The politically motivated Moses Staff hacker group has been observed using a custom multi-component toolset with the goal of carrying out espionage against its targets as part of a new campaign that exclusively singles out Israeli organizations.
First publicly documented in late 2021, Moses Staff is believed to be sponsored by the Iranian government, with attacks reported against entities in Israel, Italy, India, Germany, Chile, Turkey, the U.A.E., and the U.S.
Earlier this month, the hacker collective was observed incorporating a previously undocumented remote access trojan (RAT) called "StrifeWater" that masquerades as the Windows Calculator app to evade detection.
"Close examination reveals that the group has been active for over a year, much earlier than the group's first official public exposure, managing to stay under the radar with an extremely low detection rate," findings from FortiGuard Labs reveal.
The latest threat activity involves an attack path that leverages the ProxyShell vulnerability in Microsoft Exchange servers as an initial infection vector to deploy two web shells, followed by exfiltrating Outlook Data Files (.PST) from the compromised server.
Subsequent phases of the infection chain involve an attempt to steal credentials by dumping the memory contents of a critical Windows process called Local Security Authority Subsystem Service (Lsass.exe), before dropping and loading the "StrifeWater" backdoor (broker.exe).
The installation of the "Broker" implant, which is used to execute commands fetched from a remote server, download files, and exfiltrate data from target networks, is facilitated by a loader that masquerades as a "Hard Disk Drives Fast Stop Service" dubbed "DriveGuard" (drvguard.exe).
On top of that, the loader is also responsible for launching a watchdog mechanism ("lic.dll") that ensures its own service is never interrupted by restarting the DriveGuard every time it's stopped as well as ensuring that the loader is configured to run automatically on system startup.
The broker backdoor, for its part, is also equipped to delete itself from the disk using a CMD command, capture screenshots, and update the malware to replace the current module on the system with a file received from the server.
StrifeWater is also notable for its attempts to stay under the radar by posing as the Windows Calculator app (calc.exe), with FortiGuard Labs researchers discovering two older samples dating back to the end of December 2020, suggesting that the campaign has been operational for over a year.
The attribution to Moses Staff is based on similarities in the web shells used in previously disclosed attacks and its pattern of victimology.
"The group is highly motivated, capable, and set on damaging Israeli entities," the researchers said. "At this point, they continue to depend on 1-day exploits for their initial intrusion phase. Although the attacks we identified were carried out for espionage purposes, this does not negate the possibility that the operators will later turn to destructive measures."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
154
2 years ago
154 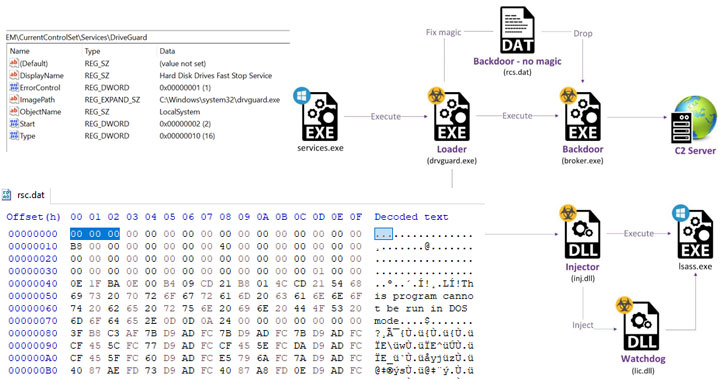

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·