Microsoft on Thursday shared fresh guidance on yet another vulnerability affecting the Windows Print Spooler service, stating that it's working to address it in an upcoming security update.
Tracked as CVE-2021-34481 (CVSS score: 7.8), the issue concerns a local privilege escalation flaw that could be abused to perform unauthorized actions on the system. The company credited security researcher Jacob Baines for discovering and reporting the bug.
"An elevation of privilege vulnerability exists when the Windows Print Spooler service improperly performs privileged file operations. An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges," the Windows maker said in its advisory. "An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights."
However, it's worth pointing out that successful exploitation of the vulnerability requires the attacker to have the ability to execute code on a victim system. In other words, this vulnerability can only be exploited locally to gain elevated privileges on a device.
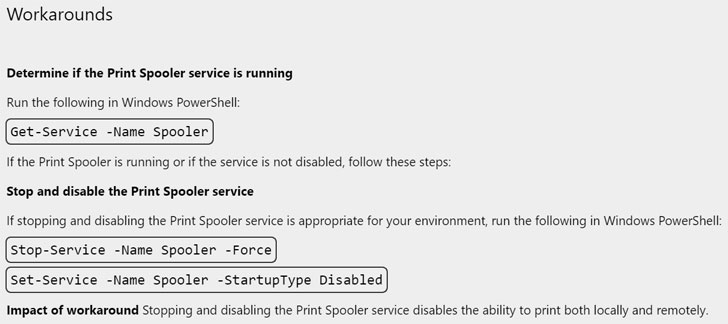
As workarounds, Microsoft is recommending users to stop and disable the Print Spooler service to prevent malicious actors from exploiting the vulnerability.
The development comes days after the Redmond-based firm rolled out patches to address a critical shortcoming in the same component that it disclosed as being actively exploited to stage in-the-wild attacks.
Dubbed PrintNightmare (CVE-2021-34527), the vulnerability stems from a missing permission check in the Print Spooler that enables the installation of malicious print drivers to achieve remote code execution or local privilege escalation on vulnerable systems.
However, it later emerged that the out-of-band security update could be entirely bypassed under specific conditions to gain both local privilege escalation and remote code execution. Microsoft has since said the fixes were "working as designed and is effective against the known printer spooling exploits and other public reports collectively being referred to as PrintNightmare."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
207
3 years ago
207 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·