BOOK THIS SPACE FOR AD
ARTICLE ADAttackers sent 52M malicious messages leveraging the likes of Office 365, Azure, OneDrive, SharePoint, G-Suite and Firebase storage in Q1 2021.
Threat actors are cashing in on the rapid shift to cloud-based business services during the pandemic, by hiding behind ubiquitous, trusted services from Microsoft and Google to make their email phishing scams look legit. And it’s working.
In fact, in the first three months of 2021 alone, researchers found 7 million malicious emails sent from Microsoft 365 and a staggering 45 million sent from Google’s infrastructure, Proofpoint reported, adding that cybercriminals have used Office 365, Azure, OneDrive, SharePoint, G-Suite and Firebase storage to send phishing emails and host attacks.
“The malicious message volume from these trusted cloud services exceeded that of any botnet in 2020, and the trusted reputation of these domains, including outlook.com and sharepoint.com, increases the difficulty of detection for defenders,” the report, issued Wednesday, explained. “This authenticity perception is essential, as email recently regained its status as the top vector for ransomware; and, threat actors increasingly leverage the supply chain and partner ecosystem to compromise accounts, steal credentials and siphon funds.”
Because breaching a single account could potentially provide sprawling access, ProofPoint reported that 95 percent of organizations were targeted for cloud account compromise, and of those, more than half were successful. Additionally, more than 30 percent of those organizations that were compromised “experienced post-access activity including file manipulation, email forwarding and OAuth activity.”
Once attackers have credentials, they can easily move in and out of a range of services and use those to send additional, convincing phishing emails.
Proofpoint provided several examples of campaigns hiding behind Microsoft and Google that attempted to scam users into giving up their information or delivering malware.
One message used a Microsoft SharePoint URL, which purported to link to a document outlining COVID-19 guidelines. Proofpoint’s team reported that this message was sent to 5,000 users in the transportation, manufacturing and business services sectors.
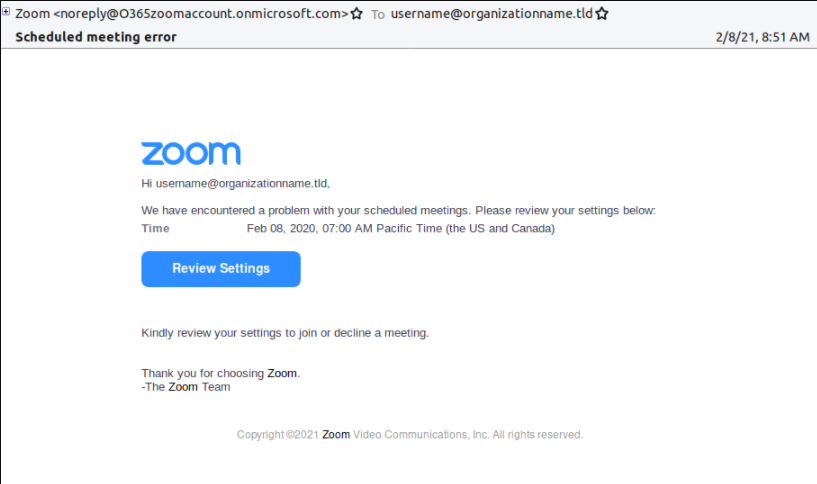
Another example provided by Proofpoint attempted to use the domain name “onmicrosoft.com” to deliver a fake video-conferencing credential harvesting email, which researchers observed was delivered to about 10,000 users.
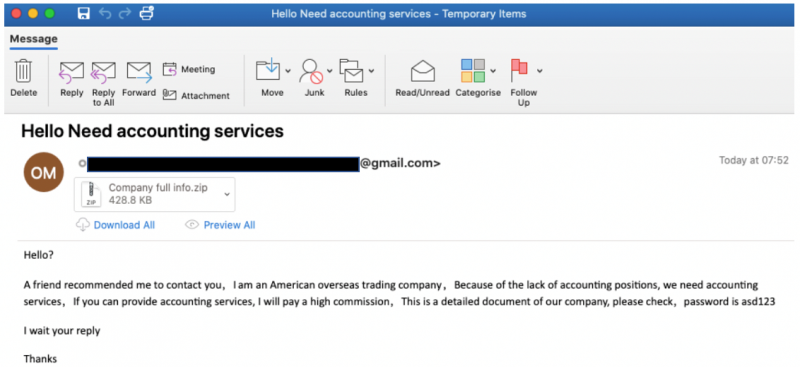
Attackers used Gmail to host another campaign starting in March, which delivered a fraudulent benefits message along with a Microsoft Excel attachment, which when macros were enabled, delivered The Trick banking trojan to steal credentials.
Another Gmail-hosted attack in February tries to induce users to access zipped MS Word documents by entering their passwords. Once opened, macros were enabled it delivered Xorist ransomware.
Attackers’ use of Gmail and Microsoft to lend a patina of legitimacy to their emails is part of a wider trend: Threat actors are generating increasingly convincing lures.
And at the tail end of May, Cofense flagged a phishing campaign using an Office SharePoint theme to bypass security gateways.
“Our research clearly demonstrates that attackers are using both Microsoft and Google infrastructure to disseminate malicious messages and target people, as they leverage popular cloud-collaboration tools,” The Proofpoint report added. “When coupled with heightened ransomware, supply chain, and cloud account compromise, advanced people-centric email protection must remain a top priority for security leaders.”
Download our exclusive FREE Threatpost Insider eBook, “2021: The Evolution of Ransomware,” to help hone your cyber-defense strategies against this growing scourge. We go beyond the status quo to uncover what’s next for ransomware and the related emerging risks. Get the whole story and DOWNLOAD the eBook now – on us!
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·