
However, this most recent campaign shows that the group is now also looking to target organizations in the financial and cryptocurrency verticals, researchers warn.
“It is F-Secure’s assessment that the group will continue to target organizations within the cryptocurrency vertical while it remains such a profitable pursuit, but may also expand to target supply chain elements of the vertical to increase returns and longevity of the campaign,” said researchers.
It’s the age of remote working, and businesses are facing new and bigger cyber-risks – whether it’s collaboration platforms in the crosshairs, evolving insider threats or issues with locking down a much broader footprint. Find out how to address these new cybersecurity realities with our complimentary Threatpost eBook, 2020 in Security: Four Stories from the New Threat Landscape, presented in conjunction with Forcepoint. We redefine “secure” in a work-from-home world and offer compelling real-world best practices. Click here to download our eBook now.
.png)

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·