BOOK THIS SPACE FOR AD
ARTICLE AD
Security researchers found a new class of DNS vulnerabilities impacting major DNS-as-a-Service (DNSaaS) providers that could allow attackers to access sensitive information from corporate networks.
DNSaaS providers (also known as managed DNS providers) provide DNS renting services to other organizations that do not want to manage and secure yet another network asset on their own.
As revealed at the Black Hat security conference by cloud security firm Wiz researchers Shir Tamari and Ami Luttwak, these DNS flaws provide threat actors with nation-state intelligence harvesting capabilities with a simple domain registration.
From domain name registration to wiretapping traffic indiscriminately
The exploitation process is quite simple, as they explained: they registered a domain and used it to hijack a DNSaaS provider's nameserver (in their case, Amazon Route 53) which enabled them to wiretap on dynamic DNS traffic streaming from Route 53 customers' networks.
"We found a simple loophole that allowed us to intercept a portion of worldwide dynamic DNS traffic going through managed DNS providers like Amazon and Google," the Wiz researchers said.
"The dynamic DNS traffic we 'wiretapped' came from over 15,000 organizations, including Fortune 500 companies, 45 U.S. government agencies, and 85 international government agencies."
The data they harvested this way ranged from employee/computer names and locations to highly sensitive details regarding organizations' infrastructure, including Internet-exposed network devices.
In one case, the researchers mapped the office locations of one of the world's largest services companies using network traffic received from 40,000 corporate endpoints.
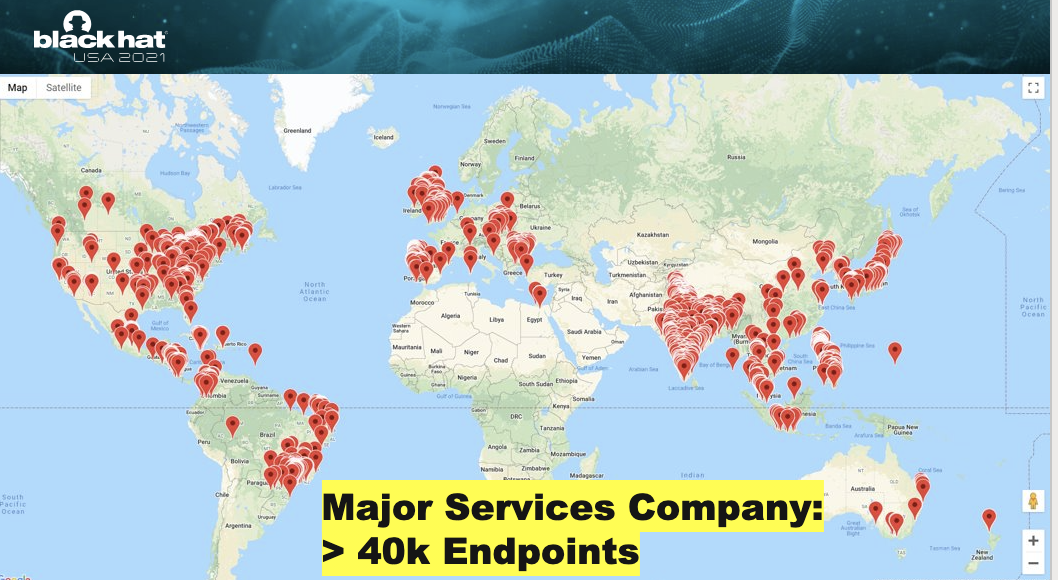 Image: Wiz
Image: WizThe information collected this way would make threat actors' job of breaching an organization's network a lot easier as it will give them "a bird's eye view on what's happening inside companies and governments" and provide them with "nation-state level spying capability."
The researchers haven't found evidence that the DNS vulnerability they uncovered was previously exploited in the wild before, but, as they explain, anyone with knowledge of the issues and the skills to abuse it "could have collected data undetected for over a decade."
"The impact is huge. Out of six major DNSaaS providers we examined, three were vulnerable to nameserver registration," they added at Black Hat.
"Any cloud provider, domain registrar, and website host who provides DNSaaS could be vulnerable."
Fixed by some, likely plaguing others
What makes things even worse, while two of the major DNS providers (Google and Amazon) have already fixed these DNS flaws, others are still likely vulnerable, exposing millions of devices to attacks.
Furthermore, it's not precisely clear who should fix this critical DNS bug. Microsoft, who could tweak the dynamic DNS algorithm which allows Windows endpoints to leak internal network traffic to malicious DNS servers, already told Wiz that this is not a vulnerability.
As Microsoft explained, this flaw is "a known misconfiguration that occurs when an organization works with external DNS resolvers."
Redmond advises using separate DNS names and zones for internal and external hosts to avoid DNS conflicts and network issues, and provides detailed documentation on how to properly configure DNS dynamic updates in Windows.
Managed DNS providers can fix the nameserver hijacking issue by correctly following RFC's "reserved names" spec, as well as verifying ownership and validating domains before allowing their customers to register them.
Companies renting DNS servers can also make changes to block their internal network traffic from leaking via dynamic DNS updates by modifying the default Start-of-Authority (SOA) record.
Additional information and technical details are available in the report published by Wiz on Wedneday, and Black Hat presentation slides are available here.
.png)














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·