BOOK THIS SPACE FOR AD
ARTICLE AD
Mozi malware botnet activity faded away in August after a mysterious unknown party sent a payload on September 27, 2023, that triggered a kill switch to deactivate all bots.
Mozi is a well-known DDoS (distributed denial of service) malware botnet that emerged in 2019, primarily targeting IoT devices such as routers, digital video recorders, and other internet-connected gadgets.
The malware leveraged known vulnerabilities or weak default passwords to compromise devices and make them part of its decentralized peer-to-peer network, where they communicate using BitTorrent's DHT (distributed hash table) protocol.
Mozi mysteriously killed
Today, ESET reported that its telemetry data showed a sharp drop in Mozi activity on August 8, 2023, starting with a halt to all operations in India.
This was followed by a similar sudden termination of activities in China, where the botnet originates, on August 16, 2023.
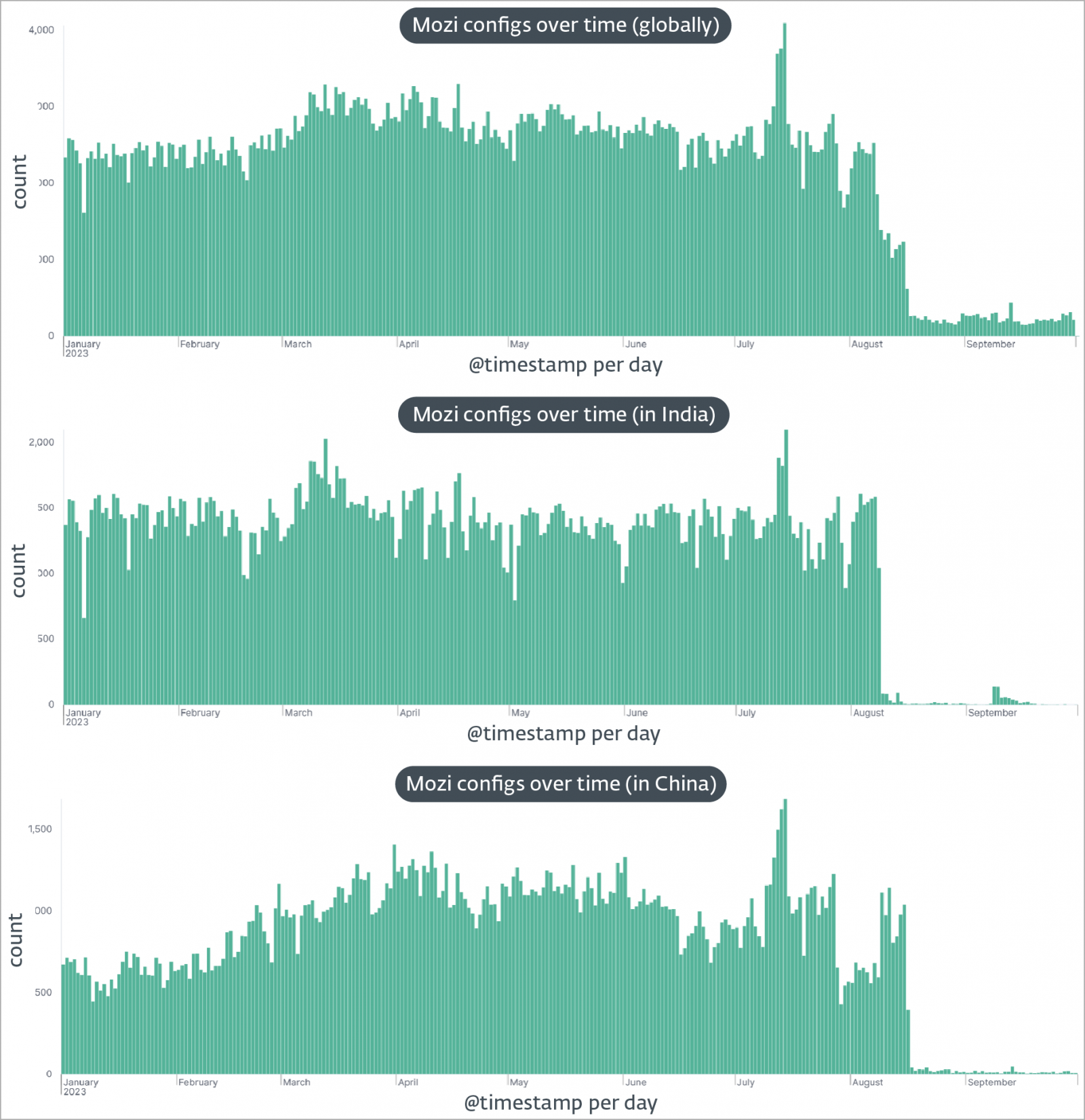 Observed Mozi activity (ESET)
Observed Mozi activity (ESET)Finally, on September 27, 2023, a UDP message was sent to all Mozi bots eight times instructing them to download an update via HTTP, which caused the following:
Termination of the Mozi malware process, Disabling certain system services (sshd and dropbear), Replacement of the Mozi file, Execution of device configuration commands, Blocking access to various ports, Establish a foothold for the new file.The fact that whoever pressed the kill switch opted to maintain persistence for the new payload, which can also ping a remote server to assist in tracking, implies a controlled takedown.
ESET's code analysis showed strong similarities between the original Mozi code and the binaries used in the takedown, which featured the correct private keys for signing the payload.
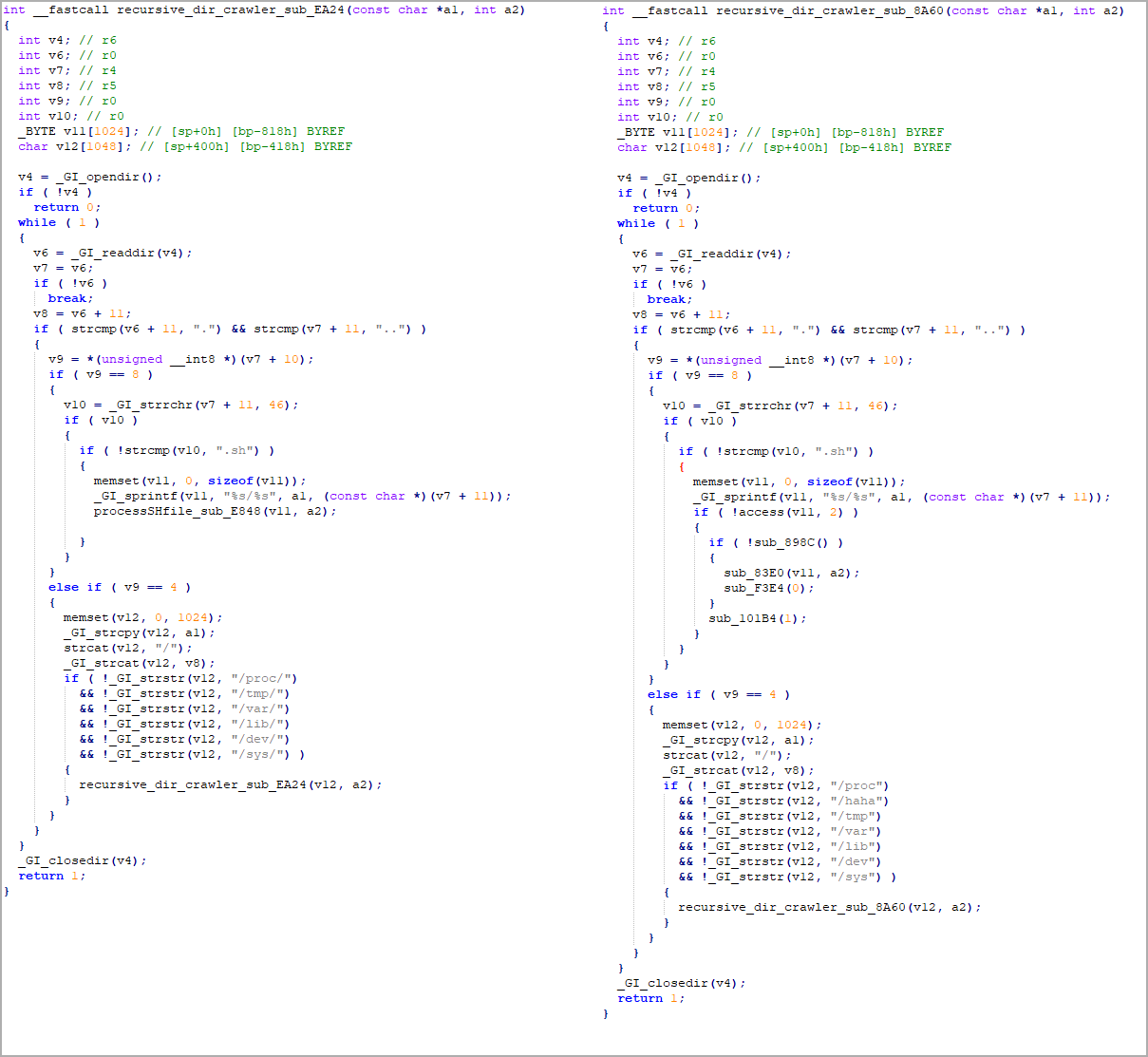 Original Mozi code (left) and kill switch payload (right) (ESET)
Original Mozi code (left) and kill switch payload (right) (ESET)This hints at the involvement of either the original botnet creators and/or Chinese law enforcement in the takedown, but for now, this remains unanswered.
Despite the good news of one of the most prolific botnets going offline, there are, unfortunately, many more DDoS malware botnets scanning the web daily for vulnerable IoTs.
Therefore, users should patch their devices using the latest firmware version, use strong passwords, and isolate them from critical networks.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·