BOOK THIS SPACE FOR AD
ARTICLE AD
A new attack called 'Browser Syncjacking' demonstrates the possibility of using a seemingly benign Chrome extension to take over a victim's device.
The new attack method, discovered by security researchers at SquareX, involves several steps, including Google profile hijacking, browser hijacking, and, eventually, device takeover.
Despite the multi-stage process, the attack is stealthy, requires minimal permissions, and almost no victim interaction other than to install what appears to be a legitimate Chrome extension.
Syncjacking phases
The attack begins with the creation of a malicious Google Workspace domain where the attacker sets up multiple user profiles with security features such as multi-factor authentication disabled. This Workspace domain will be used in the background to create a managed profile on the victim's device.
A browser extension, made to appear as a useful tool with legitimate functionality, is then published on the Chrome Web Store.
Using social engineering, the attacker tricks the victim into installing the extension, which then quietly logs them into one of the attacker's managed Google Workspace profiles in a hidden browser window running in the background.
The extension then opens a legitimate Google support page. As it has Read and Write privileges to webpages, it injects content into the page, telling the user to enable Chrome sync.
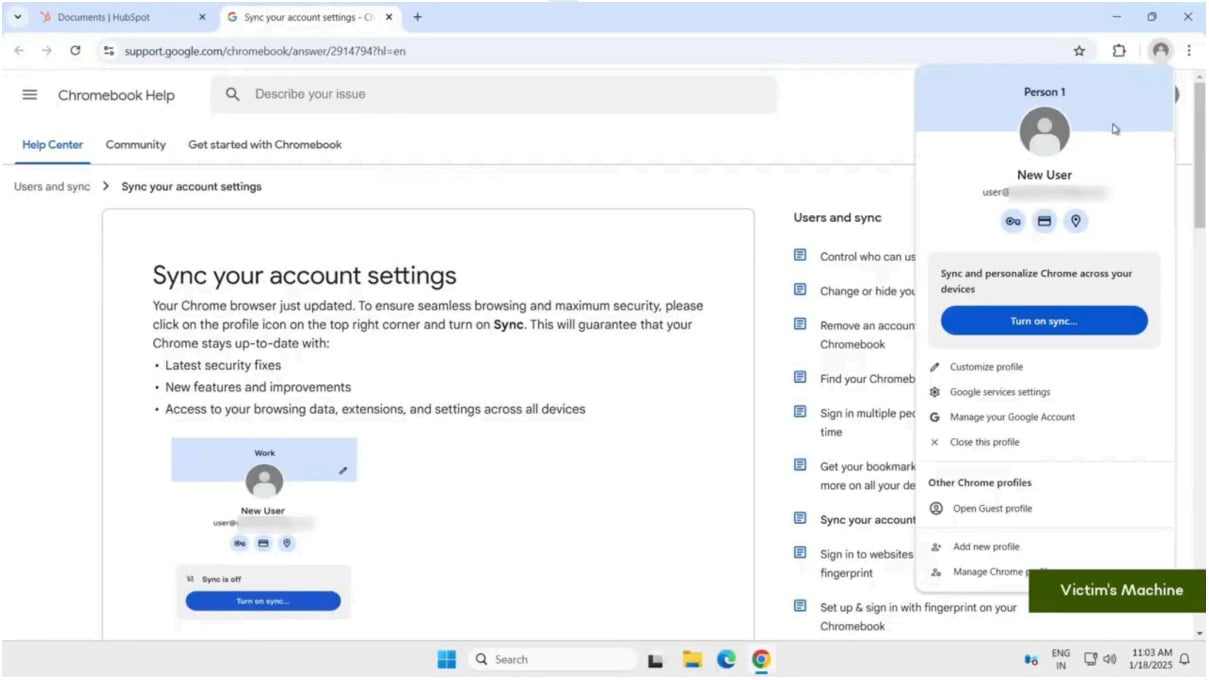 Victim opting to sync their browsing profile
Victim opting to sync their browsing profileSource: SquareX
Once synced, all stored data, including passwords and browsing history, becomes accessible to the attacker, who can now use the compromised profile on their own device.
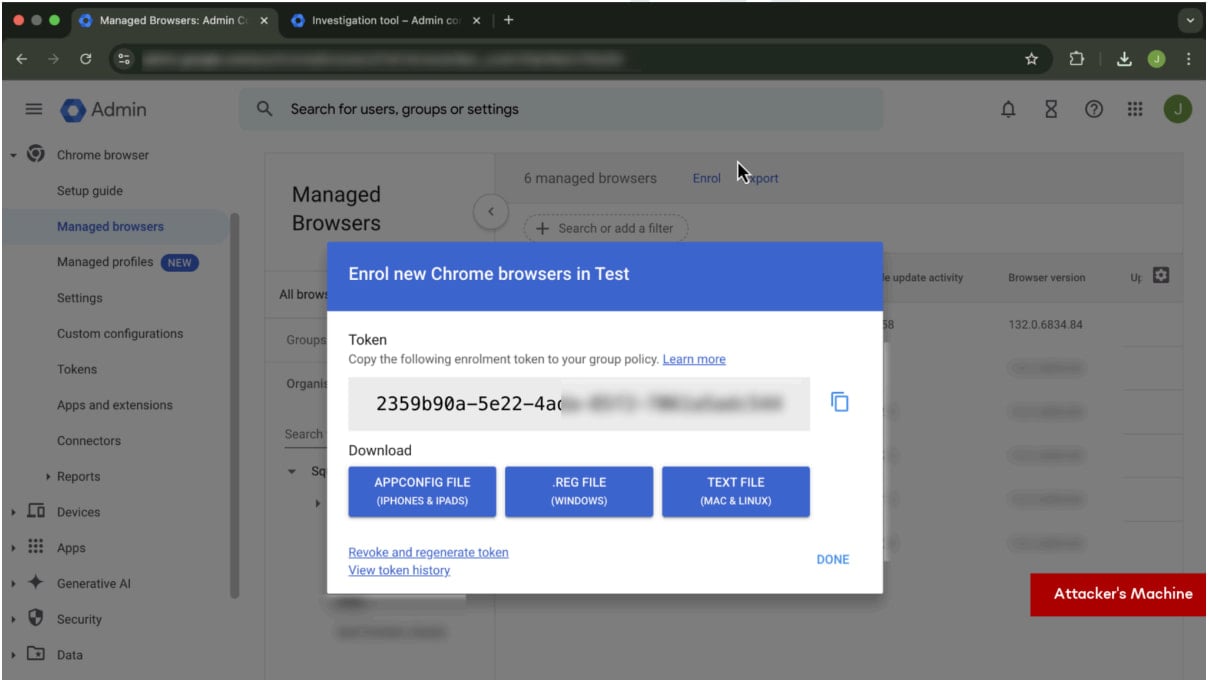 Enrolling the victim in a managed Google workspace
Enrolling the victim in a managed Google workspaceSource: SquareX
With the victim's profile under control, the attacker moves to take over the browser, which, in SquareX's demo, is done through a fake Zoom update.
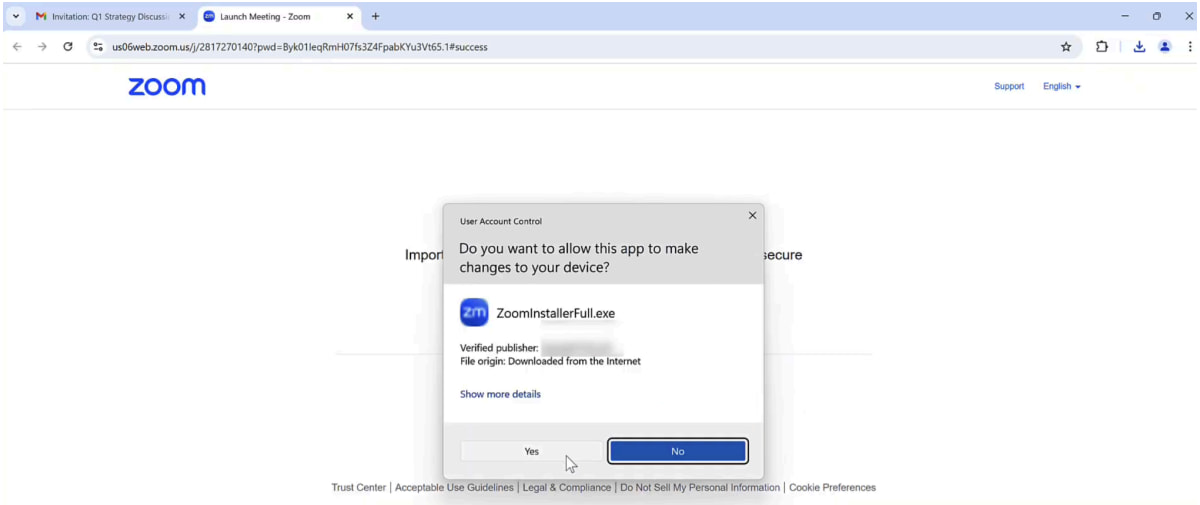 Prompting the victim to install a fake Zoom update
Prompting the victim to install a fake Zoom updateSource: SquareX
In the scenario highlighted by the researchers, a person may receive a Zoom invite, and when they click it and go to the Zoom webpage, the extension will instead inject malicious content stating that the Zoom client needs to be updated.
However, this download is an executable file containing an enrollment token, giving the attackers complete control over the victim's browser.
"Once enrolled, the attacker gains full control over the victim's browser, allowing them to silently access all web apps, install additional malicious extensions, redirect users to phishing sites, monitor/modify file downloads and many more," explains the SquareX researchers.
By leveraging Chrome's Native Messaging API, the attacker can establish a direct communication channel between the malicious extension and the victim's operating system.
This allows them to browse directories, modify files, install malware, execute arbitrary commands, capture keystrokes, extract sensitive data, and even activate the webcam and microphone.
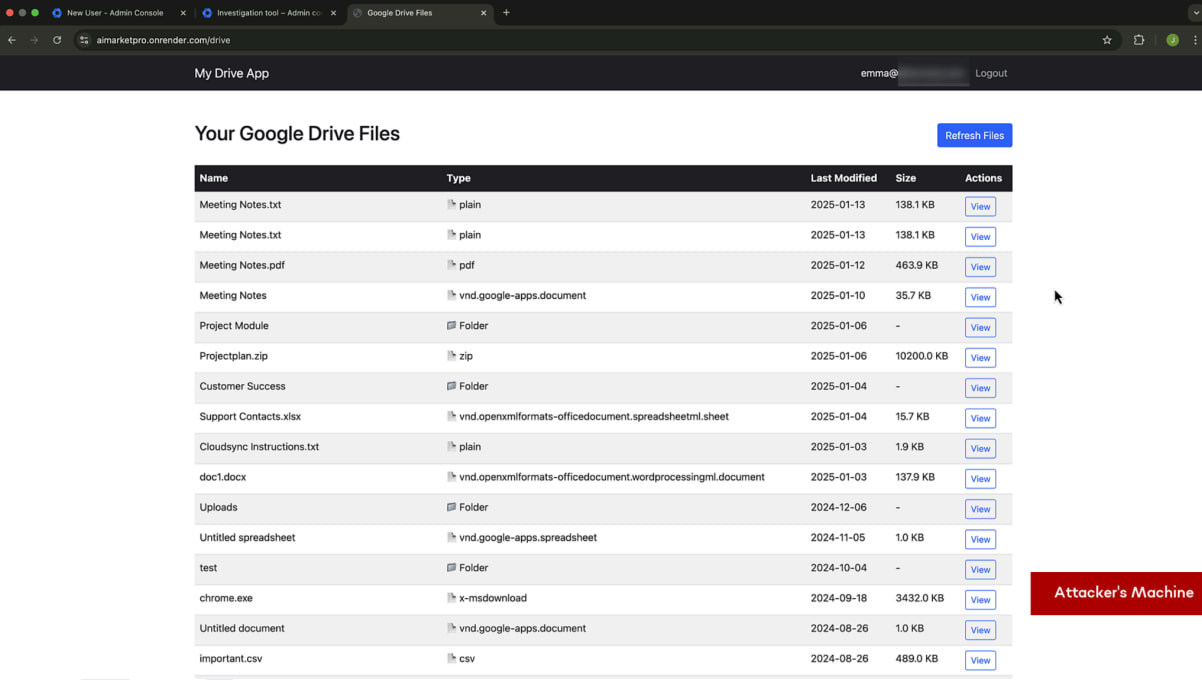 Accessing the victim's Drive contents
Accessing the victim's Drive contentsSource: SquareX
SquareX highlights the stealth and potent nature of the attack, underlining how difficult it would be for most users to realize something's off.
"Unlike previous extension attacks that involve elaborate social engineering, adversaries need only minimal permissions and a small social engineering step, with nearly no user interaction required to execute this attack," describes the report.
"Unless the victim is extremely security paranoid and is technically savvy enough to constantly navigate the Chrome settings to look for managed browser labels, there is no real visual indication that a browser has been hijacked."
Chrome extensions are often perceived as isolated risks, but recent events like a wave of hijacks impacting legitimate extensions used by millions proved otherwise.
BleepingComputer contacted Google about the new attack and will update our story if we receive a reply.
.png)














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·