BOOK THIS SPACE FOR AD
ARTICLE ADBeware! Cybercriminals are exploiting an open redirect vulnerability for phishing attacks that impersonate Nespresso to steal Microsoft logins. Millions of users are potentially at risk!
Perception Point, a prominent cybersecurity firm, has identified a new phishing campaign utilizing compromised accounts. This campaign targets users through an open redirect vulnerability within a domain owned by Nespresso, a well-known coffee manufacturer.
This redirect method helps threat actors bypass standard detection systems, allowing the attackers to extract Microsoft login credentials. Victims are left with a bitter aftertaste worse than their morning cup of coffee.
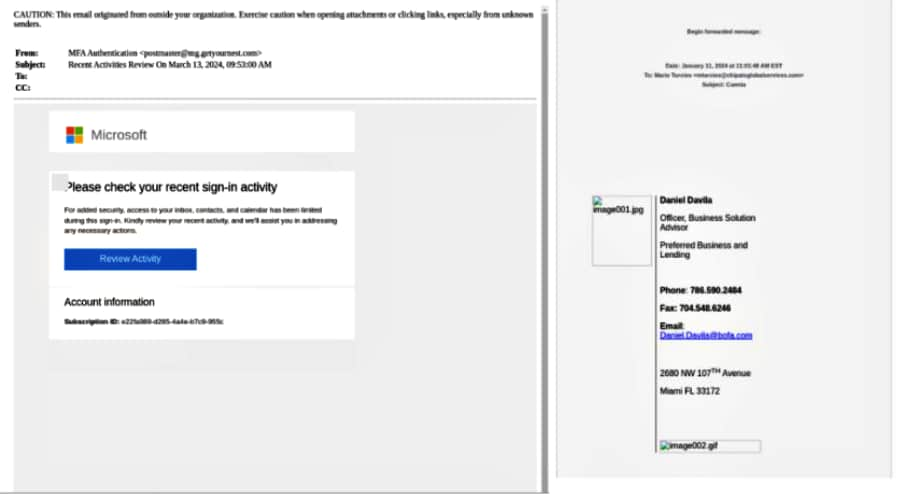
The attack starts with an email originating from a compromised account, mimicking a Microsoft multi-factor authentication request. It is worth noting that the email analysed by Perception Point came from a compromised Bank of America employee.
According to the report shared by Perception Point with Hackread.com, upon clicking the link in the email, recipients are redirected to a compromised Nespresso URL intentionally selected by the attackers due to its popularity and legitimacy.
Further, exploiting an open redirect vulnerability on the Nespresso site, the threat actor redirects users to a fake Microsoft login page. The objective? Harvesting victims’ credentials and leaving a bitter twist to their malicious brew.
Victims of this phishing attack risk losing access to various Microsoft services, including Skype, Outlook, Xbox, Microsoft 365, Family Safety, Bing Microsoft Store, and potentially even work accounts. This stolen data could be used for further phishing attempts, identity theft, or even financial fraud.
Nespresso has yet to comment on the attack, but customers are advised to be cautious when receiving emails asking for personal information. To stay safe, customers should always verify the authenticity of emails and avoid clicking on suspicious links.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·