Security researchers Thursday disclosed a new critical vulnerability affecting Domain Name System (DNS) resolvers that could be exploited by adversaries to carry out reflection-based denial-of-service attacks against authoritative nameservers.
The flaw, called 'TsuNAME,' was discovered by researchers from SIDN Labs and InternetNZ, which manage the national top-level internet domains '.nl' and '.nz' for the Netherlands and New Zealand, respectively.
"TsuNAME occurs when domain names are misconfigured with cyclic dependent DNS records, and when vulnerable resolvers access these misconfigurations, they begin looping and send DNS queries rapidly to authoritative servers and other resolvers," the researchers said.
A recursive DNS resolver is one of the core components involved in DNS resolution, i.e., converting a hostname such as www.google.com into a computer-friendly IP address like 142.250.71.36. To achieve this, it responds to a client's request for a web page by making a series of requests until it reaches the authoritative DNS nameserver for the requested DNS record. The authoritative DNS server is akin to a dictionary that holds the exact IP address for the domain that's being looked up.
But with TsuNAME, the idea is that misconfigurations during domain registration can create a cyclic dependency such that nameserver records for two zones point to each other, leading vulnerable resolvers to "simply bounce back from zone to zone, sending non-stop queries to the authoritative servers of both parent zones," thereby overwhelming their parent zone authoritative servers.
As to how this happens, it all boils down to recursive resolvers being oblivious to the cycle and not caching cyclically dependent name records.
Data gathered from the .nz domain found that two misconfigured domains alone led to a 50% increase in overall traffic volume for the .nz's authoritative servers. Google Public DNS (GDNS) and Cisco OpenDNS — which were abused to target .nz and .nl domains in 2020 — have since addressed the issue in their DNS resolver software.
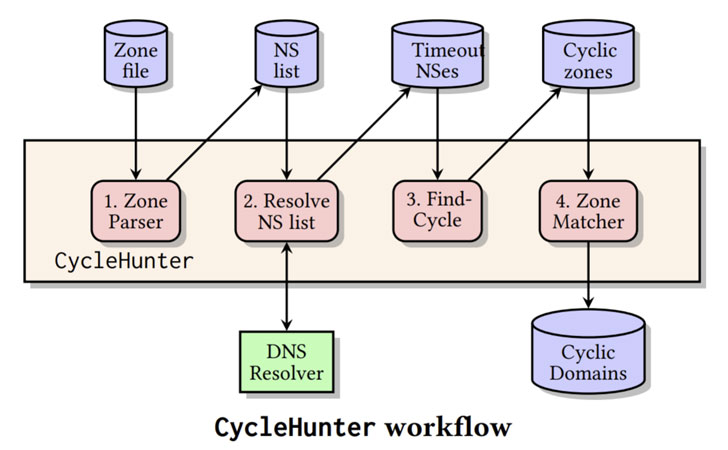
To mitigate the impact of TsuNAME in the wild, the researchers have published an open-source tool called CycleHunter that allows for authoritative DNS server operators to detect cyclic dependencies. The study also analyzed 184 million domains spanning seven large top-level domains and 3.6 million distinct nameserver records, uncovering 44 cyclic dependencies used by 1,435 domain names.
"Given that [nameserver] records can change at any time, there is no permanent solution," the researchers cautioned. "In other words, if a DNS zone has no cyclically dependent NS records at time t, it means that this zone is not vulnerable at only that particular time t. We therefore also recommend that registrars run CycleHunter on a regular basis, for instance, as part of their domain name registration process."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
175
3 years ago
175 
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·