BOOK THIS SPACE FOR AD
ARTICLE ADBackground
Linux exploitation by bad actors from People Republic of China (in short: PRC) is not a new matter. Their attacks are coming everyday and their method is also improving by days.
This post is another case of the issue, except it is reporting you some improvement and new source of DoS threat from the same landscape. The unique point of this one is by combining ElasticSearch exploitation for Linux boxes AND also aiming Windows machines via a malicious MOF (Managed Object Format) coded in a malicious PHP-MySQL webshell to exploit the WMI (Windows Management Instrumentation) architecture to remotely upload/execute any desired payload for infection. Obviously the windows infection pattern is targeting old systems with __EventConsumer runs in SYSTEM privilege (Windows XP and Windows 2003 Server). There are also an ASP web shell and some hacktools spotted.
The combination of the above threat is wrapped in a single multi purpose CNC GUI panel, that can control and monitor the attack performed, until the DDoS activity, for Linux and Windows client basis ddosers.
The ELF malware used as bot client for DDoS purpose is a new coded one, firstly spotted it in December 5th 2015,and the bad actors is synchronizing the latest version with its CNC GUI server software. Yes, we have a new threat here. As for the Windows PE DDoSer it was checked by our team (thank's B) as a variant of Linux/MrBlack malware in Win32 version. In this post we named the new malware found as Linux/DDOSTF variant.
The Wrath DDoS Stresser Service / 天罚DDoS集群压力测试系统
It's all started by and centered to this "wanna-look-legit" Chinese origin DDoS service. Which its site is in the domain of ddos.tf , this time we quicky took the snapshot of the site for the audience safe view in here [link]
.
You can browse this service's information safely about the "features" promoted in the snapshot site by using google translation, to give you a good idea what this site is doing.
In the top page, there is a snapshot picture of the DDoS CNC server software panel of its ELF botnet
which is showing the recent last version (version 6) of the DDoS client/server malware served. In a glimpse it looks exactly like the BillGates CNC tools by the design, I think they managed to copy it, somehow.
A lot of features was promoted in the 2nd tab, which we suggest the investigator to translate & read them for its correlation to the malware in this case, and in the third menu tab you can view some clear snapshots they made for the alternative older versions from 3,4,5 which is showing its support to Linux and Windows DDoS bot client managed by the one-centered CNC panel.
In the bottom of the page you will see the web exploitation tool they use to gain privilege to windows machine, using the .asp(x) script to get the payload installed & (flood) attack controllers:
I think these are real snapshots with having some slight modification for promotion purpose. Apparently we have a very serious player here. And that's linked to the information in the next tab.
In the 4th tab you can see the price list information of using this service, and how to reach the actor for the payment purpose (see:264164661 part)
..and in the 5th tab it's showing the "disclaimer" too as per following original chinese language (I copy pasted for you to automate-translating):
which is basically explaining that the author is not responsible for any bad usage..urging customers to use it for personal purpose only, and business usage guideline..and blah blah info for contacting the actor.
Is it as legal as it's stated?
Good question. And the answer is obviously NOT, below is our argument:
Once upon a time, about 24+ hours ago, there's an attack coming to an innocent ElasticSearch server from this panel:

And a red-handed evidence was spotted during an effort to infect this innocent Linux server using downloaded ELF malware files from that a malware HFS web panel to this victim host:
The attacker was using the ElasticSearch known vulnerability/exploit (thank's for the log) and that ATTACKER-PANEL is the ip of the panel mentioned in picture snapshot above. P.S.:we will disclose the IP after the threat is taken down.
The ELF file udp and syb downloaded are known ELF Linux/BillGates malware variant (with encoded commands in the codes to make reversing difficult..which was FAILED) and are using IP basis CNC in 173.254.236.97:25000. The host that's used as CNC is in United States with below detail:
"ip": "173.254.236.97", "hostname": "173.254.236.97.static.quadranet.com", "city": "Los Angeles", "region": "California", "country": "US", "loc": "34.0438,-118.2512", "org": "AS8100 QuadraNet, Inc", "postal": "90014"The panel also contains the older made of Linux/BillGates (CNC is IP basis 122.114.124.26:25000) and Linux/Elknot.freeBSD (CNC is IP basis 122.114.124.26:11223)
The geo location of IP 122.114.124.26:
There are also six files of accompanied new type of ELF DDoSers.
But what's the connection of this panel with the ddos.tf ?
In the next section the connection of this panel to the ddos.tf will be seen clear as ice..
As the additional information, in the ddos.tf site, there are some archives hidden inside that one of them contains the infamous s.exe with its pairs of ip.txt and pass.txt, the SSH weak credential bruter tool... In the legit site?? Hmm..
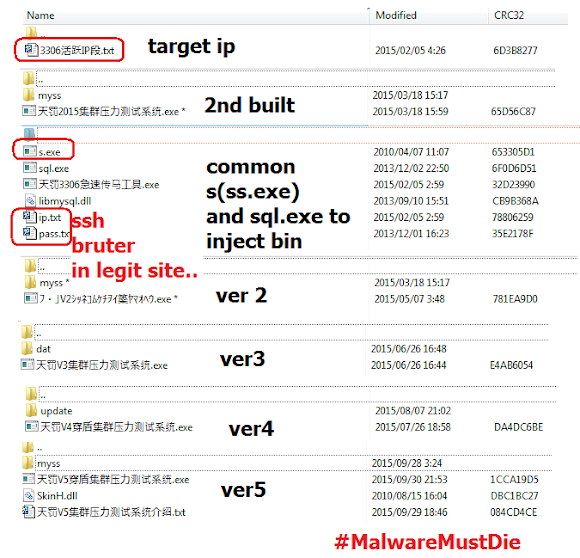
Linux/DDOSTF a new ELF DDoS malware
I decided to name the new malware as Linux/DDOSTF since this is the specific malware made for this site, it's original and we can see its characteristic clearly. The first ELF file of this kind which was spotted online, is named as JrLinux, which is probably its original name(?), but Linux/DDOSTF is easier to remember to refer to its threat's source.
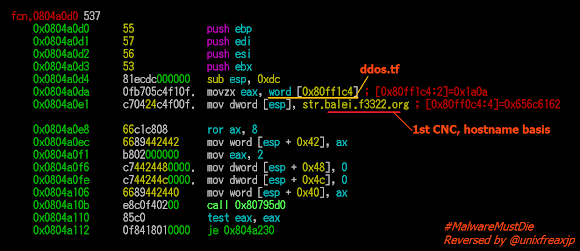
The samples are all originally coded in C compiled with stripped and static ELF, it is "fun" to reverse. This malware uses the 2 types of CNC, the one which is the pingback that is hard-coded its IP address in the binary, as you can see in the next picture, and the other is the hidden decoded base64 hostname. All of the binaries are builder basis which the five of them are all identical in skeleton that shows the ELF basis template was used as a master.
The first relation of the ddos.tf with this panel can be viewed in the new ELF Linux/DDOSTF in the below location/address which is stated its threat origin (refer to the 8888 binary):

You can see also the IP address for the first connection is written in hard-coded.
The second relation is as per explained in the ddos.tf site itself, it's camouflage the ELF into the Windows .exe file, as per seen in the new ELF with injected strings as if a Windows binary's property..
As you can see in the screenshot in the ddos.tf site:
The usage of the myss is also spotted in myss.exe and myss injection panel. So this is their "idea" of bypassing firewall as per also written in the chinese language promotion note in the ddos.tf site.
The attacker part is initially can be spotted starting at 0x0804A3D8 which is having two initial values of UDP-Flow (default) or SYN-Flow flags defined during the distribution:
If you trace it further you'll meet the jump switch in here, which stated the specific form of each attacks:

I counted to see 12 routes to packet flood logic via below jump references:
Which are having SYN, DNS, TCP and ACK logic, with four of them are HTTP floods using following snippets as HTTP headers, these 12 attacks is well-known used in Linux/BillGates and these functions are likely being snagged & modified by ddos.tf.
0x080b1d74 .string" GET %s HTTP/1.1\\r\\n Host: %s\\r\\n Connection: Keep-Alive\\r\\n Accept: */*\\r\\n Accept-Language: zh-CN\\r\\n Accept-Encoding: gzip, deflate\\r\\n User-Agent: Mozilla/5.0+(compatible;+Baiduspider/2.0;++http://wwwbaidu.com/search/spider.html)\\r\\n Referer: http://%s%s\\r\\n Pragma: no-cache\\r\\n DNT: 1\\r\\n Connection: Keep-Alive\\r\\n" 0x080b1e98 .string " GET %s HTTP/1.1\\r\\n Host: %s\\r\\n Connection: Keep-Alive\\r\\n Accept: */*\\r\\n Accept-Language: zh-CN\\r\\n Accept-Encoding: gzip, deflate\\r\\n User-Agent:Mozilla/5.0 (compatible;+Googlebot/2.1;++http://www.google.com/bot.html)\\r\\n Referer: http://%s%s\\r\\n Pragma: no-cache\\r\\n DNT: 1\\r\\n Connection: Keep-Alive\\r\\n\\r\\n"The hidden CNC leads to the domain of myss.basec.cc which is the third PoC relation of the malware download panel to the ddos.tf service (the myss mark), you can spot these sign in "distributed" version of the binaries at the below info, with its resolved data now:

And the function uses this CNC is in 0x8048FE8 with its communication "protocol".

The IP registered to this CNC is 58.220.41.10 in:
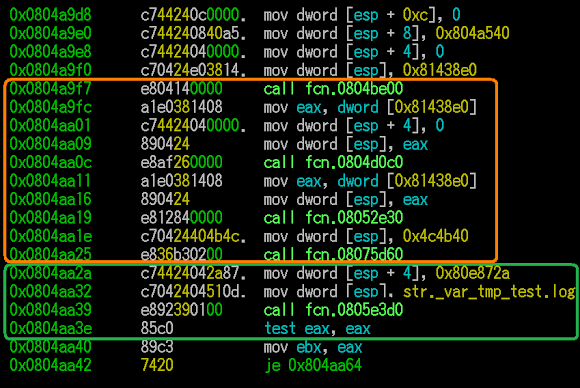
On the first run, the malware does sys_clone itself and then re- sys_clone-ing itself to then redirect the stdin, stdout, and stderr to /dev/null (for silent noises) and then do the double sys_clone again following by changing its work directory to /tmp , it then runs its main process afterward. This information is important if you want to trail/debug its processes properly.
This DDoS'er connects to first CNC, to send the initial infected report which I counted as 520 bytes blob data:
As you can see in the picture above, along with the system information, the infected host is informing the CNC whether the ELF initially flagged as UDP-flow or SYN-flow, and that info received is shown in the panel shown at ddos.tf site's screenshot:
Well, accordingly from the CNC, the below part of its control panel will be the place where the target of the DDoS will be entered, correspondenced to the infected DDoS Linux/DDOSTF bots to start the attack.
After calling back, this malware is supposed to make connection to the decoded CNC in myss.basec.cc afterward, and static compiled DNS resolver library will translate the connection to its IP to supposedly performing further steps.
This is an additional: The previous version differences
This earlier version also doesn't have the SYN/UDP-Flow tag, and therefore doesn't have the encoded hidden CNC function/data.
So it seems the hidden CNC is a new feature. I am not so sure why the hidden CNC is used in the recent version only. It's suggesting "maybe" the coder want to secretly track the distribution of this malware binaries. Below is an easy way to check that encoded CNC:
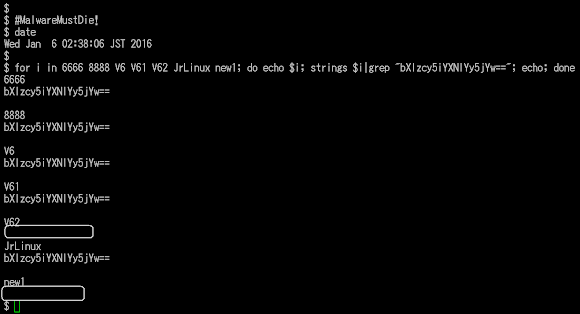
The hashes of the ELF samples & their checked CNC are as per below, our team mates are uploading the samples to the VirusTotal accordingly:
Hash (md5) ELF CNC1 CNC2 --------------------------------------------------------------------------- 71a868cdcc6b79b7d274e3b558cd4596 8888 173.254.236.97:8888 myss.basec.cc(port: 8893) 3e0d96cd1e0a97e61d96b7863f39a1d4 6666 122.114.124.26:6666 myss.basec.cc(port: 8893) 3e0d96cd1e0a97e61d96b7863f39a1d4 V6 122.114.124.26:6666 myss.basec.cc(port: 8893) bf65b4947b194be658fdc2b2fb09c35b V61 122.114.124.26:3795 myss.basec.cc(port: 8893) 3df2c500b5466b5ed2c7907fe8e0e1d5 V62 122.114.124.26:3795 (none) (none) 3e0d96cd1e0a97e61d96b7863f39a1d4 JrLinux 122.114.124.26:6666 myss.basec.cc(port: 8893) dac95d35a611cc8b4f21f9f77e10ead9 oldver balei.f3322.org:6666 (none) (none) *) myss.basec.cc = 58.220.41.10 (CN/AS23650/Chinanet Jiangshu) *) balei.f3322.org = 222.186.34.143 (CN/AS23650/Chinanet Jiangshu) ---------------------------------------------------------------------------Windows DDoSer used is..Mr.Black WinPE variant
The DDOS client payload for the Windows is Mr.Black WinPE version, it is a known threat with the good detection ratio, so I will not make comment for this.
The sample is in Virus Total [link]. And the CNC accessed is hostname basis myss.ddns.net (with same IP address as ELF at 58.220.41.10) in port 8893 too.
ASP WinShell + PHP MySQL .MOF WinShell + etc
This story is not over yet, there are two files that is important for all of us to be aware of, as per marked below:
The .aspx file, which it's not a new threat, is an ASP Web Shell which its functions are self-explanatory in the modified snapshot below:

The interesting one is the mof.php file, it is the PHP-MySQL coded to aim WMI exploitation via malicious MOF file. The common practise for the known MOF exploit file is by ASP script, but this attacker is using rather unique method, by using PHP & MySQL instead.
The interface can be pretty much viewed if you run it safely as web code as per following:

Since the PHP/MySQL as front end for WMI exploitation via MOF injection is rather rare to myself and my fellow team mates too, I tried to break down its codes as detailed as possible in the picture below:

It's amazingly "evil concept" isn't it? Yes, it is obviously a copy-paste code (see reference). I don't think they even calculated the chance to infect Windows running with PHP and MySQL installed beforehand..no wonder it has the low infection hit even it's already up ITW like 6+ months.
I almost miss this one. There is more "Binary Injection Webshell" tool also powerd by PHP/MySQL in that panel: it is udf.php, the snapshot taken during some efforts emulating the web shell :
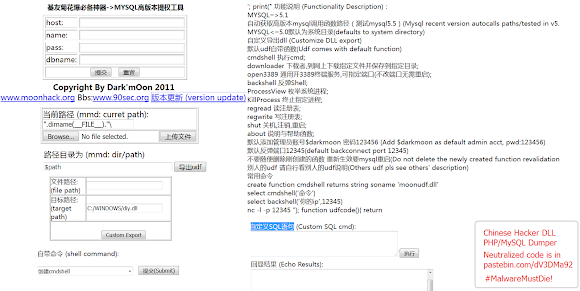
I translated the Chinese comments and captions, and also neutralized the code for not being maliciously re-used then uploaded it to our pastebin [link] for your review due to mitigation purpose. It's a PHP/SQL base (malicious) DLL injector with the custom injection option interface, with hard-coded the template default DLL in its PHP as binary text.
Seeing these two MySQL-base injection webshell scripts, I start to realize that MySQL is also powerful tool to perform a binary and file injection, and that is the reason why the actor was putting mysql.exe in the panel too. "Maybe" this is also why PHP code is chosen instead ASP. Or maybe I just took it too serious and the actor is just another copy-paster :-)
One last thing that maybe we all need to know is the tool called NetFuke is spotted in the panel, which is a nice PRC made interface sniffer [link], and looks like the atacker was using it as a tool to generate report like this:
Yes. This panel is really heavy loaded not only with malware but with webshell weapons & hacking tools. The ELF & windows malware used are pointing to the ddos.tf. Are these attackers actually the actor behind ddos.tf site (owners/administrators)? Or maybe one of the "customers" of the ddos.tf? It's still a question. Either way, the activity of the infection panel has to be stopped.
Recently I found a panel in Hongkong contains the binaries of Windows PE of DDOSTF that are not originated to MrBlack-base code (an improvement from what was previous written in this blog post), but these new binaries were either ported from the DDOSTF or coded based on the same logic as the linux version:
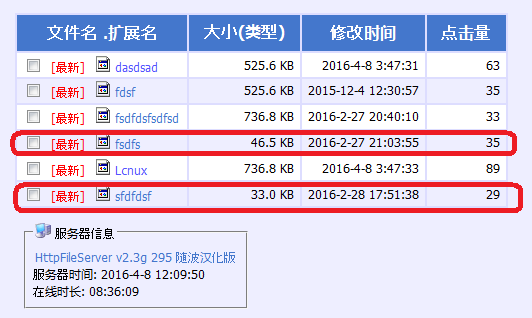
The samples I uploaded to kernelmode -->here, feel free to fetch.
The unique functionality of this windows version is the Windows OS detection, which is providing detection from Windows 2000 to Windows 8 as you can see in the below 2 snippet code:


After the version checked, the below case switch action will be executed depends on the flag of commands:
The code is in fn.0x40483B(), if you want to see the disassembled code one is in-->here
The offensive function was called in the case 0x5 to the fn.0x00403f05. You will see some same SleepTrick() (or break or 0 pause tricks combined calling prinf)..whatever you want to call it, which is explaining that many printf() was called (see picture below)
Just pass these and move forward to 0x00403f52 where you can see the other switch of 0x12 case for the thread management (picture is below)

The switch-cases I sorted as per below:
Each switch is having calls specific way on attack method and in creating threads and handles.
One thing that can be used to ID the threat is the attack code in 0x0403D7a at the below code:
This is match to the "myss" tag in-->here. This is the callback function that is using HTTP with specific HTTP referer to Baidu address:
Each attack performed is simple and specific, like the part I reversed in here:

Other attacks has different logic, it is really case by case..
Additionally, DDOS.TF windows versions are also having function to manipulate origin IP address into 192.168.1.244 and 192.168.1.32, which can be found in two attacks functions in my sample.
I hate to mock, but I have to do it after seeing the HTTP headers used for the L7 attacks of Win32/DDOS.TF, see it carefully and you will know how "IMPOSSIBLE" for some faked bots requesting in such combination.. This is supporting the fact that the coder/group behind this malware are teenagers with lacking of knowledge..
Please see below picture in marked parts, think it well and enjoy! :-))
To the young scums behind this threat, our message to you:
STOP these badness kids, go to decent path. You and your stupid "anonymous" mask won't hide you and your ID much..
#MalwareMustDie!!
Recent attacker IP for ElasticSearch of suspected same actor(same M.O.)
These are IP source of recent recorded attackers of with same panel/M.O.:
173.254.236.11|173.254.236.11.static.quadranet.com.|8100 | 173.254.192.0/18 | ASN-QUADRANET-GLOBAL | US | quadranet.com | QuadraNet Inc 173.254.236.19|173.254.236.19.static.quadranet.com.|8100 | 173.254.192.0/18 | ASN-QUADRANET-GLOBAL | US | quadranet.com | QuadraNet Inc 173.254.236.26|173.254.236.26.static.quadranet.com.|8100 | 173.254.192.0/18 | ASN-QUADRANET-GLOBAL | US | quadranet.com | QuadraNet Inc 173.254.236.55|173.254.236.55.static.quadranet.com.|8100 | 173.254.192.0/18 | ASN-QUADRANET-GLOBAL | US | quadranet.com | QuadraNet IncPlease be noted that these IP are in the same network ASN/prefix AS8100 / 173.254.192.0/18 as the latest CNC used: 173.254.236.97
Epilogue, follow up, additional reference
Thank's for the MMD ELF research cool team mates, to B for 1st spotting new ELF that is ending up to a quite long post :), to Y for nice initial analysis on the webshell exploitation, to W1 for digging all resources for exploitation codes, and W2 to spread & analysis infrastructure, you're all the best.
Good reference for MOF exploitation in Windows WMI can be found here--> [-1-][-2-][-3-][-4-]
The full view of the panel infection of ddos.tf payloads:
The sample & more info for researchers is shared at kernelmode [link]
Please help to raise detection ratio [-1-][-2-]of this new ELF variant.
@MalwareMustDie all #ELF #malware analysis:https://t.co/bsbzIIVYea was on #UNIX/@FreeBSD OS & @radareorg+gdb+objdump +posted via @firefox
— ☩MalwareMustDie (@MalwareMustDie) January 5, 2016@MalwareMustDie sure. we have blacklisted the mentioned C2 domains/IPs.
— liuya (@liuya0904) January 5, 2016@MalwareMustDie here's a different windows sample talking to same servers: https://t.co/hIjBNQ3zsa
— Travis Green (@travisbgreen) January 5, 2016@MalwareMustDie Linux/Ddostf.A, update 12822 https://t.co/6WLuFON7Oh ;-)
— Michal Malík (@michalmalik) January 5, 20166 new Open signatures, 41 new Pro. ELF.MrBlack, Dridex, Nitol.K, Darkhotel. Thanks: Kevin Ross & @MalwareMustDie https://t.co/iy0OvKtazz
— ET Labs (@ET_Labs) January 7, 2016Ddostf Win32+ELF sample: https://t.co/vhlbnJrFuM https://t.co/DBcKZUVBge https://t.co/dPGZXCM5N8
— Benkow wokned (@benkow_) January 12, 2016Create DDoSTf.yar Rule to detect ELF.DDosTf infection Ref: https://t.co/4P25nbXsk7 Thanks @benkow_ https://t.co/B6ra6jjICy
— Yara Rules (@yararules) January 13, 2016Stay safe! Happy New Year 2016 form MalwareMustDie!
.png)














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·