A sweeping probe into a data leak of more than 50,000 phone numbers has revealed an extensive misuse of Israeli company NSO Group's Pegasus "military-grade spyware" to facilitate human rights violations by surveilling heads of state, activists, journalists, and lawyers around the world.
Dubbed the "Pegasus Project," the investigation is a collaboration by more than 80 journalists from a consortium of 17 media organizations in 10 countries coordinated by Forbidden Stories, a Paris-based media non-profit, along with the technical support of Amnesty International.
"The Pegasus Project lays bare how NSO's spyware is a weapon of choice for repressive governments seeking to silence journalists, attack activists and crush dissent, placing countless lives in peril," Amnesty International's Secretary-General, Agnès Callamard, said.
"These revelations blow apart any claims by NSO that such attacks are rare and down to rogue use of their technology. While the company claims its spyware is only used for legitimate criminal and terror investigations, it's clear its technology facilitates systemic abuse. They paint a picture of legitimacy, while profiting from widespread human rights violations," Callamard added.
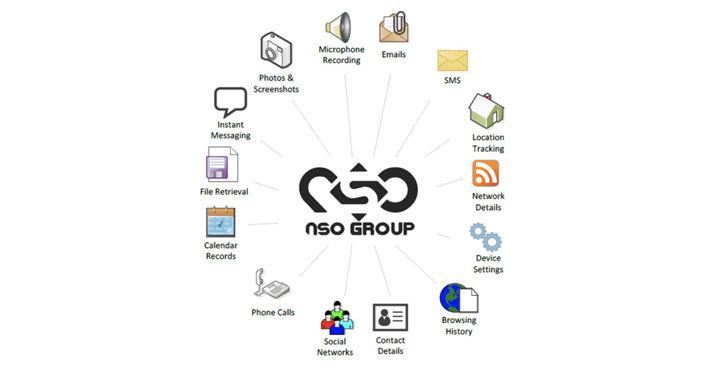
NSO Group is the maker of a cyber-surveillance weapon called "Pegasus," which, when surreptitiously installed on victims' iPhone and Android devices, enables an attacker to harvest emails, SMS messages, media, calendars, calls, and contact information, as well as chat content from messaging apps like WhatsApp, Telegram and Signal, and stealthily activate the phone's microphone and camera.
The tool, which is sold by the surveillance vendor to governments worldwide, is typically installed by either exploiting previously unknown security vulnerabilities in common apps or by tricking a potential target into clicking a malicious link. NSO Group calls itself "the world leader in precision cyber intelligence solutions for the sole use of vetted-and-approved, state-administered intelligence and law enforcement agencies."
The list of phone numbers, while not including the names, is said to contain hundreds of business executives, religious figures, academics, NGO employees, union officials, and government officials, with the probe uncovering NSO Group clients in at least 11 countries, including Azerbaijan, Bahrain, Hungary, India, Kazakhstan, Mexico, Morocco, Rwanda, Saudi Arabia, Togo, and the U.A.E.
The investigation has so far identified 180 journalists and more than 600 politicians and government officials, spanning across more than 50 countries, even as the timeline of the attacks spread over a seven-year period from 2014 up to as recently as July 2021. However, Rwanda, Morocco, India, and Hungary denied having used Pegasus to hack the phones of the individuals named in the list.
Troublingly, a forensic analysis of 67 mobile devices showed the intrusions involved the ongoing use of so-called "zero-click" exploits — which do not require any interaction from the target — since May 2018. In one instance highlighted by Amnesty International, the compromise is believed to have leveraged multiple zero-days in iMessage to attack a fully patched iPhone 12 running iOS 14.6 in July 2021.
"All this indicates that NSO Group can break into the latest iPhones," Citizen Lab's Bill Marczak said in a series of tweets. "It also indicates that Apple has a MAJOR blinking red five-alarm-fire problem with iMessage security that their BlastDoor Framework (introduced in iOS 14 to make zero-click exploitation more difficult) ain't solving."
Of the tested smartphones, 23 devices had been successfully infected with Pegasus, and 15 exhibited signs of attempted penetration, the Washington Post said in an in-depth report.
"The coming week's stories about the global hacking of phones identical to the one in your pocket, by for-profit companies, make it clear that export controls have failed as a means to regulate this industry," U.S. whistleblower Edward Snowden tweeted. "Only a comprehensive moratorium on sales can remove the profit motive."
This is far from the first time NSO Group's phone-penetrating spy software has been used to target human rights activists and journalists. In October 2019, Facebook-owned WhatsApp revealed that at least two dozen academics, lawyers, Dalit activists, and journalists in India were the target of unlawful surveillance by taking advantage of a then-unpatched vulnerability in the messaging service.
WhatsApp has since taken the company to court in the U.S., citing evidence that "the attackers used servers and Internet-hosting services that were previously associated with NSO."
For its part, the Israeli company flatly disputed the allegations, stating it's "full of wrong assumptions and uncorroborated theories that raise serious doubts about the reliability and interests of the sources," while stressing that it's on a "life-saving mission" to "break up pedophilia rings, sex and drug-trafficking rings, locate missing and kidnapped children, locate survivors trapped under collapsed buildings, and protect airspace against disruptive penetration by dangerous drones."
"After checking their claims, we firmly deny the false allegations made in their report," the company added. "Their sources have supplied them with information which has no factual basis, as evident by the lack of supporting documentation for many of their claims. In fact, these allegations are so outrageous and far from reality, that NSO is considering a defamation lawsuit."
The latest development also comes days after another Israeli company called Candiru was outed as the commercial spyware vendor behind the exploitation of a number of zero-day flaws in Google Chrome and Microsoft Windows in a series of "precision attacks" to hack more than 100 journalists, academics, activists, and political dissidents globally.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
249
3 years ago
249 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·