I am sure that many of you have by now heard of a recently disclosed critical Windows server vulnerability—called Zerologon—that could let hackers completely take over enterprise networks.
For those unaware, in brief, all supported versions of the Windows Server operating systems are vulnerable to a critical privilege escalation bug that resides in the Netlogon Remote Control Protocol for Domain Controllers.
In other words, the underlying vulnerability (CVE-2020-1472) could be exploited by an attacker to compromise Active Directory services, and eventually, the Windows domain without requiring any authentication.
What's worse is that a proof-of-concept exploit for this flaw was released to the public last week, and immediately after, attackers started exploiting the weakness against unpatched systems in the wild.
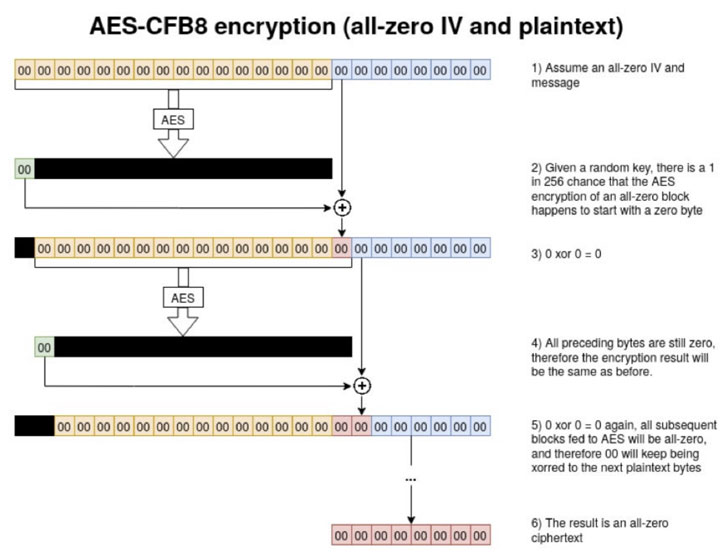
As described in our coverage based on a technical analysis published by Cynet security researchers, the underlying issue is Microsoft's implementation of AES-CFB8, where it failed to use unique, random salts for these Netlogon messages.
The attacker needs to send a specially crafted string of zeros in Netlogon messages to change the domain controller's password stored in the Active Directory.
For THN readers willing to learn more about this threat in detail, including technical information, mitigations, and detection techniques, they should join a live webinar (register here) with Aviad Hasnis, CTO at Cynet.
The free cybersecurity educational webinar is scheduled for September 30th at 5:00 PM GMT, and also aims to discuss exploits deployed in the wild to take advantage of this vulnerability.
Besides this, the Cynet team has also released a free detection tool that alerts you to any Zerologon exploitation in your environment.
Register for the live webinar here.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 4 years ago
182
4 years ago
182 















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·