Cybersecurity researchers have discovered a number of malicious packages in the NPM registry specifically targeting a number of prominent companies based in Germany to carry out supply chain attacks.
"Compared with most malware found in the NPM repository, this payload seems particularly dangerous: a highly-sophisticated, obfuscated piece of malware that acts as a backdoor and allows the attacker to take total control over the infected machine," researchers from JFrog said in a new report.
The DevOps company said that evidence points to it being either the work of a sophisticated threat actor or a "very aggressive" penetration test.
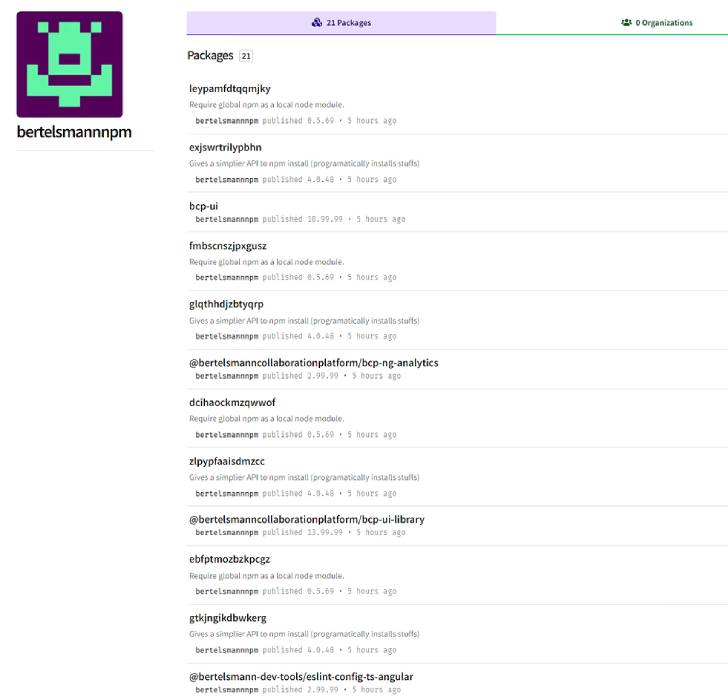
All the rogue packages, most of which have since been removed from the repository, have been traced to four "maintainers" - bertelsmannnpm, boschnodemodules, stihlnodemodules, and dbschenkernpm — indicating an attempt to impersonate legitimate firms like Bertelsmann, Bosch, Stihl, and DB Schenker.
Some of the package names are said to be very specific, raising the possibility that the adversary managed to identify the libraries hosted in the companies' internal repositories with the goal of staging a dependency confusion attack.
The findings build on a report from Snyk late last month that detailed one of the offending packages, "gxm-reference-web-auth-server," noting that the malware is targeting an unknown company that has the same package in their private registry.
"The attacker(s) likely had information about the existence of such a package in the company's private registry," the Snyk security research team said.
Calling the implant an "in-house development," JFrog pointed out that the malware harbors two components, a dropper that sends information about the infected machine to a remote telemetry server before decrypting and executing a JavaScript backdoor.
The backdoor, while lacking a persistence mechanism, is designed to receive and execute commands sent from a hard-coded command-and-control server, evaluate arbitrary JavaScript code, and upload files back to the server.
"The attack is highly targeted and relies on difficult-to-get insider information," the researchers said. But on the other hand, "the usernames created in the NPM registry did not try to hide the targeted company."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
125
2 years ago
125 















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·