BOOK THIS SPACE FOR AD
ARTICLE ADState-sponsored cyberattackers are using Google Drive, Dropbox and other legitimate services to drop spyware on Middle-Eastern targets and exfiltrate data.
Malicious files doctored up to look like legitimate content related to the Israeli-Palestine conflict are being used to target prominent Palestinians, as well as activists and journalists in Turkey, with spyware.
That’s according to a disclosure from Zscaler, which attributes the cyberattacks to the MoleRats advanced persistent threat (APT). Zscaler’s research team was able to tie MoleRats, an Arabic-speaking group with a history of targeting Palestinian interests, to this campaign because of overlap in the .NET payload and command-and-control (C2) servers with previous MoleRats APT attacks.
This campaign started last July, Zscaler reported.
MoleRats used the Dropbox API for C2 communications in both this and previous campaigns, as well as Google Drive and other established cloud-hosting services to host the payloads, according to Zscaler.
“The targets in this campaign were chosen specifically by the threat actor and they included critical members of the banking sector in Palestine, people related to Palestinian political parties, as well as human rights activists and journalists in Turkey,” Zscaler’s analysts found.
The analysts also found overlapping domain SSL-certificate data in this attack and previous known MoleRats attacks, as well as common domains used for passive DNS resolution, the report added.
The attack delivers malicious decoy Arabic-language content seemingly related to the Palestinian conflict with Israel, with a macro code, which executes a PowerShell command to fetch the malware:
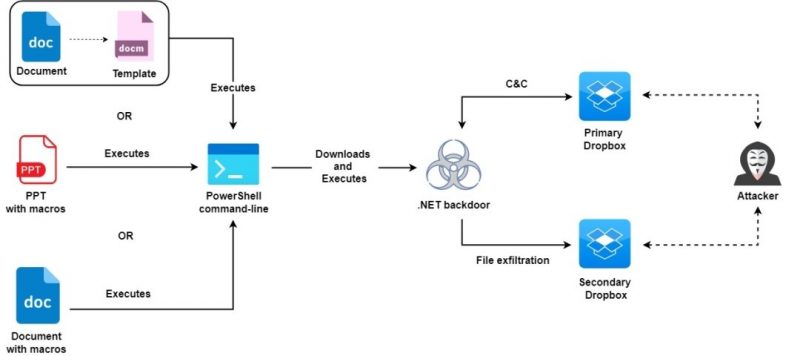
 New MoleRats Backdoor Delivery
New MoleRats Backdoor Delivery
Once executed, the malware creates a backdoor to the victim’s device and downloads its contents to a Dropbox folder, according to the researchers, who report finding at least five Dropboxes currently being used by the attackers.
Zscaler tracked the attack chain back through Dropbox and discovered that the APT’s machine is operating in the Netherlands with the same IP subnet as the C2, along with domains used in past MoleRats APT campaigns.
The most recent MoleRats attacks showed some innovation over previous campaigns in backdoor delivery, according to the report.
“Although we are not sure how these .RAR/.ZIP files were delivered, considering the past attacks they were likely delivered using phishing PDFs,” the Zscaler team determined.
The Zscaler report comes amid a recent explosion of APT attacks, which are up more than 50 percent over the past year. That’s fueled in large part by Log4Shell attacks, according to recent Check Point Research.
Check out our free upcoming live and on-demand online town halls – unique, dynamic discussions with cybersecurity experts and the Threatpost community.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·