Two new ransomware-as-service (RaaS) programs have appeared on the threat radar this month, with one group professing to be a successor to DarkSide and REvil, the two infamous ransomware syndicates that went off the grid following major attacks on Colonial Pipeline and Kaseya over the past few months.
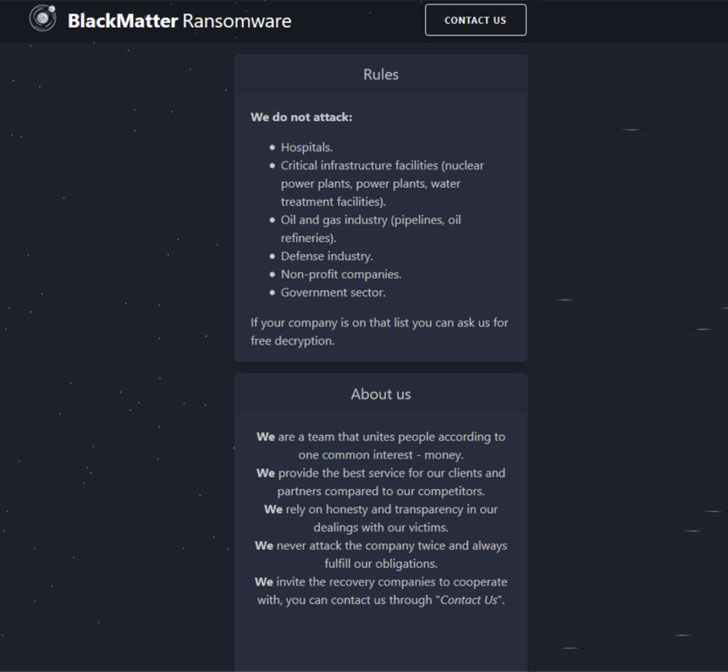
"The project has incorporated in itself the best features of DarkSide, REvil, and LockBit," the operators behind the new BlackMatter group said in their darknet public blog, making promises to not strike organizations in several industries, including healthcare, critical infrastructure, oil and gas, defense, non-profit, and government sectors.
According to Flashpoint, the BlackMatter threat actor registered an account on Russian-language forums XSS and Exploit on July 19, quickly following it up with a post stating they are looking to purchase access to infected corporate networks comprising anywhere between 500 and 15,000 hosts in the U.S., Canada, Australia, and the U.K. and with revenues of over $100 million a year, potentially hinting at a large-scale ransomware operation.
"The actor deposited 4BTC (approximately $150,000 USD) into their escrow account. Large deposits on the forum indicate the seriousness of the threat actor," Flashpoint researchers said in a report. "BlackMatter does not openly state that they are a ransomware collective operator, which technically doesn't break the rules of the forums, though the language of their post, as well as their goals clearly indicate that they are a ransomware collective operator."
On July 27, the group is said to have begun actively recruiting partners and affiliates using Exploit forum's Jabber server to promulgate their recruitment message, in which they claim to be looking for experienced penetration testers knowledgeable in Windows and Linux systems as well as initial access suppliers, who would either sell their access for a percentage of the profits.
Last month, enterprise security firm Proofpoint disclosed how ransomware gangs are increasingly buying access from independent cybercriminal groups who infiltrate major targets and then supply them with an entry point to deploy data theft and encryption operations in exchange for a slice of the ill-gotten gains.
The emergence of BlackMatter coincides with the demise of DarkSide and REvil in the wake of highly publicized ransomware incidents of Colonial Pipeline, JBS, and Kaseya, raising speculations that the groups may eventually rebrand and resurface under a new identity.
While concrete evidence connecting BlackMatter and the now-defunct groups is scant, the "similar rules around targeting" and the fact that REvil previously labeled their Windows Registry key "BlackLivesMatter" lend credence to theories that REvil may have indeed taken a temporary hiatus and gone underground after a wave of high-profile attacks.
"It is possible that copycats are intentionally mimicking the behavior of REvil to gain immediate credibility for allegedly being the reincarnation of REvil," Flashpoint said.
BlackMatter is not the only newcomer, however. South Korean security firm S2W Labs last week took the wraps off Haron, another latest entrant to the cybercrime ecosystem that made its appearance this month and heavily borrows from past ransomware variants such as Thanos and the now-discontinued Avaddon.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
281
3 years ago
281 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·