BOOK THIS SPACE FOR AD
ARTICLE ADA sophisticated malware called Winos4.0 is being disguised as harmless gaming applications to infiltrate Windows-based systems. Learn about the multi-stage attack, data theft risks, and how to protect yourself from this emerging threat.
Cybersecurity researchers at Fortinet’s FortiGuard Labs have identified a new malicious campaign leveraging game-related applications to target Microsoft Windows users and deliver Winos4.0, a new and advanced malware framework similar to Cobalt Strike and Sliver.
Once downloaded and executed, these apps act as Trojan horses, downloading and installing the Winos4.0 framework.
The company’s findings shared with Hackread.com ahead of publishing on Wednesday, Nov 6, identified multiple samples of this malware hidden within gaming-related applications, including installation tools, speed boosters, and optimization utilities. By analyzing the decoded DLL file, they learned about the potential targeting of the education sector, as indicated by its file description, “校园政务” (Campus Administration).
Winos4.0 framework offers comprehensive functionality, a stable architecture, and efficient control over numerous online endpoints. It is rebuilt from Gh0stRat, a powerful remote access trojan created by the Chinese hacking group C. Rufus Security Team in 2008. Moreover, it includes several modular components, each handling distinct functions. Given its capabilities, Winos4.0 has already been deployed in multiple attack campaigns like Silver Fox.
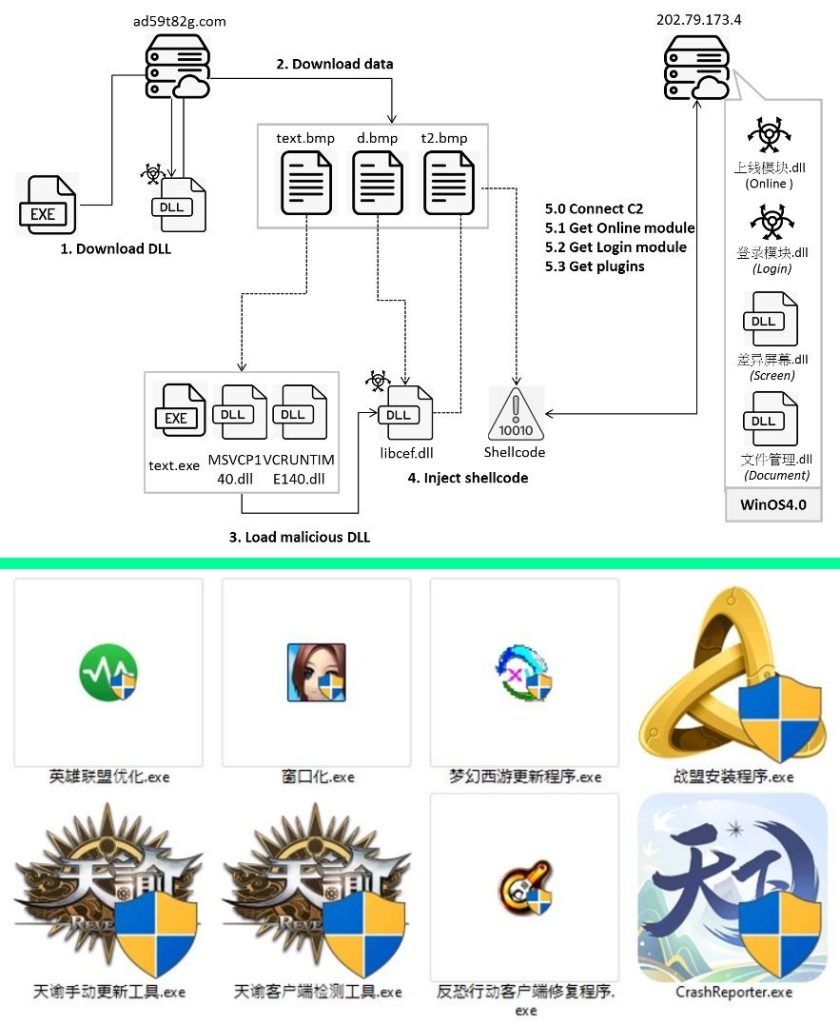
This multi-stage attack starts with retrieving a fake BMP file from a remote server, which is then XOR-decoded, extracting a DLL file named “you.dll”. This file is loaded through its export function “you” to proceed to the next stage.
“You.dll” downloads three files from a remote path after creating a folder with a random name, extracts one to reveal clean files (u72kOdQ.exe, MSVCP140.dll, and VCRUNTIME140.dll), and another to reveal the main malicious file, “libcef.dll”. The extracted files then load “libcef.dll” to inject shellcode and decode another file using an XOR key.
The injected shellcode loads APIs and retrieves configuration data to establish a connection using TCP protocol, sending a string to the C2 server, which responds with encrypted data. The data is decrypted using XOR, and a module is executed. The module (上线模块.dll) downloads data from the C2 server and records its address in the registry, setting the stage for the attack’s final phase.
The last stage launches the 登录模块.dll file, which performs tasks like enabling crash restart, recording clipboard content, checking window title bar for specific applications, collecting system information, checking for crypto wallet extensions, checking for anti-virus appliances, sending login messages, and maintaining connection to its C2server with heartbeats.
The capabilities of Winos4.0 show that it is a powerful framework that can be used to easily control compromised systems. Researchers recommend that users should be aware of the source of any new application and only download software from qualified sources.
Therefore, refrain from downloading applications and software from third-party app stores and websites. Before executing them, scan URLs and downloaded files on VirusTotal. Regularly scan your devices, especially after downloading new files. In office environments, block systems from downloading apps on workstations.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·