BOOK THIS SPACE FOR AD
ARTICLE ADA recent analysis published by Infoblox reveals a sophisticated phishing operation, dubbed Morphing Meerkat, actively exploiting DNS vulnerabilities for years to conduct highly effective phishing campaigns.
According to researchers, this operation utilizes a phishing-as-a-service (PhaaS) platform, enabling both technical and non-technical cybercriminals to launch targeted attacks.
The platform is equipped with tools to bypass security systems, including the exploitation of open redirects on adtech servers, redirection through compromised WordPress websites, and the use of DNS MX records to identify victim email service providers. Also, they use mass spam delivery and dynamic content tailoring to evade traditional security measures.
“We have discovered a phishing kit that creatively employs DNS mail exchange (MX) records to dynamically serve fake, tailored, login pages, spoofing over 100 brands,” researchers noted in the blog post, shared with Hackread.com ahead of its release.
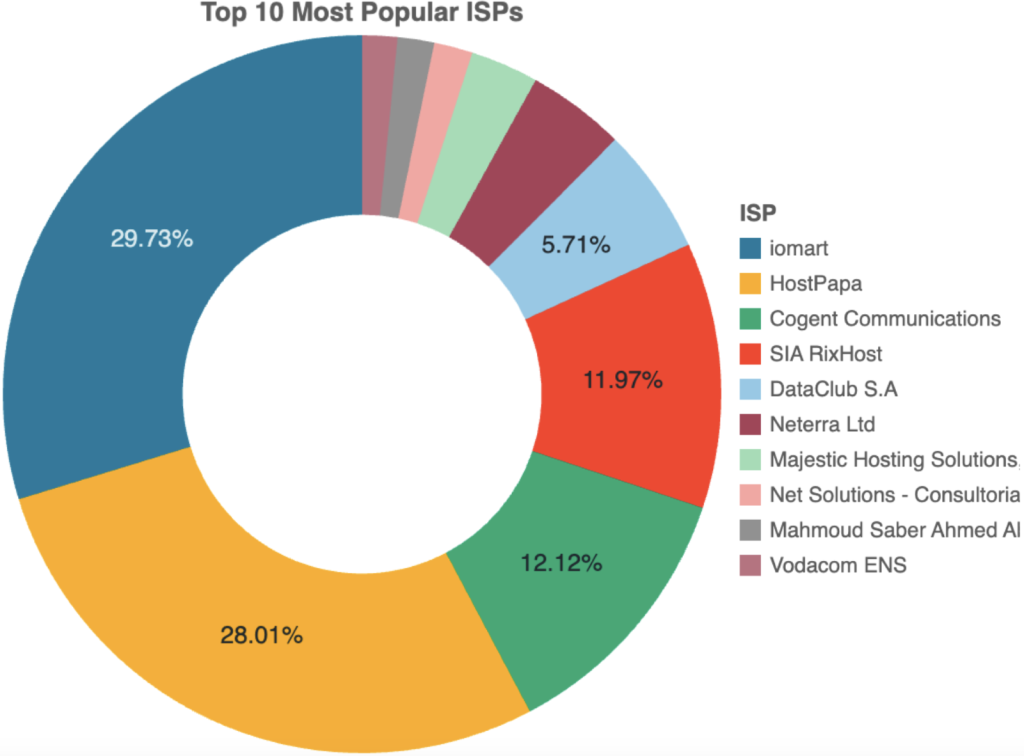
Regarding the distribution of spam emails, the platform’s primary attack vector, researchers observed a distinct centralization pattern, with a considerable portion originating from servers hosted by iomart (United Kingdom) and HostPapa (United States), indicating a unified network rather than dispersed activity from multiple independent entities.
Morphing Meerkat uses a dynamic serving of fake login pages customized to the victim’s email service provider by querying DNS MX records using Cloudflare DoH or Google Public DNS. The platform maps these records to corresponding phishing HTML files, featuring over 114 unique brand designs, ensuring a personalized phishing experience and increasing the likelihood of successful credential theft.
The operation has evolved significantly since its detection in January 2020. Initially, it targeted only five email brands (Gmail, Outlook, AOL, Office 365, and Yahoo) and lacked translation capabilities. By July 2023, it had integrated DNS MX records-based dynamic loading of phishing pages and now supports dynamic translation into over a dozen languages, including English, Korean, Spanish, Russian, German, Chinese, and Japanese.
To harvest stolen credentials, they utilize several methods, including email delivery via EmailJS, PHP scripts, AJAX requests, and communication with Telegram channels using web API hooks. The platform also implements anti-analysis measures, such as disabling keyboard shortcuts and mouse right-clicks and obfuscating code to hinder security researchers.
As Infoblox points out, “moderately advanced internet users and security researchers often verify the malicious state of a phishing webpage by examining its HTML code.” Morphing Meerkat counters this by actively blocking such inspection.
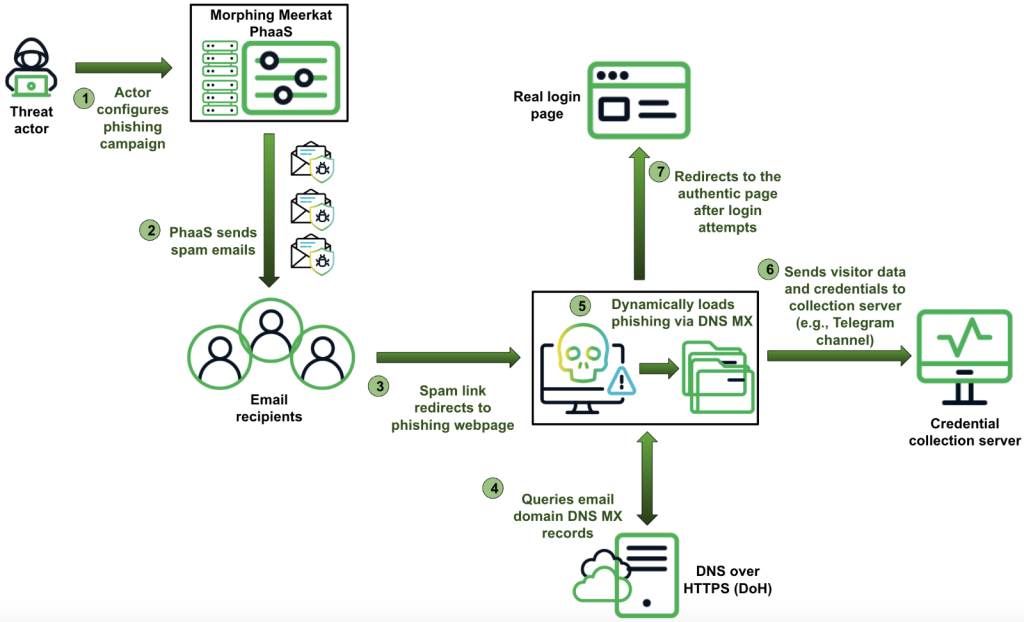 Morphing Meerkat Attack Chain (Source: Infoblox)
Morphing Meerkat Attack Chain (Source: Infoblox)
The use of open redirect vulnerabilities on adtech platforms, particularly DoubleClick, allows the threat actors to bypass email security systems by leveraging the domain’s high reputation. The platform also employs cloaking techniques, redirecting users to legitimate login pages and inflating code with non-functional elements, complicating threat analysis.
Considering the platform’s potential to exploit security blind spots through open redirects, DoH communication, and file-sharing services, it is essential that organizations strengthen DNS security, restrict DoH communication, and limit access to non-essential infrastructure to prevent exploitation.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·