BOOK THIS SPACE FOR AD
ARTICLE ADThe data-extortion gang got at Microsoft’s Azure DevOps server. Meanwhile, fellow Lapsus$ victim and authentication firm Okta said 2.5 percent of customers were affected in its own Lapsus$ attack.
In a new blog post published last night, Microsoft confirmed that the Lapsus$ extortion group hacked one of its employee’s accounts to get “limited access” to project source code repositories.
“No customer code or data was involved in the observed activities. Our investigation has found a single account had been compromised, granting limited access. Our cybersecurity response teams quickly engaged to remediate the compromised account and prevent further activity,” Microsoft explained in an advisory about the Lapsus$ threat actors.
Over the weekend and into this week, the gang has publicly claimed to have penetrated Microsoft’s defenses and stolen source code, including code for the company’s Bing search engine, Bing Maps and Cortana voice assistant.
Compromised Azure DevOps Server
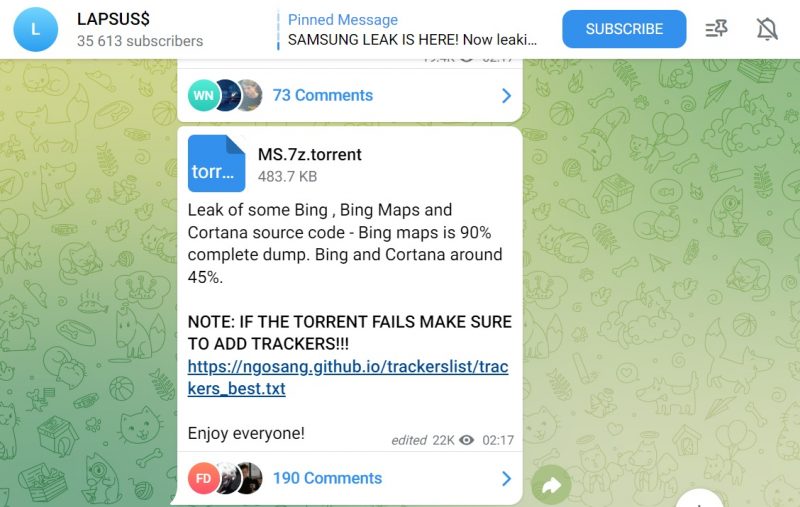
On Sunday, the actor announced that it had compromised Microsoft’s Azure DevOps server. Lapsus$ shared a screenshot of what were allegedly Microsoft’s internal source code repositories: leaked files that security researchers said appear to be legitimate internal source code.
LAPSU$ next victim seem to be @Microsoft (?)@SOSIntel @LawrenceAbrams pic.twitter.com/X5FmgajJcz
— 🥷🏼💻Tom Malka💻🥷🏼 (@ZeroLogon) March 20, 2022
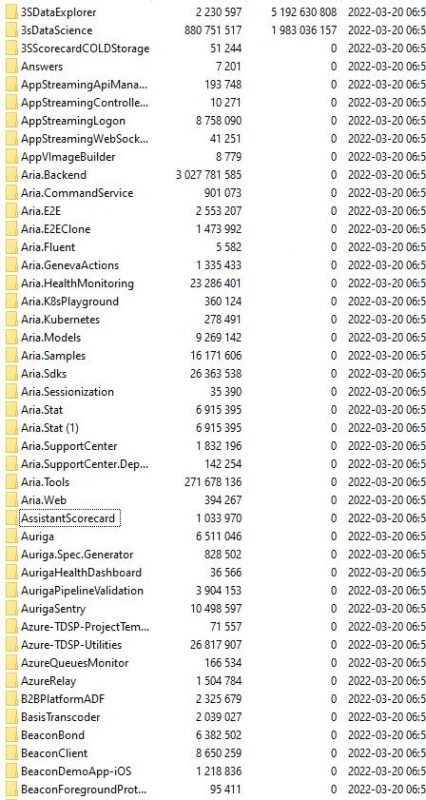
The threat actor has published more data since then: On Monday night, Lapsus$ posted a torrent for a 9GB 7zip archive containing the source code of over 250 projects that the gang claimed came from Microsoft. Then, last night, it released 37GB of that Azure DevOps server-derived data, BleepingComputer reported.
Security researchers who have pored over the leaked files told BleepingComputer that they appear to be legitimate internal source code from Microsoft; that the leaked projects contain emails and internal engineering documentation for mobile apps; and that the projects look to be for web-based infrastructure, websites, or mobile apps. However, the projects don’t contain source code for Microsoft desktop software such as Windows, Windows Server and Microsoft Office, according to the outlet’s sources.
Security Affairs shared a screenshot, shown below, of the uncompressed 7zip archive that contains the 37GB of source code belonging to hundreds of Microsoft projects.
Source code isn’t Medusa. Just looking at it won’t turn anybody into stone. The company “does not rely on the secrecy of code as a security measure and viewing source code does not lead to elevation of risk,” Microsoft’s advisory said.
Lapsus$ TTPs
Microsoft tracks Lapsus$ as DEV-0537. Its advisory outlines the gang’s tactics, techniques and procedures (TTPs) that it uses to compromise user identities so as to gain initial access to a targeted organization, including:
Deploying the malicious Redline password stealer to obtain passwords and session tokens Purchasing credentials and session tokens from criminal underground forums Paying employees at targeted organizations (or suppliers/business partners) for access to credentials and MFA approval Searching public code repositories for exposed credentialsMicrosoft confirmed that Lapsus$ had used the TTPs in the gang’s attack on Microsoft. “Our team was already investigating the compromised account based on threat intelligence when the actor publicly disclosed their intrusion,” according to its advisory. “This public disclosure escalated our action allowing our team to intervene and interrupt the actor mid-operation, limiting broader impact.”
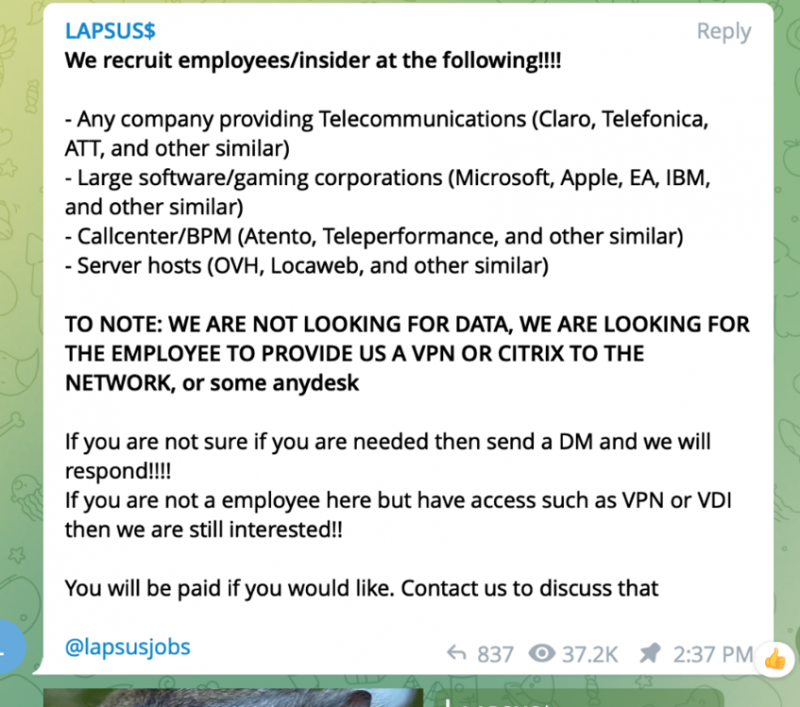
With regards to the third bullet point in that TTP list – paying rogue employees to help it crack a target’s defenses – Lapsus$ hasn’t been particularly subtle about its recruitment efforts. The gang posted a notice on its Telegram channel on March 10, telling the world that it was up for recruiting company insiders, including those at Microsoft; other big software/gaming companies such as Apple, IBM or EA; telecoms such as Telefonica, ATT; and more, to help it carry out its dirty work.
How to Stop Lapsus$
Microsoft’s advisory offered a detailed list of recommendations for organizations to help them avoid going through what it, Okta and a growing list of Lapsus$ victims have suffered.
Below are some of the company’s top-level suggestions. Its advisory drills down into each:
Strengthen MFA implementation Require healthy and trusted endpoints Leverage modern authentication options for VPNs Strengthen and monitor your cloud security posture Improve awareness of social engineering attacks Establish operational security processes in response to DEV-0537 intrusionsLapsus$ Got at Data for 2.5% of Okta Customers
Lapsus$ also breached authentication firm Okta, it claimed: a claim supported by what the actor purported were screenshots of Okta’s Slack channels and the interface for Cloudflare, which is one of thousands of customers that use Okta’s technology to provide authentication for its employees.
In an update published last night, Okta Chief Security Officer David Bradbury confirmed the hit and provided details on the skope, saying that about 2.5 percent of the company’s customers were potentially affected by a January 2022 Lapsus$ intrusion. Hence, those companies’ data “may have been viewed or acted upon,” he said. As of Tuesday night, Okta had already contacted affected customers by email.
Moving to the cloud? Discover emerging cloud-security threats along with solid advice for how to defend your assets with our FREE downloadable eBook, “Cloud Security: The Forecast for 2022.” We explore organizations’ top risks and challenges, best practices for defense, and advice for security success in such a dynamic computing environment, including handy checklists.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·