BOOK THIS SPACE FOR AD
ARTICLE AD
A team of security researchers has disclosed new side-channel vulnerabilities in modern Apple processors that could steal sensitive information from web browsers.
The Georgia Institute of Technology and Ruhr University Bochum researchers, who presented another attack dubbed 'iLeakage' in October 2023, presented their new findings in two separate papers, namely FLOP and SLAP, which show distinct flaws and ways to exploit them.
The flaws stem from faulty speculative execution implementation, the underlying cause of notorious attacks like Spectre and Meltdown.
The FLOP and SLAP side-channel attacks target features aimed at speeding up processing by guessing future instructions instead of waiting for them can leave traces in memory to extract sensitive information.
"Starting with the M2/A15 generation, Apple CPUs attempt to predict the next memory address that will be accessed by the core," explained the researchers to BleepingComputer.
"Moreover, starting with the M3/A17 generation, they attempt to predict the data value that will be returned from memory. However, mispredictions in these mechanisms can result in arbitrary computations being performed on out-of-bounds data or wrong data values."
These mispredictions can have real-world security implications, such as escaping the web browser sandbox and reading cross-origin personally identifiable information on Safari and Chrome, as demonstrated in the two papers.
The attacks are executed remotely through a web browser using a malicious webpage containing JavaScript or WebAssembly code designed to trigger them.
The researchers disclosed the flaws to Apple on March 24, 2024 (SLAP) and September 3, 2024 (FLOP).
Apple acknowledged the shared proof-of-concept and stated it plans to address the issues. However, at the time of writing, the flaws remain unmitigated.
FLOP
The first paper describes False Load Output Prediction (FLOP), a problem with Apple's latest M3, M4, and A17 processors, which predict not just the memory addresses they will access but even the actual values stored in memory.
If those Load Value Prediction (LVP) guesses are wrong, incorrect data is used for temporary computations, which attackers can exploit to leak sensitive information.
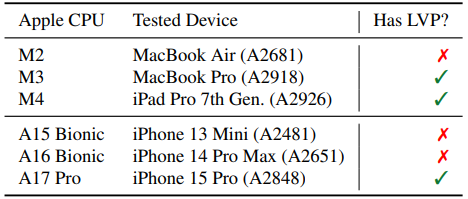 Apple CPUs vulnerable to FLOP attacks
Apple CPUs vulnerable to FLOP attacksSource: flop.fail
The researchers demonstrated the FLOP attack by tricking Apple's M3 CPU into making wrong guesses after training it via an execution loop that loads a specific constant value and then triggers a misprediction.
While the CPU remains in this incorrect state, it leaks data through a cache timing attack. This leak lasts long enough for the researchers to measure memory access times and deduce the secret value before the CPU corrects itself.
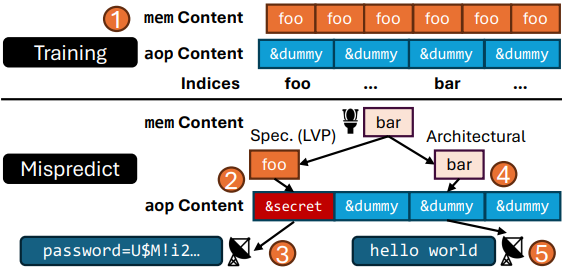 Overview of the attack
Overview of the attackSource: flop.fail
Through FLOP, the researchers demonstrated escaping Safari's sandbox, retrieving sender and subject information from Proton Mail inbox, stealing Google Maps location history, and recovering private events from iCloud Calendar.
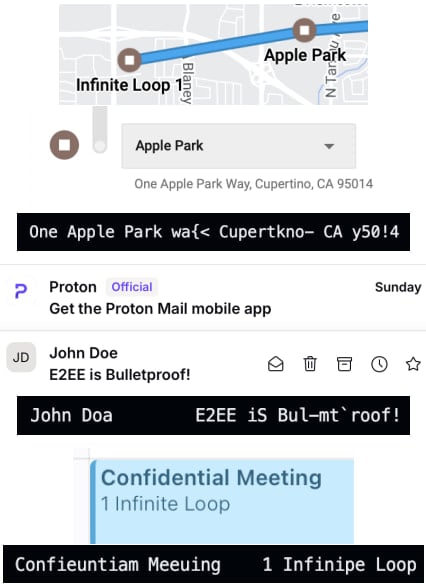 Leaking data via FLOP
Leaking data via FLOPSource: flop.fail
SLAP
The second paper describes Speculative Load Address Prediction (SLAP), which impacts Apple's M2 and A15 processors, and many of the later models.
Instead of FLOP, which is guessing what value a memory load will return, SLAP concerns the prediction of the memory address that will be accessed next, called Load Address Prediction (LAP).
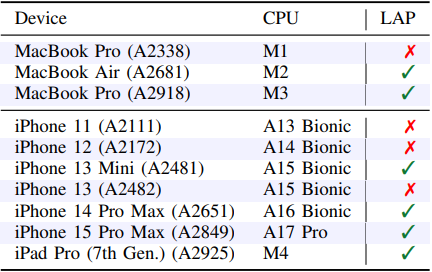 Apple CPUs supporting LAP
Apple CPUs supporting LAPSource: slap.fail
An attacker can "train" the CPU to anticipate a specific memory access pattern, then manipulate it into accessing secret data by abruptly altering the memory layout, causing the following prediction to point to the secret.
The CPU, trusting its prediction, reads and processes the sensitive data before realizing and correcting the mistake, allowing an attacker to exploit cache timing or other side channels to infer the leaked data.
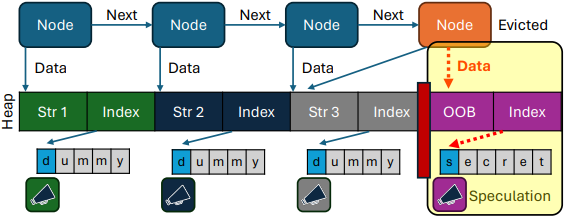 Overview of the SLAP attack
Overview of the SLAP attackSource: slap.fail
By executing the SLAP attack repeatedly, the attacker can reconstruct stolen information such as retrieving Gmail inbox data, Amazon orders and browsing data, and Reddit user activity.
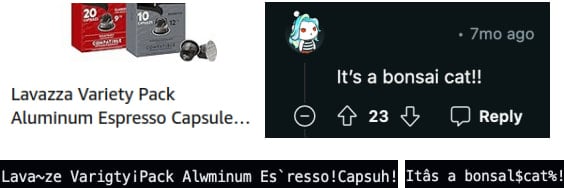 Secrets retrieved via SLAP
Secrets retrieved via SLAPSource: slap.fail
Real-world implications
The FLOP and SLAP attacks are significant due to their impact on modern and widely used hardware and because they can be executed remotely without requiring physical access.
A victim would just need to visit a malicious website for the secrets to leak, bypassing browser sandboxing, ASLR, and traditional memory protections.
The scripts used in the demo websites execute a sequence of memory loads designed to manipulate Apple's FLOP and SLAP, so no malware infection is required. Modern browsers allow advanced computation, effectively serving as attack tools in this case.
Until security updates from Apple are made available, a possible mitigation would be to turn off JavaScript in Safari and Chrome, though this will expectedly break many websites.
BleepingComputer contacted Apple to request a comment on the researchers' findings, but we are still waiting for a response.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·