Microsoft's Windows 10 and the upcoming Windows 11 versions have been found vulnerable to a new local privilege escalation vulnerability that permits users with low-level permissions access Windows system files, in turn, enabling them to unmask the operating system installation password and even decrypt private keys.
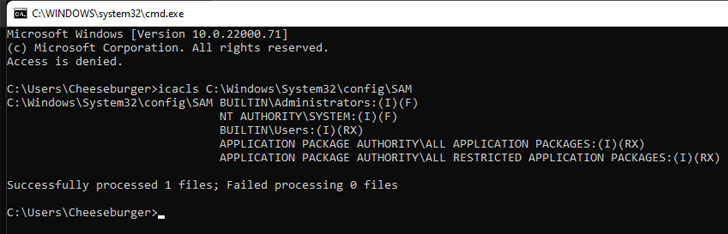
"Starting with Windows 10 build 1809, non-administrative users are granted access to SAM, SYSTEM, and SECURITY registry hive files," CERT Coordination Center (CERT/CC) said in a vulnerability note published Monday. "This can allow for local privilege escalation (LPE)."
The files in question are as follows -
c:\Windows\System32\config\sam c:\Windows\System32\config\system c:\Windows\System32\config\securityMicrosoft, which is tracking the vulnerability under the identifier CVE-2021-36934, acknowledged the issue, but has yet to roll out a patch, or provide a timeline for when the fix will be made available.
"An elevation of privilege vulnerability exists because of overly permissive Access Control Lists (ACLs) on multiple system files, including the Security Accounts Manager (SAM) database," the Windows makers noted. "An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
Successful exploitation of the flaw, however, necessitates that the attacker already has a foothold and is in possession of the ability to execute code on the victim system. In the interim, the CERT/CC is recommending that users restrict access to sam, system, and security files and delete VSS shadow copies of the system drive.
The latest disclosure also marks the third publicly disclosed unpatched bug in Windows since the release of Patch Tuesday updates on July 13. Besides CVE-2021-36934, two more weaknesses affecting the Print Spooler component have also been discovered, prompting Microsoft to urge all users to stop and disable the service to protect systems against exploitation.
Linux Distros Suffer from "Sequoia" Privilege Escalation Flaw
It's not just Windows. Remediations have been released for a security shortcoming affecting all Linux kernel versions from 2014 that can be exploited by malicious users and malware already deployed on a system to gain root-level privileges.
Dubbed "Sequoia" by researchers from cybersecurity firm Qualys, the issue has been assigned the identifier CVE-2021-33909 and affects default installations of Ubuntu 20.04, Ubuntu 20.10, Ubuntu 21.04, Debian 11, and Fedora 34 Workstation. Red Hat Enterprise Linux versions 6, 7, and 8 are also affected by the vulnerability.
Specifically, the flaw concerns a size_t-to-int type conversion vulnerability in the Linux Kernel's "seq_file" file system interface, permitting an unprivileged local attacker to create, mount, and delete a deep directory structure whose total path length exceeds 1GB, resulting in privilege escalation on the vulnerable host.
Separately, Qualys also disclosed a stack exhaustion denial-of-service vulnerability in systemd (CVE-2021-33910) that could be exploited by unprivileged attackers to crash the software suite and trigger a kernel panic.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
205
3 years ago
205 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·