BOOK THIS SPACE FOR AD
ARTICLE ADPakistan-linked Transparent Tribe (aka APT 36, Operation C-Major) disguises CapraRAT, an Android spyware, as popular apps to steal your data. Learn how to protect yourself from these scams.
Cybersecurity researchers at SentinelLabs have uncovered a new wave of Android spyware linked to the Pakistan-aligned hacking group Transparent Tribe (aka APT 36, Operation C-Major).
Researchers have discovered four new CapraRAT APKs (Android application packages) linked to the actor, all installing CapraRAT, a highly invasive spyware that grants attacker control over Android device data. The malware masquerades as seemingly innocuous apps- Crazy Games, S*xy Videos, Weapons, and TikTok.
This demonstrates that the group has expanded its target audience to include mobile gamers, weapons enthusiasts, and TikTok users, marking a significant shift from their previous focus on Indian government and military personnel.
According to SentinelLabs’ blog post, tesearchers also found that the actor continues to embed spyware into curated video browsing applications after updating the underlying code for modern Android devices while keeping the main functionality the same.
For your information, in September 2023, SentinelLabs discovered three APKs linked to Transparent Tribe’s CapraRAT mobile remote access trojan. These apps, while mimicking YouTube’s appearance, were less fully featured than the legitimate Android YouTube application.
The S*xy Videos app: The S*xy Videos app launches YouTube with a query related to the app’s theme and similarly the TikTok app launches YouTube with the query “Tik Toks,” while the Weapons app launches the Forgotten Weapons YouTube channel, which reviews classic arms and has 2.7 million subscribers. This follows the previous campaign’s use of a romance-themed social engineering pretext with one APK called Piya Sharma, launching YouTube with no query.
The Crazy Games app: The Crazy Games app is a surveillance tool, requiring users to grant risky permissions, including accessing GPS location, managing network state, reading and sending SMS, reading contacts, recording audio and screen, storage read and write access, using the camera, and viewing call history, etc.
The latest CapraRAT versions utilize WebView to launch URLs to YouTube or CrazyGames, without any indication of weaponization, as it doesn’t require key CapraRAT permissions like SMS, calls, contacts, or audio/video recording.
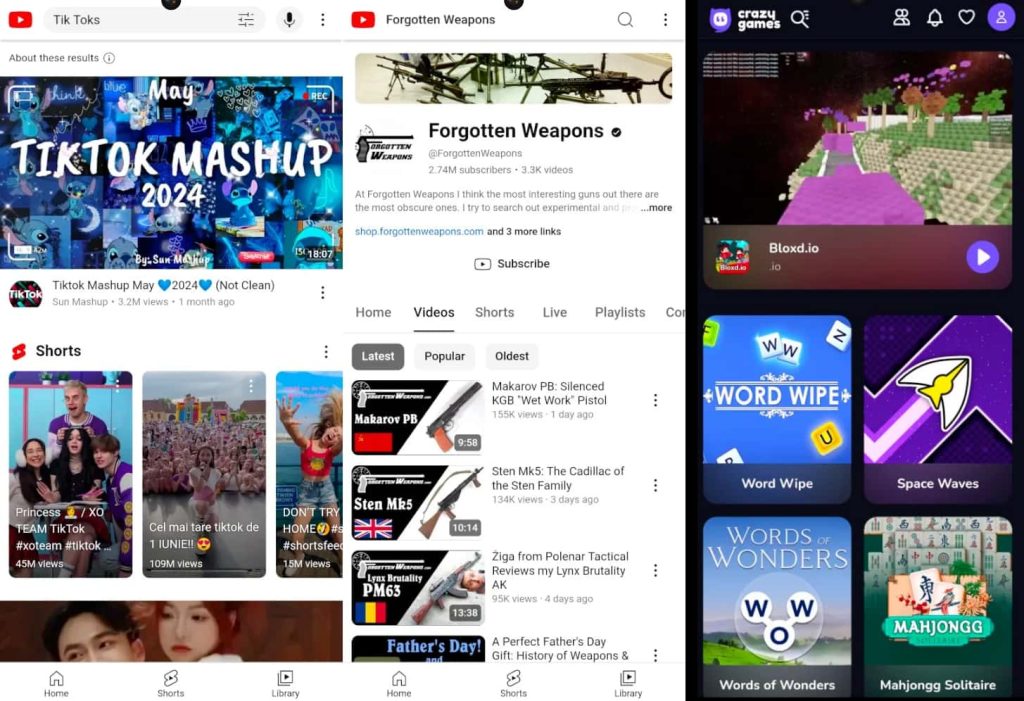 TikTok and Weapons-themed CapraRAT YouTube WebView (left) – Crazy Games CapraRAT WebView (right) – Screenshot: SentinelLabs
TikTok and Weapons-themed CapraRAT YouTube WebView (left) – Crazy Games CapraRAT WebView (right) – Screenshot: SentinelLabs“The new CapraRAT packages also contain a very minimal new class called WebView, which is responsible for maintaining compatibility with older versions of Android via the Android Support Library, which developers can choose to include in a project to enhance compatibility,” researchers noted.
CapraTube remix campaign targets individuals who download apps from untrusted sources. To stay safe, prefer official stores like Google Play, scrutinize app permissions, read independent reviews before downloading an unfamiliar app, and install and maintain a reputable security solution on your Android device.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·