Microsoft on Thursday disclosed that it addressed a pair of issues with the Azure Database for PostgreSQL Flexible Server that could result in unauthorized cross-account database access in a region.
"By exploiting an elevated permissions bug in the Flexible Server authentication process for a replication user, a malicious user could leverage an improperly anchored regular expression to bypass authentication to gain access to other customers' databases," Microsoft Security Response Center (MSRC) said.
New York City-based cloud security company Wiz, which uncovered the flaws, dubbed the exploit chain "ExtraReplica." Microsoft said it mitigated the bug within 48 hours of disclosure on January 13, 2022.
Specifically, it relates to a case of privilege escalation in the Azure PostgreSQL engine to gain code execution and a cross-account authentication bypass by means of a forged certificate, allowing an attacker to create a database in the target's Azure region and exfiltrate sensitive information.
In other words, successful exploitation of the critical flaws could have enabled an adversary to gain unauthorized read access to other customers' PostgreSQL databases, effectively circumventing tenant isolation.
Wiz zeroed down the privilege escalation to a bug stemming as a result of modifications introduced in the PostgreSQL engine to harden their privilege model and add new features. The name ExtraReplica comes from the fact that the exploit leverages a PostgreSQL feature that permits copying database data from one server to another, i.e., "replicating" the database.
The Windows maker described the security vulnerability as affecting PostgreSQL Flexible Server instances deployed using the public access networking option, but stressed that it did not find evidence of the flaw being actively exploited and that no customer data was accessed.
"No action is required by customers," MSRC said. "In order to further minimize exposure, we recommend that customers enable private network access when setting up their Flexible Server instances."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
235
2 years ago
235 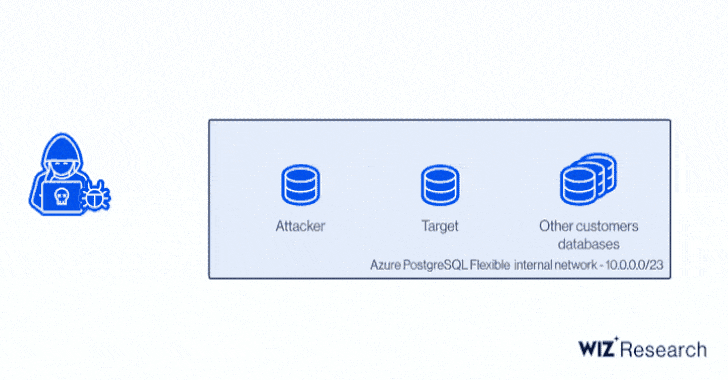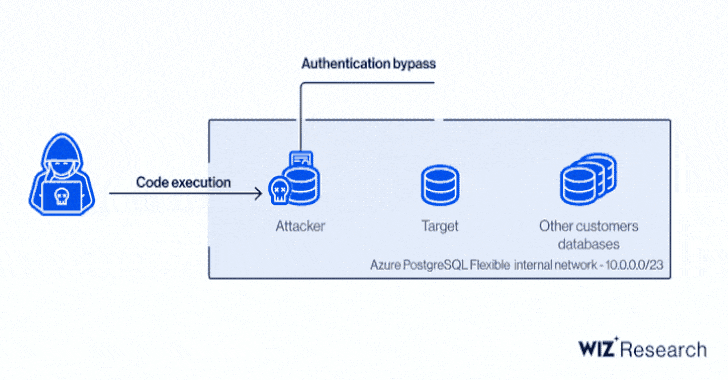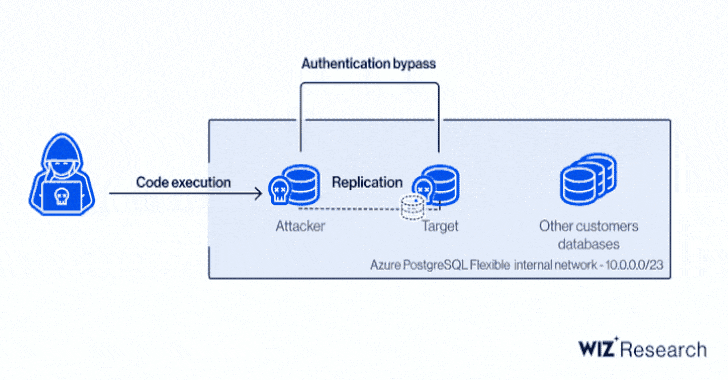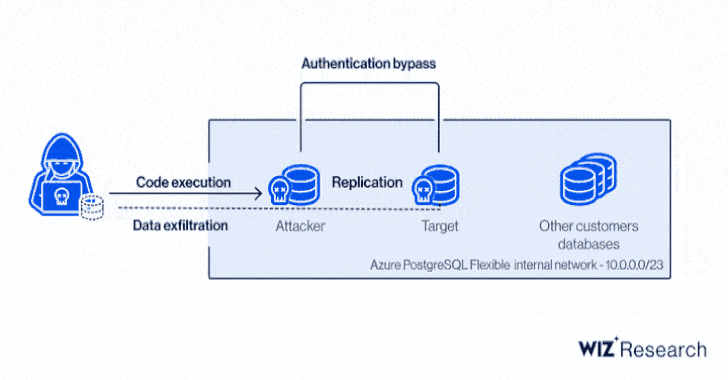

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·