BOOK THIS SPACE FOR AD
ARTICLE ADKremlin-linked actors have launched multiple assaults since invasion began

A new report from Microsoft has revealed that at least six separate Russian nation-state actors have launched damaging cyber-attacks against Ukraine since the invasion began earlier this year.
The study (PDF), released yesterday (April 27), detailed how Microsoft researchers have tracked at least 237 “cyber operations” originating from Russia.
These attacks “have not only degraded the systems of institutions in Ukraine but have also sought to disrupt people’s access to reliable information and critical life services on which civilians depend, and have attempted to shake confidence in the country’s leadership”, Microsoft states.
It comes more than two months after Russian troops invaded neighboring Ukraine, sparking the beginning of a war that has so far claimed tens of thousands of lives.
Direct hits
Microsoft has observed these cyber-attacks as being “strongly correlated and sometimes directly timed” with Russia’s kinetic military operations targeting services and institutions crucial for civilians.
“For example, a Russian actor launched cyber-attacks against a major broadcasting company on March 1, the same day the Russian military announced its intention to destroy Ukrainian ‘disinformation’ targets and directed a missile strike against a TV tower in Kyiv,” the report details.
As many as 32% of destructive attacks directly targeted Ukrainian government organizations at the national, regional, and city levels, while more than 40% of attacks were aimed at organizations in critical infrastructure sectors that could have negative second-order effects on the Ukrainian government, military, economy and civilians.
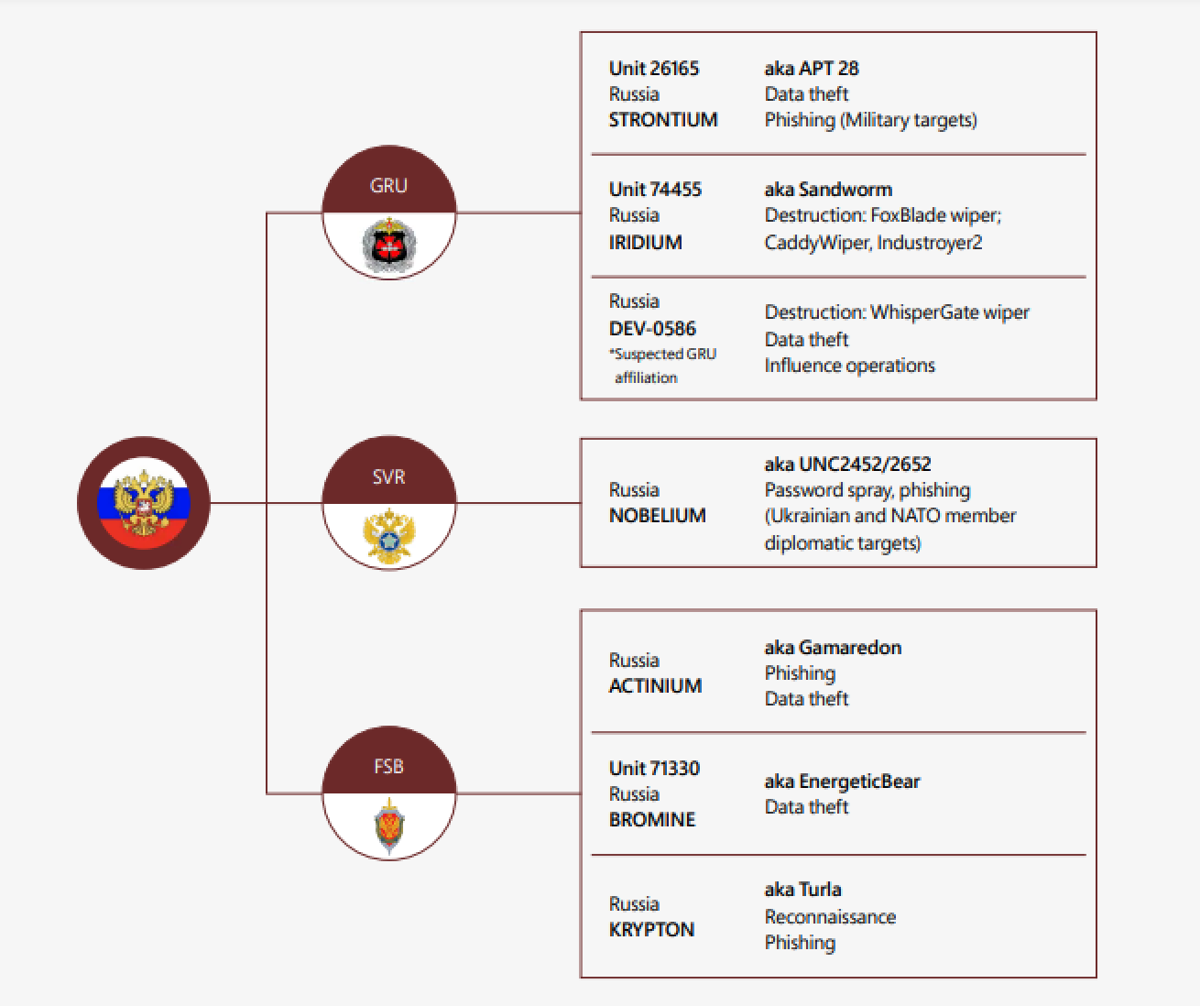 A diagram detailing some of the nation-state actors identified by Microsoft
A diagram detailing some of the nation-state actors identified by Microsoft
“At least six known or suspected Russian cyber threat groups in addition to other unattributed threat actors are engaged in activities that range from reconnaissance and phishing for initial access to pervasive lateral movement, data theft, and data deletion,” according to Microsoft.
“The multiple phases of their operations suggest these actors are positioning themselves for continued compromises and impact on Ukrainian networks for the duration of this conflict and beyond.”
Nation-state groups mentioned in the report include GRU unit 74455, aka Sandworm, also known as Iridium, which Microsoft claims is responsible for the malware FoxBlade wiper, CaddyWiper, and Industroyer2. GRU is Russian military intelligence.
Read more of the latest security news from Ukraine
Also mentioned in the report is Nobellium, aka APT29, which is thought to be led by Russia’s Foreign Intelligence Service, which has been seen using password spraying and phishing attacks against Ukrainian and NATO member diplomatic targets.
Microsoft stated that these attacks used a variety of techniques to gain initial access to their targets including phishing, use of unpatched vulnerabilities, and compromising upstream IT service providers.
The tech giant also noted how the cyber-attackers often modify their malware with each deployment to evade detection. “Notably, our report attributes wiper malware attacks we previously disclosed to a Russian nation-state actor we call Iridium,” Microsoft added.
READ MORE Data wiper deployed in cyber-attacks targeting Ukrainian systems
The Windows-specific data wiper appeared on “hundreds of machines”, according to telemetry from information security firm ESET, in the days following the invasion.
The wiper abuses legitimate drivers from the EaseUS Partition Master software in order to corrupt data.
Although primarily directed towards Ukraine, the ‘HermeticWiper’ malware strain has also been detected in the Baltic states of Latvia and Lithuania.
Date stamps on the malware indicate that it was compiled two months before the invasion – evidence that the cyber-attack was premeditated.
Continued escalation
“Given Russian threat actors have been mirroring and augmenting military actions, we believe cyber-attacks will continue to escalate as the conflict rages,” Microsoft concluded.
“Our report includes specific recommendations for organizations that may be targeted by Russian actors as well as technical information for the cybersecurity community.
“We will continue to provide updates as we observe activity and believe we can safely disclose new developments.”
The full report (PDF) contains more information, including a detailed timeline of individual attacks targeting Ukraine.
DON’T MISS Ukrainian ISP used by military disrupted by ‘powerful’ cyber-attack
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·