BOOK THIS SPACE FOR AD
ARTICLE ADOriginally, since 2019, Mispadu Stealer targeted Spanish- and Portuguese-speaking victims, but the new variant aims at URLs associated with Mexican citizens.
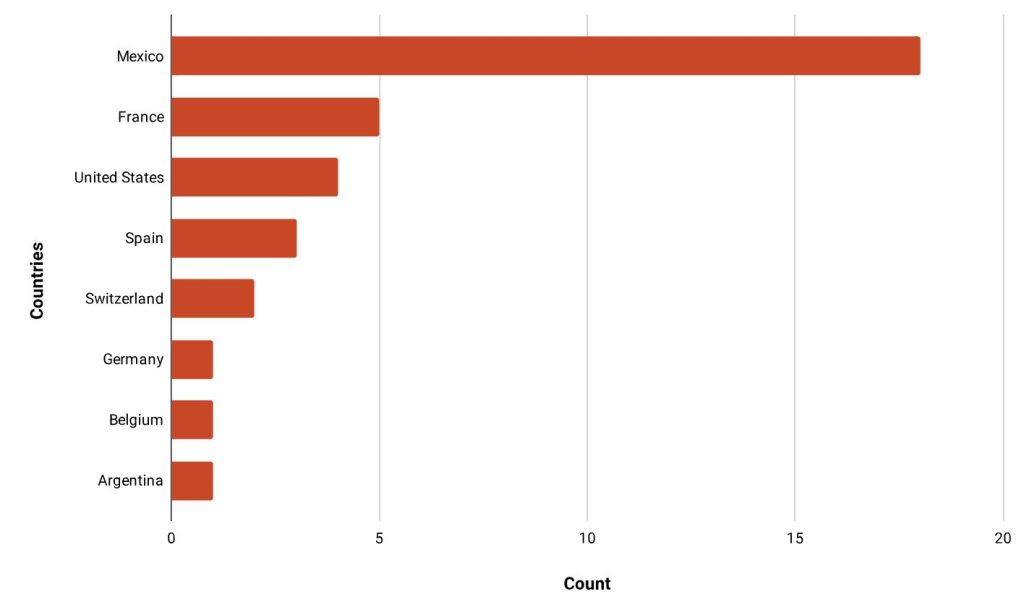
In a recent development reported by Unit 42 researchers, a new variant of the infamous Mispadu Stealer has emerged, targeting users primarily in Mexico with stealthy information-stealing techniques. The discovery shows the persistent evolution of this malware, showcasing its adaptability and the challenges it poses to cybersecurity efforts.
Initially identified in 2019, Mispadu Stealer has been a persistent threat, known for its stealthy operations primarily targeting Spanish- and Portuguese-speaking victims. The latest variant, however, demonstrates a high level of sophistication, specifically targeting regions and URLs associated with Mexican citizens.
The discovery of this new variant came as part of Unit 42’s Managed Threat Hunting initiative, while researchers were investigating the Windows Defender SmartScreen CVE-2023-36025 vulnerability.
This vulnerability, categorized as a security feature bypass within the Windows SmartScreen function, allows attackers to circumvent warnings and execute malicious payloads. Exploiting this vulnerability, the Mispadu Stealer variant was found to employ a crafty technique involving the creation of internet shortcut files (.url) or hyperlinks pointing to malicious files, effectively bypassing SmartScreen’s warnings.
One of the key findings in this investigation is the malware’s use of a parameter referencing a network share, which, when embedded in a .url file, directs victims to a threat actor’s network share to retrieve and execute the malicious payload without triggering SmartScreen warnings. This technique, while not limited to Mispadu Stealer, showcases the malware’s ability to adapt and evolve its tactics.
Further analysis of the new variant reveals a sophisticated operation that selectively targets victims based on their geographic location and system configurations. By querying the bias between the local time zone and UTC and performing checks based on the victim’s location, the malware ensures its execution primarily within specific regions, such as the Americas and certain parts of Western Europe.
Once executed, the malware proceeds to interact with the victim’s browser history, extracting URLs and checking them against a targeted list. Notably, the malware employs encryption algorithms and techniques to evade detection, highlighting the evolving sophistication of its information-stealing capabilities.
The attribution of this new variant to previous Mispadu campaigns highlights the challenges in combating evolving cybersecurity threats. While similarities in tactics and infrastructure provide insights into the malware’s origins, the ever-changing nature of such threats demands a comprehensive approach to cybersecurity.
As Mispadu continues to evolve and target unsuspecting users, cybersecurity experts emphasize the importance of staying informed on the latest threat intelligence, deploying strong endpoint protection measures, and advocating a culture of cybersecurity awareness among employees and users. By adopting proactive measures and leveraging collective intelligence, organizations can better defend against emerging threats like the new variant of Mispadu Stealer.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·