BOOK THIS SPACE FOR AD
ARTICLE ADNew Poco RAT Malware Targets Spanish Speakers Through Emails! Disguised as financial documents, Poco RAT steals your info & hijacks your computer. Learn how to stay safe and what to do if you receive a suspicious email.
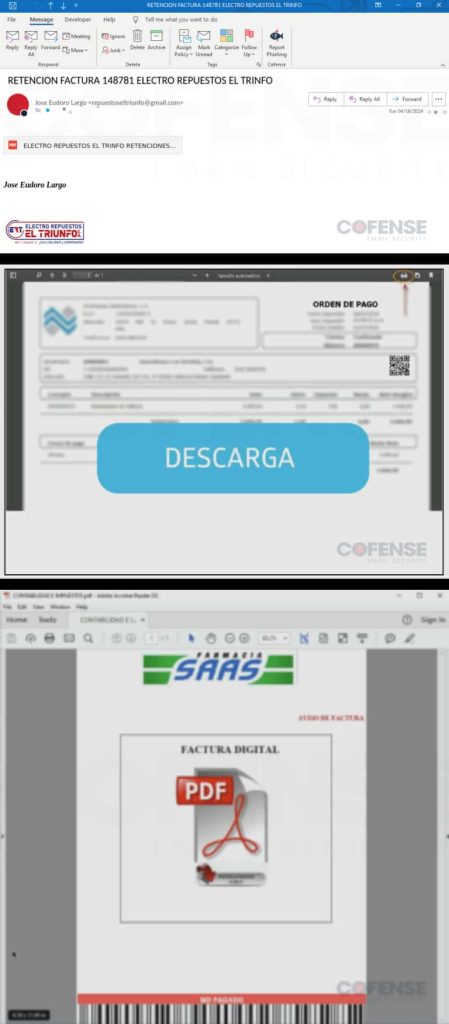
A new malware campaign has been discovered by Cofense Intelligence that specifically targets Spanish speakers. This malware, called Poco RAT, is delivered via email and is cleverly disguised as financial documents. The malicious emails contain a link to a Google Drive archive that, when clicked, downloads the malware onto the victim’s computer.
The archive can be delivered in three ways: directly in the email using a Google Drive URL (53% of emails), embedded in an HTML file (40% of emails), or attached to a PDF with a link to download from Google Drive (seen in 7% of emails). The HTML file can be either attached or downloaded via another embedded link hosted on Google Drive.
“Threat actors often use legitimate file hosting services such as Google Drive to bypass Secure Email Gateways (SEGs),” Cofense researchers explained in their report shared with Hackread.com.
Nevertheless, once downloaded, Poco RAT establishes persistence on the infected machine and injects itself into a legitimate process to remain hidden and operate undetected for extended periods.
Poco RAT then connects to a command and control (C2) server, receiving instructions from the attacker, which is always hosted on 94131119126 and connected to at least one of three ports: 6541, 6542, or 6543. Interestingly, if the infected computer appears to be from Latin America, attempts to communicate are not responded to by the C2.
For your information, Poco RAT is a Remote Access Trojan targeting Spanish language speakers using the POCO C++ Library. It was first observed in early 2024 and assigned a malware family in February 2024.
Initially delivered via embedded links to 7zip archives containing executables hosted on Google Drive, it primarily targets companies in the Mining sector (accounting for 67% of attacks) but over time it expanded operations to three more sectors, including utilities, manufacturing, and hospitality.
The malware’s custom code focuses on anti-analysis, communication with its C2 center, and downloading and running files, which makes it capable of delivering more specialized malware for information stealing or ransomware.
This malware campaign is dangerous because it can steal your financial information or take complete control of your computer. To stay safe from malware, be cautious of unsolicited emails, avoid opening emails from unknown senders, keep your software up to date, and enable two-factor authentication whenever possible.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·