A "logical flaw" has been disclosed in NPM, the default package manager for the Node.js JavaScript runtime environment, that enables malicious actors to pass off rogue libraries as legitimate and trick unsuspecting developers into installing them.
The supply chain threat has been dubbed "Package Planting" by researchers from cloud security firm Aqua. Following responsible disclosure on February 10, the underlying issue was remediated by NPM on April 26.
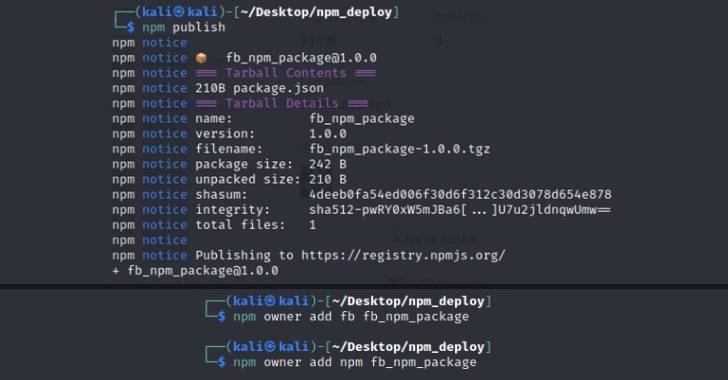
"Up until recently, NPM allowed adding anyone as a maintainer of the package without notifying these users or getting their consent," Aqua's Yakir Kadkoda said in a report published Tuesday.
This effectively meant that an adversary could create malware-laced packages and assign them to trusted, popular maintainers without their knowledge.
The idea here is to add credible owners associated with other popular NPM libraries to the attacker-controlled poisoned package in hopes that doing so would attract developers into downloading it.
The consequences of such a supply chain attack are significant for a number of reasons. Not only does it give a false sense of trust among developers, it could also inflict reputational damage to legitimate package maintainers.
The disclosure comes as Aqua uncovered two more flaws in the NPM platform related to two-factor authentication (2FA) that could be abused to facilitate account takeover attacks and publish malicious packages.
"The main problem is that any npm user can perform this and add other NPM users as maintainers of their own package," Kadkoda said. "Eventually, developers are responsible for what open source packages they use when building applications."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
154
2 years ago
154 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·