BOOK THIS SPACE FOR AD
ARTICLE AD
The Netwalker ransomware operation has generated a total of $25 million in ransom payments since March 1st according to a new report by McAfee.
Netwalker is a Ransomware-as-a-Service (RaaS) operation that began operating in late 2019, where affiliates are enlisted to distribute the ransomware and infect victims in return for a 60-70% cut of ransom payments.
Known as a human-operated, or enterprise-targeting, ransomware, Netwalker affiliates will hack into an organization's network and quietly gain control.
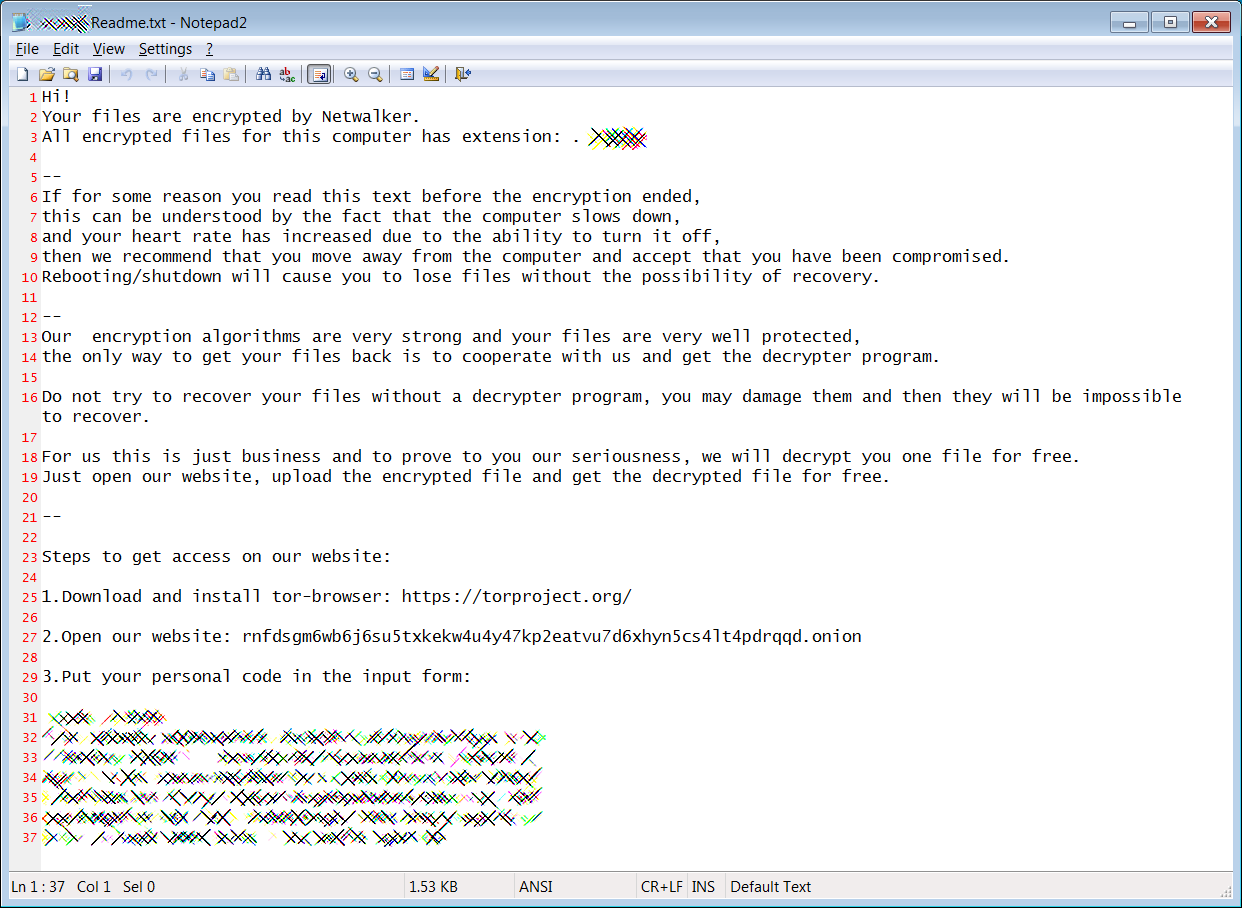 Netwalker ransom note
Netwalker ransom noteWhile gaining access to other workstations and servers, the threat actors will steal unencrypted files that are later used as leverage to get victims to pay.
Once they gain access to a network's Windows domain controller, they will deploy the ransomware to encrypt all of the devices on the network.
Building an advanced operation
When first starting, Netwalker infections were few and far between. Towards the end of April, something changed, and the operation pushed into high gear with a constant stream of new victims being reported on the ransomware identification site, ID Ransomware.
This increase in activity coincides with the Netwalker developers' recruitment drive on a Russian-speaking hacker forum where they stated they were looking for "experienced networkers with their own material."
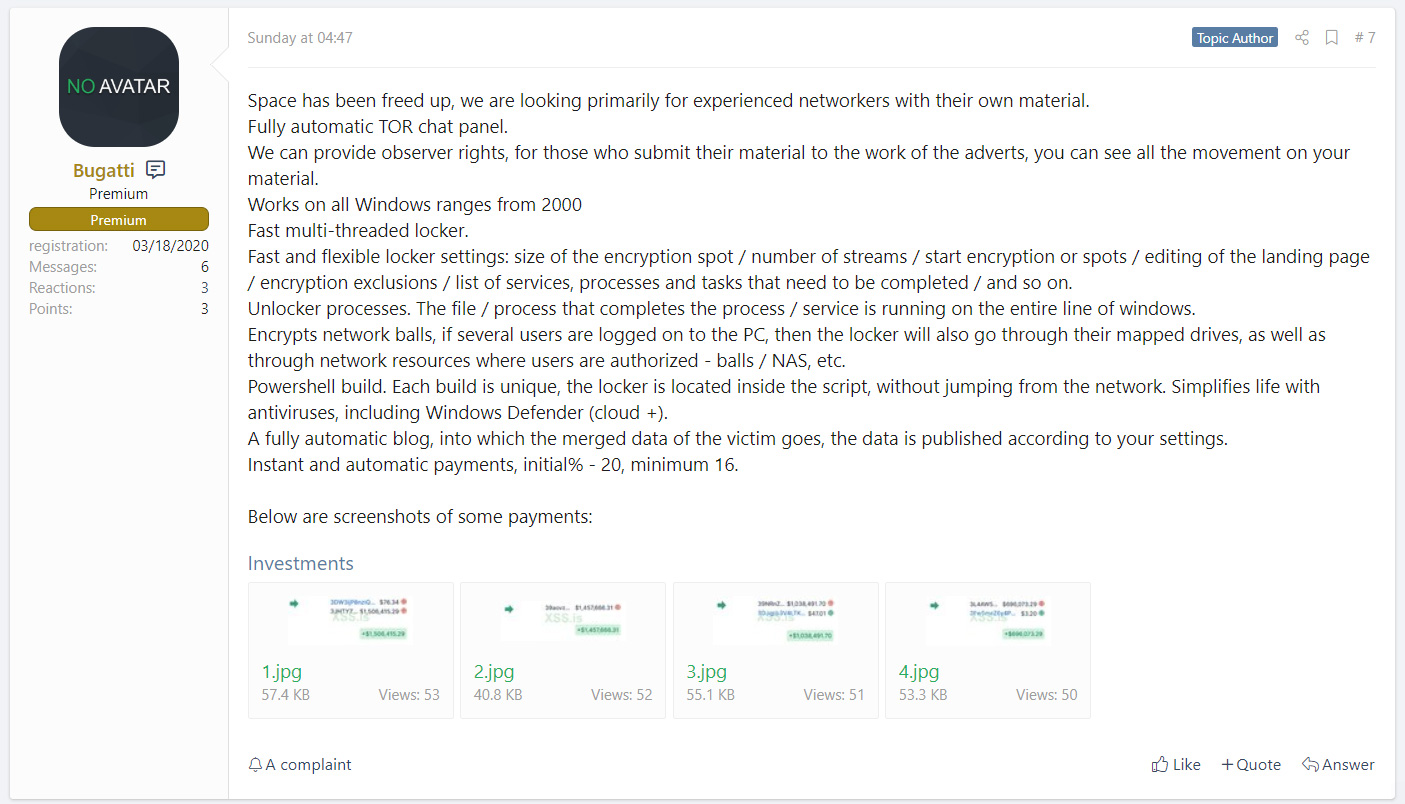 Netwalker recruitment drive
Netwalker recruitment driveTo entice experienced hackers, Netwalker provided a screenshot showing partial bitcoin addresses with large ransom payments to illustrate the amount of money they could earn.
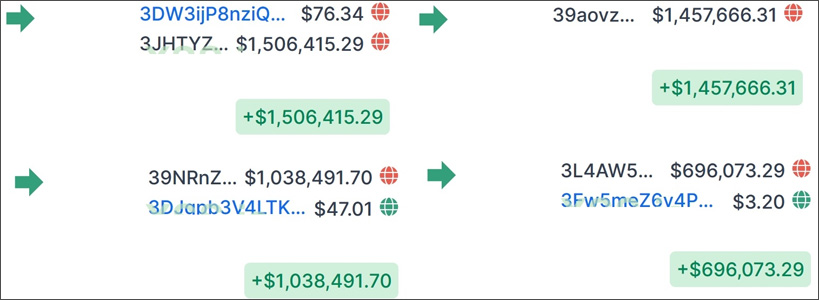 Netwalker ransom payments
Netwalker ransom paymentsAs part of their increased development, Netwalker also released an automated data leak site that allows affiliates to upload stolen data and schedule it for release at a specific date and time.
This site allows the affiliate to pressure the victim into paying the ransom with increasing anxiety as a timer counts down until the data is published.
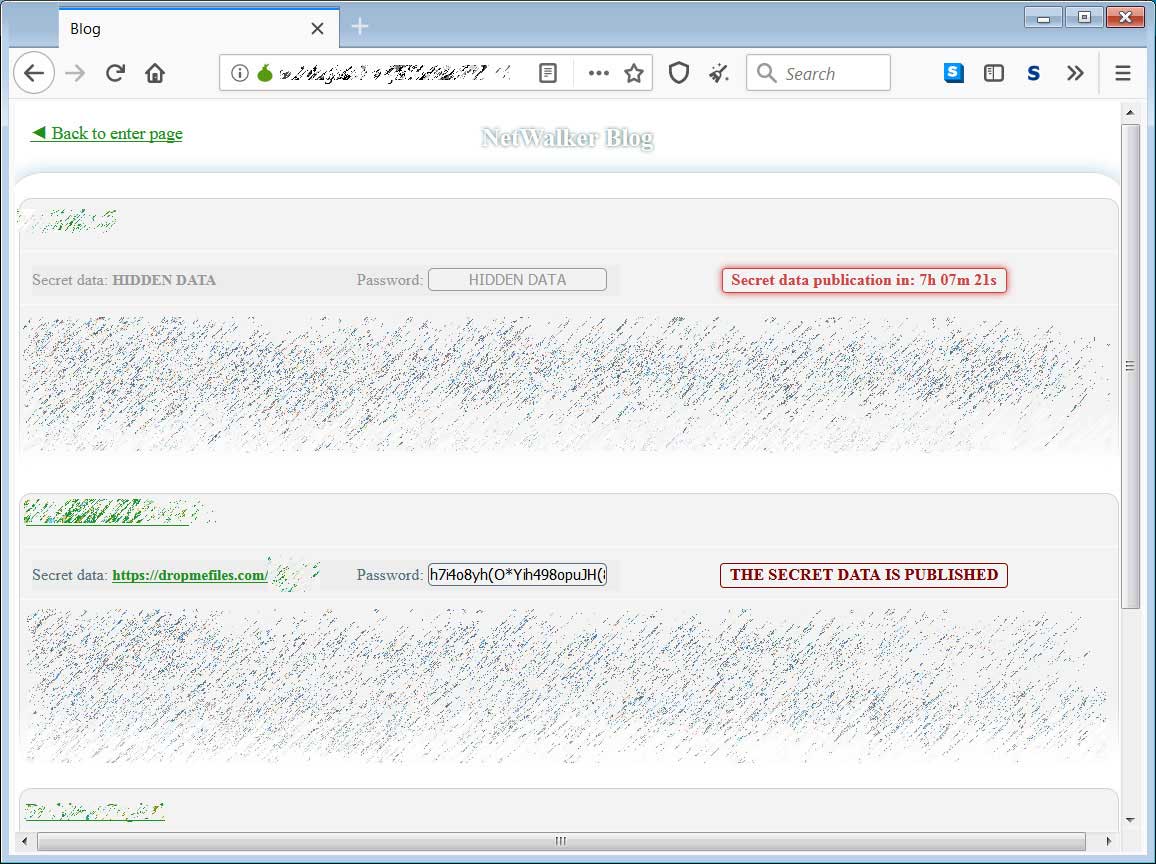 Netwalker data leak site
Netwalker data leak siteGenerated $25 million in 5 months
The recruitment drive and automated leak site must have paid off, as in a new report by McAfee it, was discovered that Netwalker generated $25 million in just five months.
After the Netwalker operator published the image of ransom payments, with the help of CipherTrace, McAfee was able to determine the full bitcoin addresses shown in the image and other associated addresses.
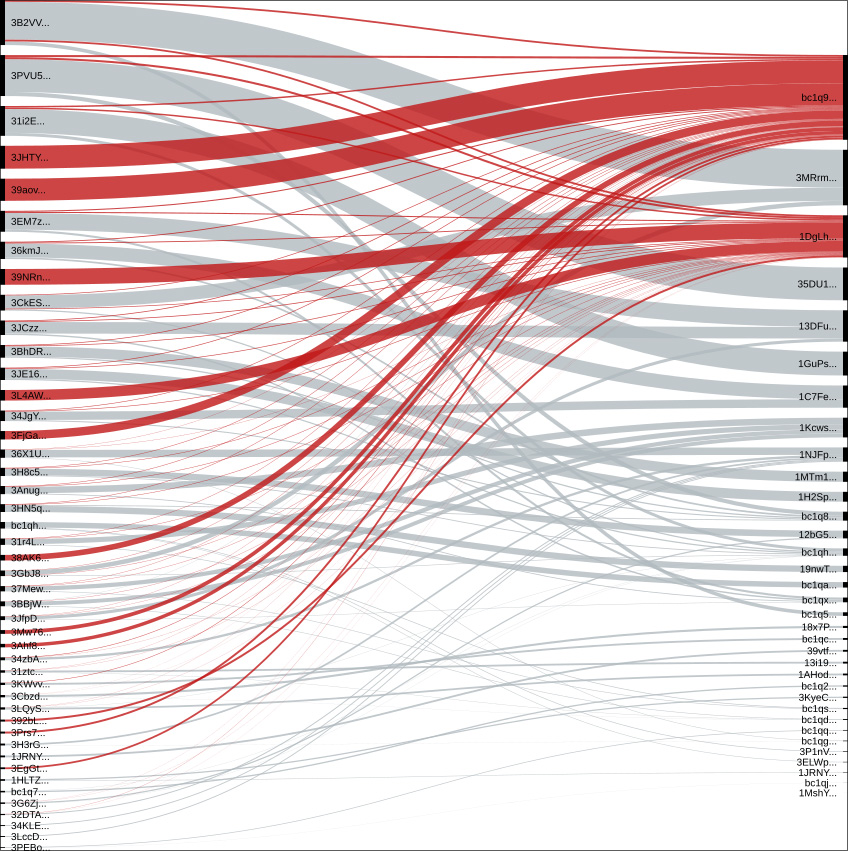 Related Netwalker bitcoin addresses
Related Netwalker bitcoin addressesBy following the transactions on these related bitcoin addresses, McAfee observed 2,795 bitcoins being transferred between related Netwalker wallets between March 1st, 2020, and July 27th,2020.
"The total amount of extorted bitcoin that has been uncovered by tracing transactions to these NetWalker related addresses is 2795 BTC between 1 March 2020 and 27 July 2020. By using historic bitcoin to USD exchange rates, we estimate a total of 25 million USD was extorted with these NetWalker related transactions," McAfee's report states.
This amount is not surprising considering the high-profile attacks that Netwalker has conducted this year:
February 2020: Australia's Toll Group suffered a major outage due to Netwalker attack May 2020: Michigan State University hit with Netwalker attack June 2020: UC San Francisco pays Netwalker $1.14 ransom July 2020: Lorien Health suffers Netwalker attack July 2020: German-based Dussmann Group discloses data breach after Netwalker attackUnfortunately, it has been all too common for organizations to pay the ransom as, in some cases, it is easier to pay a ransom then try to recover on their own.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·