BOOK THIS SPACE FOR AD
ARTICLE AD
The LockBit 2.0 ransomware gang is actively recruiting corporate insiders to help them breach and encrypt networks. In return, the insider is promised million-dollar payouts.
Many ransomware gangs operate as a Ransomware-as-a-Service, which consists of a core group of developers, who maintain the ransomware and payment sites, and recruited affiliates who breach victims' networks and encrypt devices.
Any ransom payments that victims make are then split between the core group and the affiliate, with the affiliate usually receiving 70-80% of the total amount.
However, in many cases, the affiliates purchase access to networks from other third-party pentesters rather than breaching the company themselves.
With LockBit 2.0, the ransomware gang is trying to remove the middle-man and instead recruit insiders to provide them access to a corporate network.
LockBit 2.0 promises millions of dollars to insiders
In June, the LockBit ransomware operation announced the launch of their new LockBit 2.0 ransomware-as-a-service.
This relaunch included redesigned Tor sites and numerous advanced features, including automatically encrypting devices on a network via group policies.
With this relaunch, LockBit has also changed the Windows wallpaper placed on encrypted devices to offer "millions of dollars" for corporate insiders who provide access to networks where they have an account.
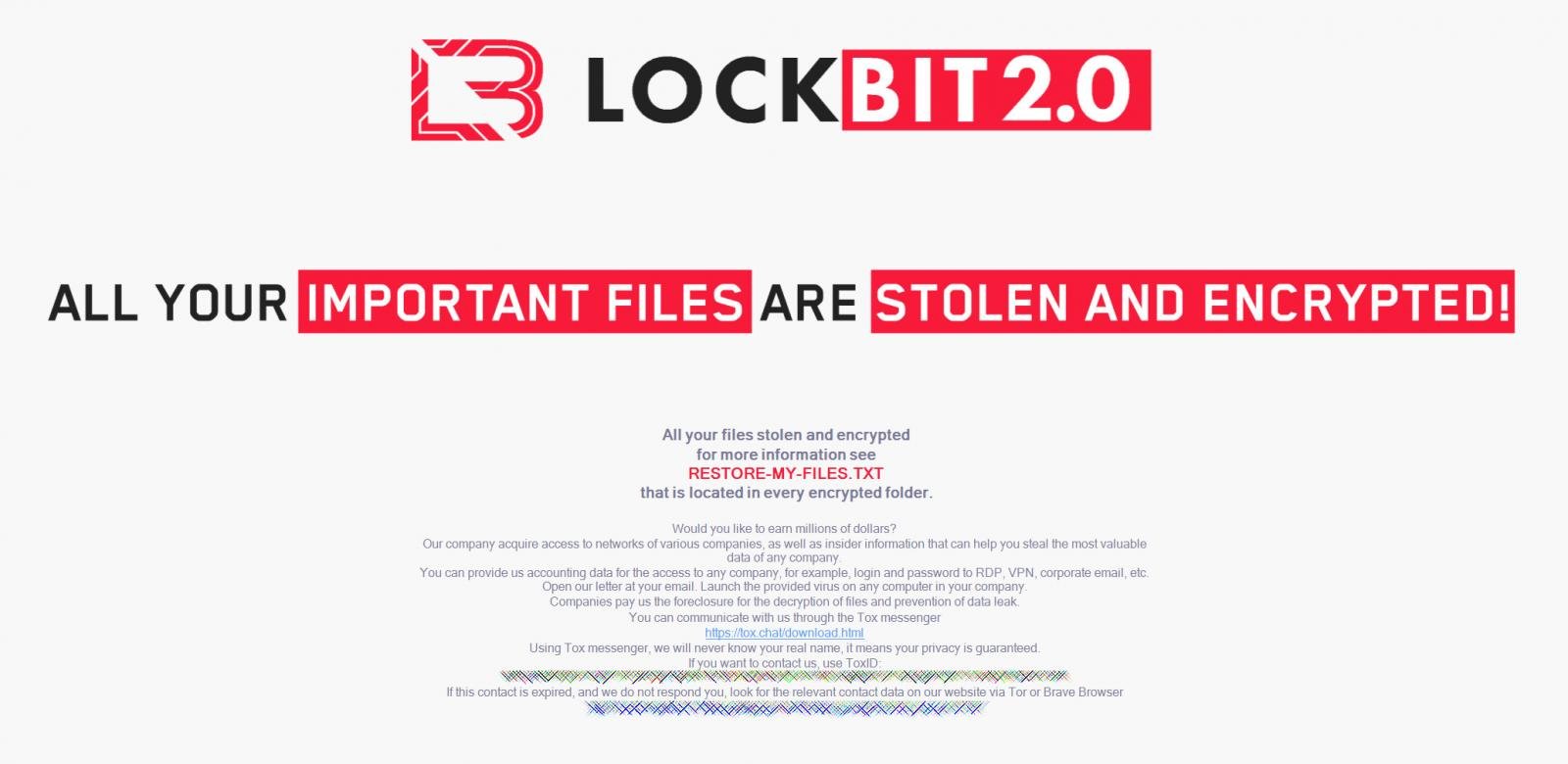 New LockBit 2.0 wallpaper recruiting insiders
New LockBit 2.0 wallpaper recruiting insidersThe full text, with the contact information redacted, explains that LockBit is looking for RDP, VPN, corporate email credentials that they can then use to gain access to the network.
The ransomware gang also says they will send the insider a "virus" that should be executed on a computer, likely to give the ransomware gang remote access to the network.
"Would you like to earn millions of dollars?
Our company acquire access to networks of various companies, as well as insider information that can help you steal the most valuable data of any company.
You can provide us accounting data for the access to any company, for example, login and password to RDP, VPN, corporate email, etc. Open our letter at your email. Launch the provided virus on any computer in your company.
Companies pay us the foreclosure for the decryption of files and prevention of data leak.
You can communicate with us through the Tox messenger
https://tox.chat/download.html
Using Tox messenger, we will never know your real name, it means your privacy is guaranteed.
If you want to contact us, use ToxID: xxxx"
When we first saw this message, it seemed counterintuitive to recruit an insider for a network already been breached.
However, this message is likely targeting external IT consultants who may see the message while responding to an attack.
While this tactic may sound far-fetched, it is not the first time threat actors attempted to recruit an employee to encrypt their company's network.
In August 2020, the FBI arrested a Russian national for attempting to recruit a Tesla employee to plant malware on the network of Tesla's Nevada Gigafactory.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·