BOOK THIS SPACE FOR AD
ARTICLE ADThe LockBit ransomware gang has created encryptors targeting Macs for the first time, likely becoming the first major ransomware operation to ever specifically target macOS.
The new ransomware encryptors were discovered by cybersecurity researcher MalwareHunterTeam who found a ZIP archive on VirusTotal that contained what appears to be all of the available LockBit encryptors.
Historically, the LockBit operation uses encryptors designed for attacks on Windows, Linux, and VMware ESXi servers. However, as shown below, this archive [VirusTotal] also contained previously unknown encryptors for macOS, ARM, FreeBSD, MIPS, and SPARC CPUs.
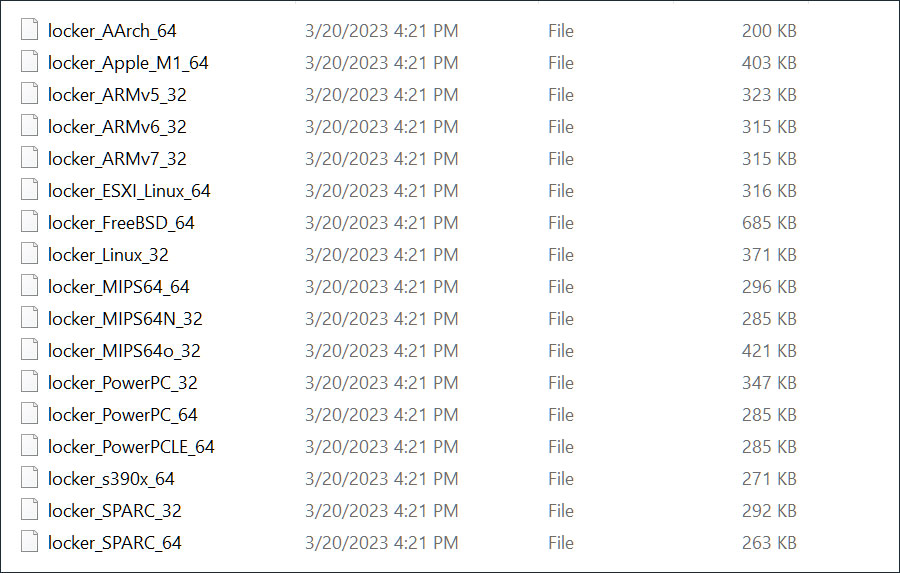 Archive of available LockBit encryptors
Archive of available LockBit encryptorsSource: BleepingComputer
These encryptors also include one named 'locker_Apple_M1_64' [VirusTotal] that targets the newer Macs running on Apple Silicon. The archive also contains lockers for PowerPC CPUs, which older Macs use.
Further research by cybersecurity researcher Florian Roth found an Apple M1 encryptor uploaded to VirusTotal in December 2022, indicating that these samples have been floating around for some time.
Likely test builds
BleepingComputer analyzed the strings in the LockBit encryptor for Apple M1 and found strings that are out of place in a macOS encryptor, indicating that these were likely haphazardly thrown together in a test.
For example, there are numerous references to VMware ESXi, which is out of place in an Apple M1 encryptor, as VMare announced they would not be supporting the CPU architecture.
_check_esxi esxi_ _Esxi _kill_esxi_1 _kill_esxi_2 _kill_esxi_3 _kill_processes _kill_processes_Esxi _killed_force_vm_id _listvms _esxcfg_scsidevs1 _esxcfg_scsidevs2 _esxcfg_scsidevs3 _esxi_disable _esxi_enableFurthermore, the encryptor contains a list of sixty-five file extensions and filenames that will be excluded from encryption, all of them being Windows file extensions and folders.
A small snippet of the Windows files the Apple M1 encryptor will not encrypt is listed below, all out of place on a macOS device.
.exe .bat .dll msstyles gadget winmd ntldr ntuser.dat.log bootsect.bak autorun.inf thumbs.db iconcache.dbAlmost all of the ESXi and Windows strings are also present in the MIPs and FreeBSD encryptors, indicating that they use a shared codebase.
The good news is that these encryptors are likely not ready for deployment in actual attacks against macOS devices.
Cisco Talos researcher Azim Khodjibaev told BleepingComputer that based on their research, the encryptors were meant as a test and were never intended for deployment in live cyberattacks.
While Windows has been the most targeted operating system in ransomware attacks, nothing prevents developers from creating ransomware that targets Macs.
The fact that they are being tested indicates that more advanced and optimized encryptors for these CPU architectures could come in the future.
Therefore, all computer users, including Mac owners, should practice good online safety habits, including keeping the operating system updated, avoiding opening unknown attachments and executables, and using strong and unique passwords at every site you visit.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·