BOOK THIS SPACE FOR AD
ARTICLE AD
A newly discovered cyber-espionage group has been hacking governments and high-profile companies in Asia since at least 2020 using a combination of custom and existing malicious tools.
The threat group, tracked as Worok by ESET security researchers who first spotted it, has also attacked targets from Africa and the Middle East.
To date, Worok has been linked to attacks against telecommunications, banking, maritime, and energy companies, as well as military, government, and public sector entities.
In late 2020, Worok targeted a telecommunications company in East Asia, a bank in Central Asia, a maritime industry company in Southeast Asia, a government entity in the Middle East, and a private company in southern Africa.
While there have been no sightings until February 2022, ESET once again linked the group with new attacks against an energy company in Central Asia and a public sector entity in Southeast Asia.
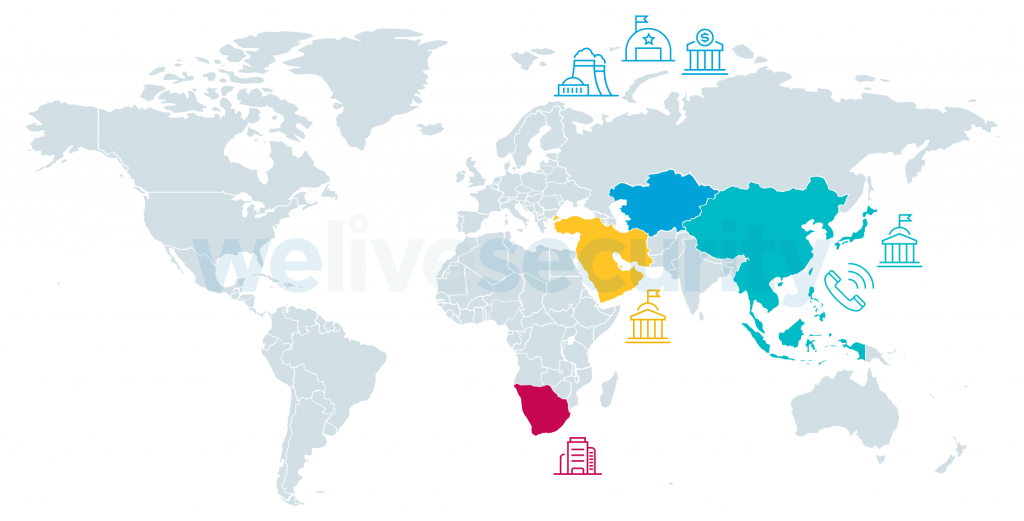 Worok attack map (ESET)
Worok attack map (ESET)"We believe the malware operators are after information from their victims because they focus on high-profile entities in Asia and Africa, targeting various sectors, both private and public, but with a specific emphasis on government entities," ESET malware researcher Thibaut Passilly said.
Even though the group used ProxyShell exploits to gain initial access to its victims' networks, the initial access vector remains unknown for most of its breaches.
"In such cases, typically webshells have been uploaded after exploiting these vulnerabilities, in order to provide persistence in the victim's network. Then the operators used various implants to gain further capabilities," Passilly added.
Worok's malicious toolset includes two loaders, a C++ loader known as CLRLoad and a C# loader dubbed PNGLoad helps the attackers hide malware payloads in PNG image files using steganography.
While ESET is yet to retrieve one of the final payloads delivered in the group's attacks, it did spot a new PowerShell backdoor dubbed PowHeartBeat, which replaced CLRLoad in incidents observed since February 2022 as the tool designed to launch PNGLoad on compromised systems.
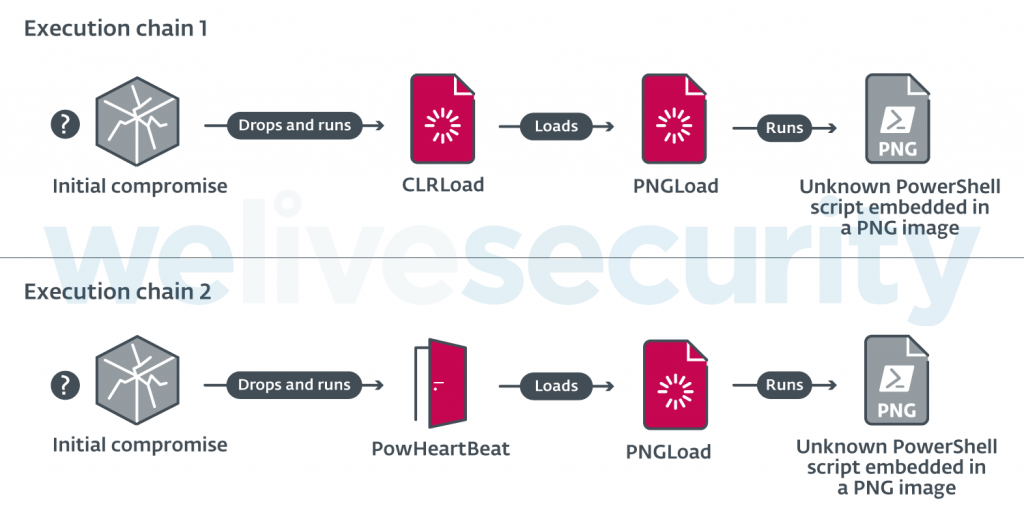 Worok attack chains (ESET)
Worok attack chains (ESET)PowHeartBeat comes with a wide range of capabilities, including file manipulation and command or process execution, as well as uploading or downloading files to and from victims' devices.
"Activity times and toolset indicate possible ties with TA428, but we make this assessment with low confidence," Passilly concluded.
"While our visibility is limited, we hope that shedding light on this group will encourage other researchers to share information about this group."
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·