BOOK THIS SPACE FOR AD
ARTICLE AD
Microsoft has disclosed a high-severity Exchange Server vulnerability that allows attackers to forge legitimate senders on incoming emails and make malicious messages a lot more effective.
The security flaw (CVE-2024-49040) impacts Exchange Server 2016 and 2019, and was discovered by Solidlab security researcher Vsevolod Kokorin, who reported it to Microsoft earlier this year.
"The problem is that SMTP servers parse the recipient address differently, which leads to email spoofing," Kokorin said in a May report.
"Another issue I discovered is that some email providers allow the use of the symbols < and > in group names, which does not comply with RFC standards."
"During my research, I did not find a single mail provider that correctly parses the 'From' field according to RFC standards," he added.
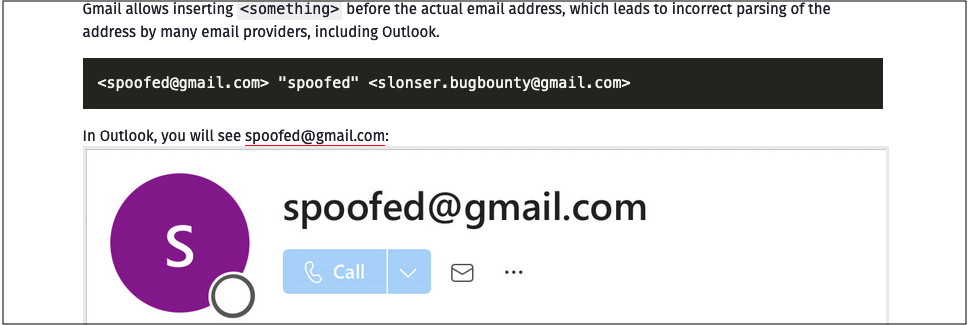 CVE-2024-49040 email spoofing (Vsevolod Kokorin)
CVE-2024-49040 email spoofing (Vsevolod Kokorin)Microsoft also warned today that the flaw could be used in spoofing attacks targeting Exchange servers and released several updates during this month's Patch Tuesday to add exploitation detection and warnings banners.
"The vulnerability is caused by the current implementation of the P2 FROM header verification, which happens in transport," Microsoft explained.
"The current implementation allows some non-RFC 5322 compliant P2 FROM headers to pass which can lead to the email client (for example, Microsoft Outlook) displaying a forged sender as if it were legitimate."
Exchange servers now warn of exploitation
While Microsoft has not patched the vulnerability and will accept emails with these malformed headers, the company says Exchange servers will now detect and prepend a warning to malicious emails after installing the Exchange Server November 2024 Security Update (SU).
CVE-2024-49040 exploitation detection and email warnings will be enabled by default on all systems where admins enable secure by default settings.
Up-to-date Exchange servers will also add a warning to the body of any emails it detects as having a forged sender and an X-MS-Exchange-P2FromRegexMatch header to allow admins to reject phishing emails attempting to exploit this flaw using custom mail flow rules.
"Notice: This email appears to be suspicious. Do not trust the information, links, or attachments in this email without verifying the source through a trusted method," the warning reads.
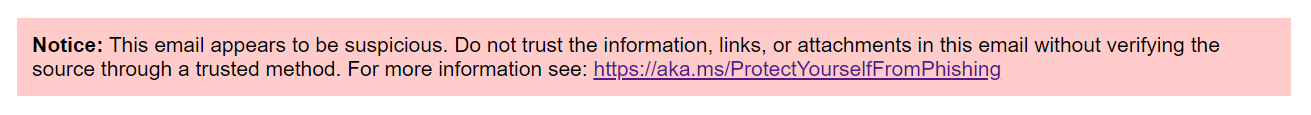 Suspicious message disclaimer (Microsoft)
Suspicious message disclaimer (Microsoft)While not advised, the company provides the following PowerShell command for those who still want to disable this new security feature (run it from an elevated Exchange Management Shell):
New-SettingOverride -Name "DisableNonCompliantP2FromProtection" -Component "Transport" -Section "NonCompliantSenderSettings" -Parameters @("AddDisclaimerforRegexMatch=false") -Reason "Disabled For Troubleshooting" Get-ExchangeDiagnosticInfo -Process Microsoft.Exchange.Directory.TopologyService -Component VariantConfiguration -Argument Refresh"Although it's possible to disable the feature using New-SettingOverride, we strongly recommend you leave the feature enabled, as disabling the feature makes it easier for bad actors to run phishing attacks against your organization," Redmond warned.
.png)














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·