Cybersecurity researchers have detailed critical security vulnerabilities affecting NETGEAR DGN2200v1 series routers, which they say could be reliably abused as a jumping-off point to compromise a network's security and gain unfettered access.
The three HTTPd authentication security weaknesses (CVSS scores: 7.1 – 9.4) impact routers running firmware versions prior to v1.0.0.60, and have since been fixed by the company in December 2020 as part of a coordinated vulnerability disclosure process.
"The rising number of firmware attacks and ransomware attacks via VPN devices and other internet-facing systems are examples of attacks initiated outside and below the operating system layer," Microsoft 365 Defender Research Team's Jonathan Bar Or said. "As these types of attacks become more common, users must look to secure even the single-purpose software that run their hardware—like routers."
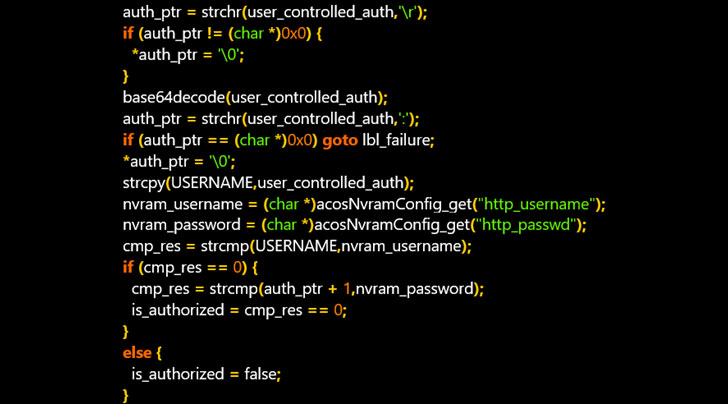
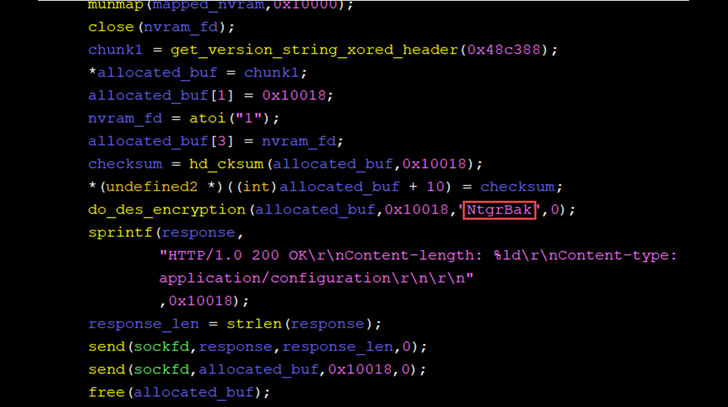
In a nutshell, the flaws allow accessing router management pages using an authentication bypass, enabling an attacker to gain complete control over the router, as well as derive saved router credentials via a cryptographic side-channel attack, and even recover the username and the password stored in the router's memory by exploiting the configuration backup\restore feature.
"The username and the password are compared [against the saved credentials] using strcmp," Bar Or explained. "The libc implementation of strcmp works by comparing character-by-character until a NUL terminator is observed or until a mismatch happens. An attacker could take advantage of the latter by measuring the time it takes to get a failure."
Furthermore, by abusing the aforementioned authentication bypass to fetch the configuration file, the researchers found that the credentials were encrypted using a constant key, which can be subsequently used to retrieve the plaintext password and the user name.
NETGEAR DGN2200v1 users are recommended to download and update to the latest firmware to fend off any potential attacks.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
190
3 years ago
190 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·