BOOK THIS SPACE FOR AD
ARTICLE AD“Panamorfi,” a new DDoS attack, exploits Discord, Minecraft, and Jupyter Notebooks. Cybersecurity researchers warn of this threat targeting misconfigured Jupyter Notebooks, urging data scientists and engineers to secure their systems from potential attacks launched using the Minecraft mod “mineping.”
Cybersecurity researchers at Aqua Nautilus have discovered a new threat targeting data professionals. Dubbed ‘Panamorfi’, this attack exploits a common tool used by data scientists and engineers called Jupyter Notebooks. The attackers are misusing these notebooks to launch Distributed Denial of Service attacks (DDoS attacks), which can cripple websites and online services.
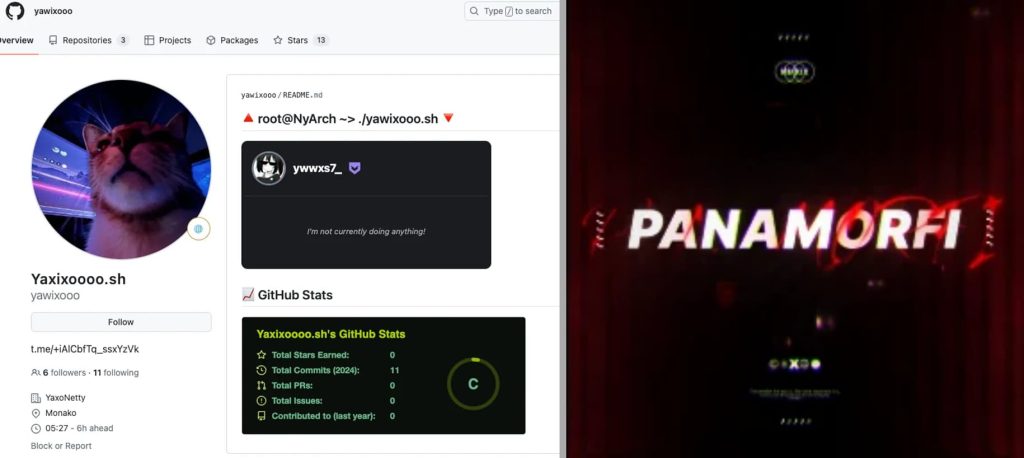
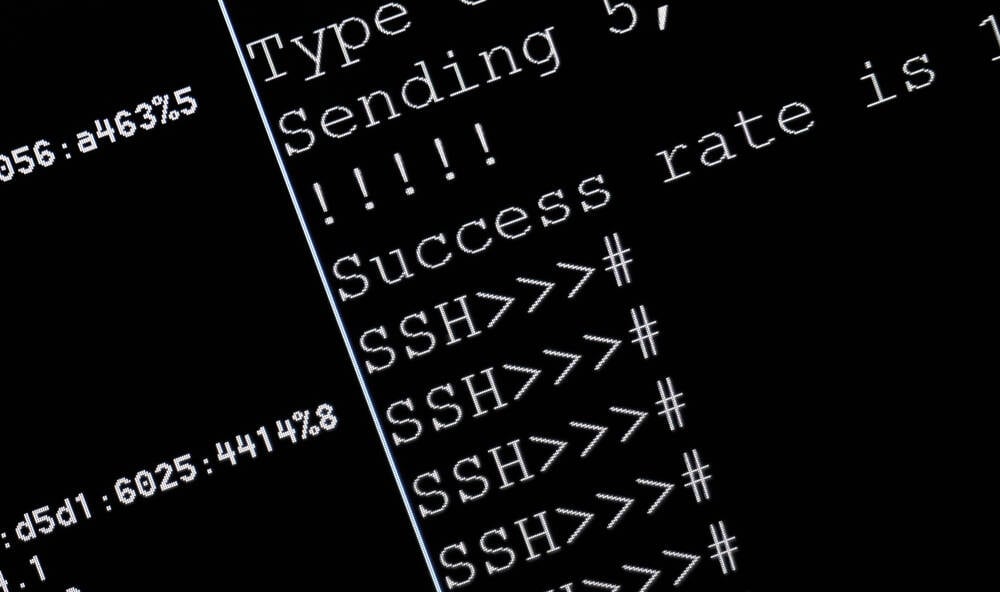
The Panamorfi attack is unique because it uses a Java-based tool originally designed for the popular game Minecraft. This tool, called ‘mineping’, is being repurposed to flood target servers with traffic, causing them to crash.
The attackers behind Panamorfi target misconfigured Jupyter notebooks that have been left vulnerable and exposed to outside access. For your information, Jupyter Notebooks are widely used by data practitioners to analyze and visualize data, with nearly 10 million available on GitHub.
However, these tools often lack proper security measures, leaving them vulnerable to exploitation. In this case, the attackers were able to gain initial access to an exposed Jupyter notebook and use it to download a malicious zip file containing two Java files.
According to Aqua Nautilus’ blog post shared with Hackread.com ahead of publishing on Friday, August 2, 2024, its researchers have identified the attacker as ‘yawixooo’ and are tracking their activity which shows that the threat actor has been using Discord to control the DDoS attack.
To protect against similar attacks, it is recommended that data practitioners take the following steps:
Ensure that Jupyter notebooks are properly secured and configured Limit the execution of code to only what is necessary for the task at hand Use security tools and solutions to detect and block malicious behavior Stay up-to-date with the latest security patches and updatesThis is not the first time Jupyter Notebooks have been exploited in a cyber attack. Last year, they were the target of a large-scale campaign where threat actors used Qubitstrike malware to steal cryptocurrency and cloud data from data scientists and researchers.
.png)











 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·