BOOK THIS SPACE FOR AD
ARTICLE AD
Mozilla has started rolling out the Site Isolation security feature to all Firefox channels, protecting users from attacks launched via malicious websites.
Until today, Site Isolation could only be enabled by users of Firefox Nightly, the release channel used by Mozilla to test new features not yet ready for a wider rollout.
Site Isolation has been under development since April 2018 under the Project Fission codename, with Mozilla first announcing plans to add it to the Firefox web browser in February 2019.
A similar Site Isolation feature is also available in Google Chrome, first released as an experimental feature for Chrome 63 users in December 2017, and later made generally available in Chrome 67, released at the end of May 2018.
How Site Isolation works
The new Site Isolation security architecture acts as an additional security boundary between sites, and it works by completely separating users' web content, loading all sites in separate processes.
Thus it prevents malicious websites from accessing private data (including passwords, credit card numbers, or other sensitive info) loaded from other sites.
For instance, with this new feature enabled, Firefox can protect users from attackers exploiting Meltdown and Spectre vulnerabilities that allow them to harvest sensitive data by reading memory content anywhere within a process's address space.
"This fundamental redesign of Firefox’ Security architecture extends current security mechanisms by creating operating system process-level boundaries for all sites loaded in Firefox for Desktop," Mozilla engineers Anny Gakhokidze and Neha Kochar said.
"Isolating each site into a separate operating system process makes it even harder for malicious sites to read another site’s secret or private data."
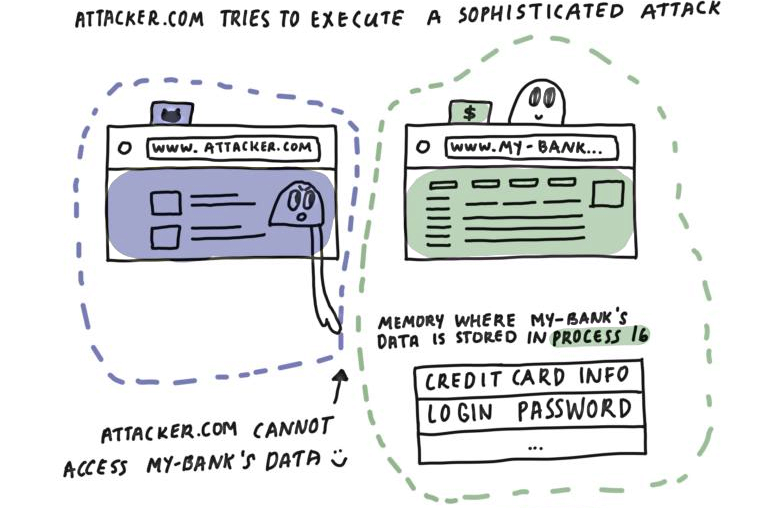 How Site Isolation works (Mozilla)
How Site Isolation works (Mozilla)Besides obvious security advantages, Site Isolation also comes with performance benefits:
By placing more pages into separate processes, we can ensure that doing heavy computation or garbage collection on one page will not degrade the responsiveness of pages in other processes. Using more processes to load websites allows us to spread work across many CPU cores and use the underlying hardware more efficiently. Due to the finer-grained separation of sites, a subframe or a tab crashing will not affect websites loaded in different processes, resulting in improved application stability and better user experience.How to enable Site Isolation
You can start testing Site Isolation right now by enabling it on any Firefox release channel, including Release, Beta, or Nightly.
To do that, you have to follow these step-by-step instructions:
To enable Site Isolation on Firefox Nightly:
Navigate to about:preferences#experimental Check the “Fission (Site Isolation)” checkbox to enable. Restart Firefox.To enable Site Isolation on Firefox Beta or Release:
Navigate to about:config. Set `fission.autostart` pref to `true`. Restart Firefox.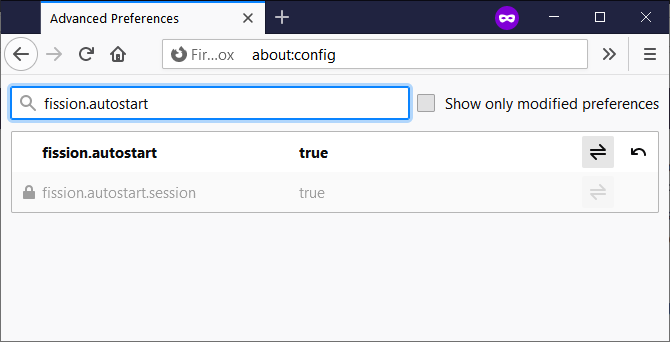 Enabling Site Isolation
Enabling Site IsolationToggling on Site Isolation is highly recommended given that it "sandboxes web pages and web frames, isolating them from each other, further strengthening Firefox security."
Once enabled, it will protect you from current and future security vulnerabilities that would allow malicious websites to access private info loaded from other sites.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·