A previously undocumented Android-based remote access trojan (RAT) has been found to use screen recording features to steal sensitive information on the device, including banking credentials, and open the door for on-device fraud.
Dubbed "Vultur" due to its use of Virtual Network Computing (VNC)'s remote screen-sharing technology to gain full visibility on targeted users, the mobile malware was distributed via the official Google Play Store and masqueraded as an app named "Protection Guard," attracting over 5000 installations. Banking and crypto-wallet apps from entities located in Italy, Australia, and Spain were the primary targets.
"For the first time we are seeing an Android banking trojan that has screen recording and keylogging as the main strategy to harvest login credentials in an automated and scalable way," researchers from ThreatFabric said in a write-up shared with The Hacker News.
"The actors chose to steer away from the common HTML overlay development we usually see in other Android banking Trojans: this approach usually requires a larger time and effort investment from the actors to create multiple overlays capable of tricking the user. Instead, they chose to simply record what is shown on the screen, effectively obtaining the same end result."
While banking malware such as MysteryBot, Grandoreiro, Banker.BR, and Vizom have traditionally relied on overlay attacks — i.e., creating a false version of the bank's login page and overlaying it on top of the legitimate app — to trick victims into revealing their passwords and other important private information, evidence is mounting that threat actors are pivoting away from this approach.
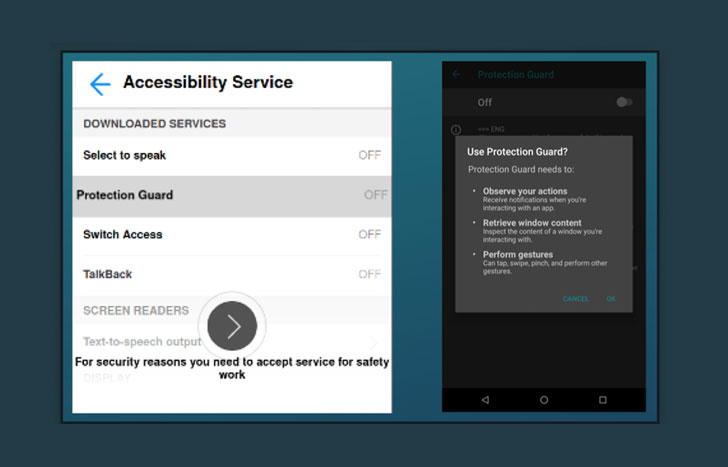
In a report published earlier this week, Italian cybersecurity firm Cleafy uncovered UBEL, an updated variant of Oscorp, that was observed using WebRTC to interact with the compromised Android phone in real-time. Vultur adopts a similar tactic in that it takes advantage of accessibility permissions to capture keystrokes and leverages VNC's screen recording feature to stealthily log all activities on the phone, thus obviating the need to register a new device and making it difficult for banks to detect fraud.
What's more, the malware employs ngrok, a cross-platform utility used to expose local servers behind NATs and firewalls to the public internet over secure tunnels, to provide remote access to the VNC server running locally on the phone. Additionally, it also establishes connections with a command-and-control (C2) server to receive commands over Firebase Cloud Messaging (FCM), the results of which, including extracted data and screen captures, are then transmitted back to the server.
ThreatFabric's investigation also connected Vultur with another well-known piece of malicious software named Brunhilda, a dropper that utilizes the Play Store to distribute different kinds of malware in what's called a "dropper-as-a-service" (DaaS) operation, citing overlaps in the source code and C2 infrastructure used to facilitate attacks.
These ties, the Amsterdam-based cybersecurity services company said, indicate Brunhilda to be a privately operating threat actor that has its own dropper and proprietary RAT Vultur.
"The story of Vultur shows one more time how actors shift from using rented Trojans (MaaS) that are sold on underground markets towards proprietary/private malware tailored to the needs of this group," the researchers concluded. "These attacks are scalable and automated since the actions to perform fraud can be scripted on the malware backend and sent in the form of commands sequence, making it easy for the actor(s) to hit-and-run."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
199
3 years ago
199 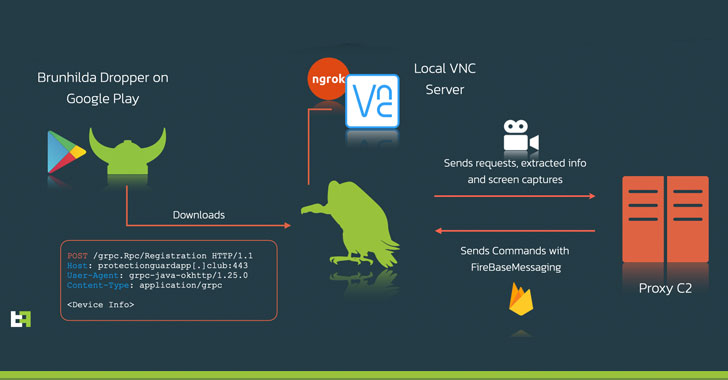

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·