BOOK THIS SPACE FOR AD
ARTICLE ADFinSpy has returned in new campaigns targeting dissident organizations in Egypt – and researchers uncovered new samples of the spyware targeting macOS and Linux users.
The FinSpy commercial spyware is back in recently observed campaigns against organizations and activists in Egypt. While the spyware previously targeted Windows, iOS and Android users, researchers have discovered these campaigns using new variants that target macOS and Linux users.
FinSpy is a full-fledged surveillance software suite, which has the ability to intercept victims’ communications, access private data, and record audio and video, according to Amnesty International, which uncovered the recent new variants. It’s been in use by law-enforcement and government agencies around the world since 2011.
However, researchers recently uncovered never-before-seen FinSpy samples that have been in use in campaigns since October 2019. These samples include “Jabuka.app,” a FinSpy variant for macOS, and “PDF,” a FinSpy variant for Linux. Both were publicly disclosed Friday for the first time.
“Through additional technical investigations into this most recent variant, Amnesty’s Security Lab also discovered, exposed online by an unknown actor, new samples of FinSpy for Windows, Android, and previously undisclosed versions for Linux and MacOS computers,” said Amnesty International researchers, in a Friday analysis.
FinSpy’s Past
FinSpy has been operating since 2011, however, in recent years researchers have spotted campaigns leveraging the spyware taking more innovative approaches.
In March 2019, Amnesty International published a report analyzing phishing attacks that were targeting Egyptian human rights defenders and media and civil -ociety organizations’ staff. These attacks, carried out by a group known as “NilePhish,” distributed samples of FinSpy for Microsoft Windows through a fake Adobe Flash Player download website.
In June 2019, Kaspersky researchers said they saw new instances of the spyware within the firm’s telemetry, including activity recorded in Myanmar last month. According to Kaspersky, several dozen unique mobile devices have been infected over the past year, using revamped implants. These newer samples targeted Android and iOS devices.
New Samples
The most recent attacks published this week continue to target Egyptian civil-society organizations. Researchers said that the FinSpy sample for macOS “uses a quite complex chain to infect the system, and the developers took measures to complicate its analysis.”
The sample is unique in that all its binaries are obfuscated with the open source LLVM-obfuscator, which was developed by a research team in 2013. However, according to Patrick Wardle, security researcher with Jamf, the obfuscation is easy to bypass.
“Good news, this obfuscation doesn’t really hinder analysis,” he said in a detailed analysis over the weekend. “One can simply scroll past it in a disassembler, or in a debugger set breakpoints on relevant (non-obfuscated) code.”
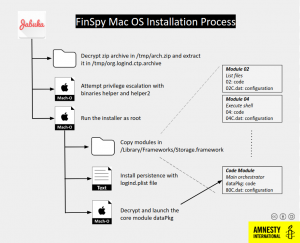
Once downloaded, the first stage of the spyware conducts checks to detect whether it is running in a virtual machine (VM). If not it decrypts a ZIP archive, which contains the installer and binaries for privilege escalation (including one that exploits a bug in macOS X and another with a Python exploit for CVE-2015-5889, which exists in the remote_cmds component in Apple OS X before 10.11).
“This first stage uses the exploits to get root access,” said Amnesty International researchers. “If none of them work, it will ask the user to grant root permissions to launch the next-stage installer.”
The Linux payload meanwhile is very similar to the macOS version, which researchers believe suggests a potential shared codebase. However, the launchers and the infection chain are adapted to work on Linux systems, with the “PDF” file obtained from the server being a short script containing encoded binaries for Linux 32bit and 64bit.
Once downloaded the file extracts an installer and executes it, which then checks that the system is not on a virtual machine before extracting a first-stage payload. Like its macOS counterpart, FinSpy for Linux is also obfuscated using LLVM-Obfuscator.
The malware variants for both macOS and Linux include a large list of modules with keylogging, scheduling and screen recording capabilities. They also have the abilities to steal emails by installing a malicious add-on to Apple Main and Thunderbird, which sends the emails for FinSpy to collect, and the capability of collecting information about Wi-Fi networks.
“FinSpy for Mac OS, and similarly its Linux counterpart, follow a modular design,” said researchers. “The launcher logind only instantiates the core component dataPkg, which oversees communications with the Command and Control server (C&C), and decrypting/launching modules when needed.”
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·