A computer retail company based in the U.S. was the target of a previously undiscovered implant called SideWalk as part of a recent campaign undertaken by a Chinese advanced persistent threat group primarily known for singling out entities in East and Southeast Asia.
Slovak cybersecurity firm ESET attributed the malware to an advanced persistent threat it tracks under the moniker SparklingGoblin, an adversary believed to be connected to the Winnti umbrella group, noting its similarities to another backdoor dubbed Crosswalk that was put to use by the same threat actor in 2019.
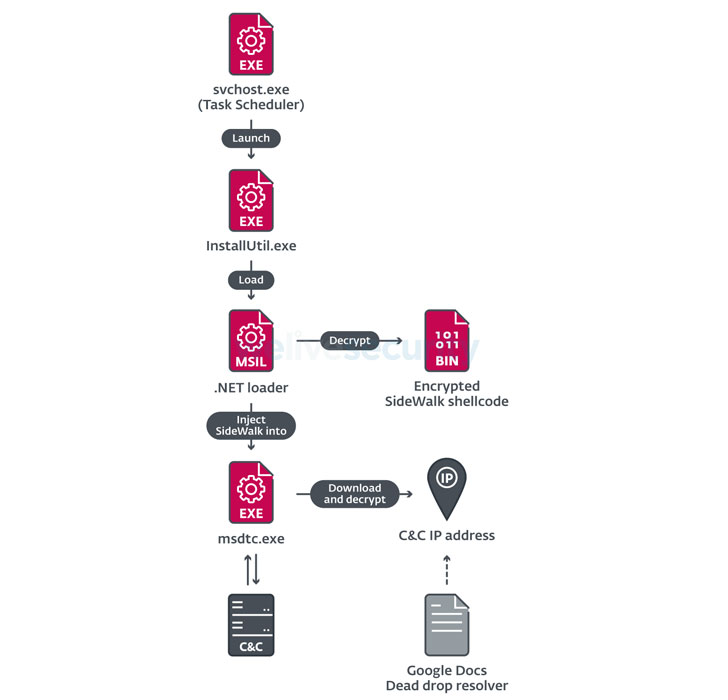
"SideWalk is a modular backdoor that can dynamically load additional modules sent from its C&C [command-and-control] server, makes use of Google Docs as a dead drop resolver, and Cloudflare workers as a C&C server," ESET researchers Thibaut Passilly and Mathieu Tartare said in a report published Tuesday. "It can also properly handle communication behind a proxy."
Since first emerging on the threat landscape in 2019, SparklingGoblin has been linked to several attacks aimed at Hong Kong universities using backdoors such as Spyder and ShadowPad, the latter of which has become a preferred malware of choice among multiple Chinese threat clusters in recent years.
Over the past year, the collective has hit a broad range of organizations and verticals around the world, with a particular focus on the academic institutions located in Bahrain, Canada, Georgia, India, Macao, Singapore, South Korea, Taiwan, and the U.S. Other targeted entities include media companies, religious organizations, e-commerce platforms, computer and electronics manufacturers, and local governments.
SideWalk is characterized as an encrypted shellcode, which is deployed via a .NET loader that takes care of "reading the encrypted shellcode from disk, decrypting it and injecting it into a legitimate process using the process hollowing technique." The next phase of the infection commences with SideWalk establishing communications with the C&C server, with the malware retrieving the encrypted IP address from a Google Docs document.
"The decrypted IP address is 80.85.155[.]80. That C&C server uses a self-signed certificate for the facebookint[.]com domain. This domain has been attributed to BARIUM by Microsoft, which partially overlaps with what we define as Winnti Group. As this IP address is not the first one to be used by the malware, it is considered to be the fallback one," the researchers said.
Besides using HTTPS protocol for C&C communications, SideWalk is designed to load arbitrary plugins sent from the server, amass information about running processes, and exfiltrate the results back to the remote server.
"SideWalk is a previously undocumented backdoor used by the SparklingGoblin APT group. It was most likely produced by the same developers as those behind CROSSWALK, with which it shares many design structures and implementation details," the researchers concluded.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
258
3 years ago
258 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·