BOOK THIS SPACE FOR AD
ARTICLE ADAn APT group has started heavily relying on cloud services like Azure Active Directory and OneDrive, as well as open-source tools, to obfuscate its attacks.
Microsoft has suspended 18 Azure Active Directory applications that were being leveraged for command-and-control (C2) infrastructure by what it says is a Chinese nation-state actor.
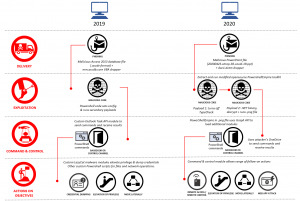
While Microsoft services like Azure Active Directory (AD) – its cloud-based identity and access management service – are popular among enterprises, cybercriminals are also swooping in on these services to enhance the weaponization of their malware payload, attempt to gain command and control all the way to the server, and obfuscate detection. One such threat group recently spotted leveraging these cloud services and open source tools is what Microsoft calls Gadolinium, a Chinese nation-state activity group that has been compromising targets for nearly a decade.
After compromising victim devices, Gadolinium was setting up AD accounts to receive commands from and send stolen data to its C2 server. But beyond that, the threat group has also stored stolen data in Microsoft’s file hosting service and synchronization service, OneDrive; launched attacks using the open source PowershellEmpire toolkit and used GitHub to host commands.
“Gadolinium has been experimenting with using cloud services to deliver their attacks to increase both operation speed and scale for years,” said Ben Koehl and Joe Hannon, with Microsoft’s Threat Intelligence Center, in a report posted Thursday.
Evolved Attacks
Gadolinium is also known as APT40, which researchers like FireEye have assessed with “moderate confidence” is a state sponsored espionage actor attributed to China. While previously Gadolinium has targeted worldwide maritime and health industries, Microsoft said recently it has observed newly expanded targeting for the threat group to include the Asia Pacific region and other targets in higher education and regional government organizations.
In mid-April 2020 the threat actors were detected sending spear-phishing emails with malicious attachments, with lures relating to the COVID-19 pandemic. When opened, the attached PowerPoint file (20200423-sitrep-92-covid-19.ppt), would drop a file, doc1.dotm, which then has two payloads that run in succession.
These include a payload that turns off a type check (DisableActivitySurrogateSelectorTypeCheck), while the second loads an embedded .Net binary that downloads a .Png image file.
“The .png is actually PowerShell which downloads and uploads fake png files using the Microsoft Graph API to https://graph.microsoft.com/v1.0/drive/root:/onlinework/contact/$($ID)_1.png:/content where $ID is the ID of the malware,” said researchers.
Behind the scenes, these attacks relied on a bundle of Microsoft services and open source tooling – which Microsoft said has been a steady trend in recent years for several nation-state activity groups migrating to open source tooling.
Gadolinium Leveraging Cloud Services
Researchers said that historically Gadolinium has leveraged custom-crafted malware families – but analysts have been able to identify these and defend against them.
In response, the threat actor has started experimenting with cloud applications to help it sidestep detection of its attacks, starting in 2018, when the threat group chose to use GitHub to host commands. Many cloud services frequently offer a free trial or one-time payment account offering (via PayGo), and malicious actors have found ways to take advantage of these legitimate business offerings, said researchers.
“By establishing free or PayGo accounts, they can use cloud-based technology to create a malicious infrastructure that can be established quickly then taken down before detection or given up at little cost,” said researchers.
This past year, Gadolinium has also started modifying portions of its attack vector, instead using open-source toolkits to obfuscate its activity and make it more difficult for analysts to track.
Microsoft said that the 18 Azure Active Directory applications that were suspended were part of Gadolinium’s PowerShell Empire infrastructure, which is a modified version of the open source PowershellEmpire toolkit. This is a toolkit that allows attackers to load additional modules to infected computers via Microsoft Graph API calls. It provides a command and control module that uses the attacker’s Microsoft OneDrive account to execute commands and retrieve results between attacker and victim systems.
“The attacker uses an Azure Active Directory application to configure a victim endpoint with the permissions needed to exfiltrate data to the attacker’s own Microsoft OneDrive storage,” said researchers. “From an endpoint or network monitoring perspective the activity initially appears to be related to trusted applications using trusted cloud service APIs and, in this scenario, no OAuth permissions consent prompts occur.”
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·