BOOK THIS SPACE FOR AD
ARTICLE AD
Microsoft's Digital Crimes Unit (DCU) has seized 17 malicious domains used by scammers in a business email compromise (BEC) campaign targeting the company's customers.
The domains taken down by Microsoft were so-called "homoglyph" domains registered to resemble those of legitimate business. This technique allowed the threat actors to impersonate companies when communicating with their clients.
According to the complaint filed by Microsoft last week (more details available in the court order), they used the domains registered via NameSilo LLC and KS Domains Ltd./Key-Systems GmbH as malicious infrastructure in BEC attacks against Office 365 customers and services.
"Defendants use malicious homoglyph domains together with stolen customer credentials to unlawfully access customer accounts, monitor customer email traffic, gather intelligence on pending financial transactions, and criminally impersonate O365 customers, all in an attempt to deceive their victims into transferring funds to the cybercriminals," Microsoft said.
"The relief sought in this action is necessary to stop the cybercriminals and prevent irreparable and ongoing harm to Microsoft and its customers."
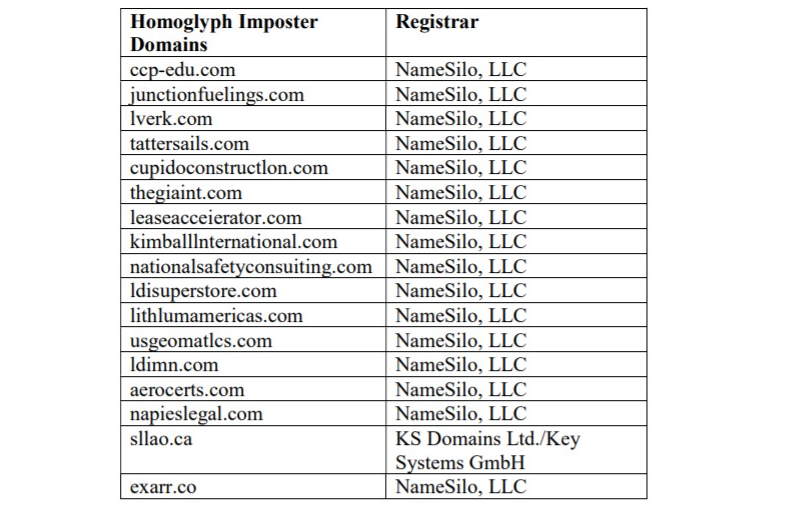 Malicious homoglyph domains taken down by Microsoft
Malicious homoglyph domains taken down by MicrosoftBEC scammers from West Africa
The criminals behind this campaign are "part of an extensive network that appears to be based out of West Africa" per Microsoft and have mainly targeted North American small businesses operating across several industry sectors.
"The group proceeded to gather intelligence to impersonate these customers in an attempt to trick victims into transferring funds to the cybercriminals," Hogan-Burney said.
"Once the criminals gained access to a network, they imitated customer employees and targeted their trusted networks, vendors, contractors and agents in an effort to deceive them into sending or approving fraudulent financial payments."
These tactics perfectly line up with methods used in BEC scams where attackers employ various tactics (including social engineering, phishing, and hacking) to compromise business email accounts, later used to redirect payments to bank accounts under their control or to target employees as part of gift card scams.
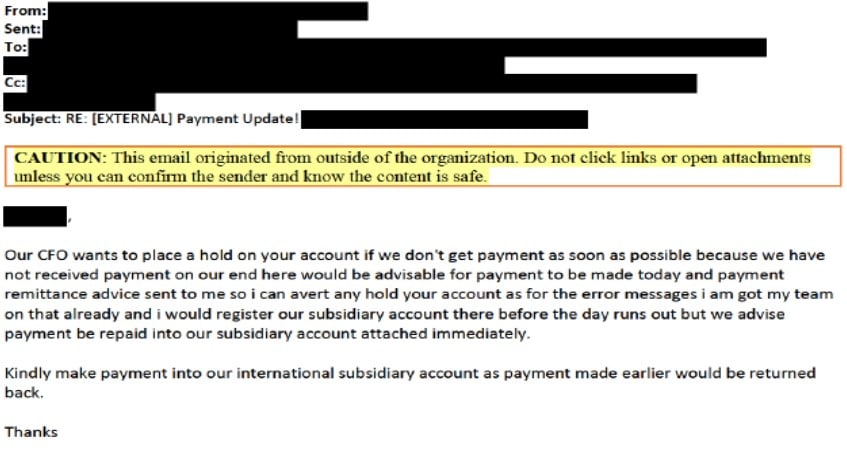 Sample email sent by BEC scammers (Microsoft)
Sample email sent by BEC scammers (Microsoft)This is not the first time Microsoft has had to deal with such incidents. For instance, last month, Microsoft 365 Defender researchers disrupted the cloud-based infrastructure used by another large-scale BEC campaign.
In the June attacks, the scammers used legacy protocols like IMAP/POP3 to exfil emails and circumvent MFA on Exchange Online accounts when the targets failed toggle off legacy auth.
One month earlier, Microsoft detected one more BEC gang targeting over 120 organizations using typo-squatted domains registered only a few days before the attacks started.
"We continue to see this technique used in business email compromise (BEC), nation state activity, malware and ransomware distribution, often combined with credential phishing and account compromise to deceive victims and infiltrate customer networks," Hogan-Burney concluded.
"This disruption effort follows 23 previous legal actions against malware and nation-state groups that we’ve taken in collaboration with law enforcement and other partners since 2010."
BEC behind $1.8 billion in losses last year
Although in some cases, BEC scammers' methods may seem to lack sophistication and their phishing emails might look clearly malicious to some, BEC attacks have been behind record-breaking financial losses since 2018.
The FBI 2020 annual report on cybercrime has listed a record number of over $1.8 billion in losses reported just last year.
In March, the FBI also warned of BEC attacks increasingly targeting US state, local, tribal, and territorial (SLTT) government entities.
In other alerts sent last year, the FBI warned of BEC scammers abusing email auto-forwarding and cloud email services (including Microsoft Office 365 and Google G Suite) in their attacks.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·