BOOK THIS SPACE FOR AD
ARTICLE ADNuGet packages are under attack! A new malware campaign exploits hidden code execution techniques to inject malware into developers’ machines. Learn how to protect yourself!
NuGet packages, a popular resource for developers, have become a target for malicious actors. Researchers at ReversingLabs uncovered an ongoing campaign targeting developers through deceptive NuGet packages leveraging a loophole in MSBuild integrations to bypass traditional security measures.
Researchers discovered connections between a malicious campaign discovered by Phylum in October 2023, which utilized PowerShell scripts within the “tools” directory for code execution, targeting over 700 packages but was quickly detected and removed.
In October 2023, researchers discovered three packages, ZendeskApi.Client.V2, Betalgo.Open.AI, and Forge.Open.AI, published to the NuGet repository, mimicking the original packages’ names (ZendeskApi.Client, Betalgo.OpenAI and Forge.OpenAI) through typosquatting. These packages were part of the same campaign ReversingLabs had been tracking since August 2023.
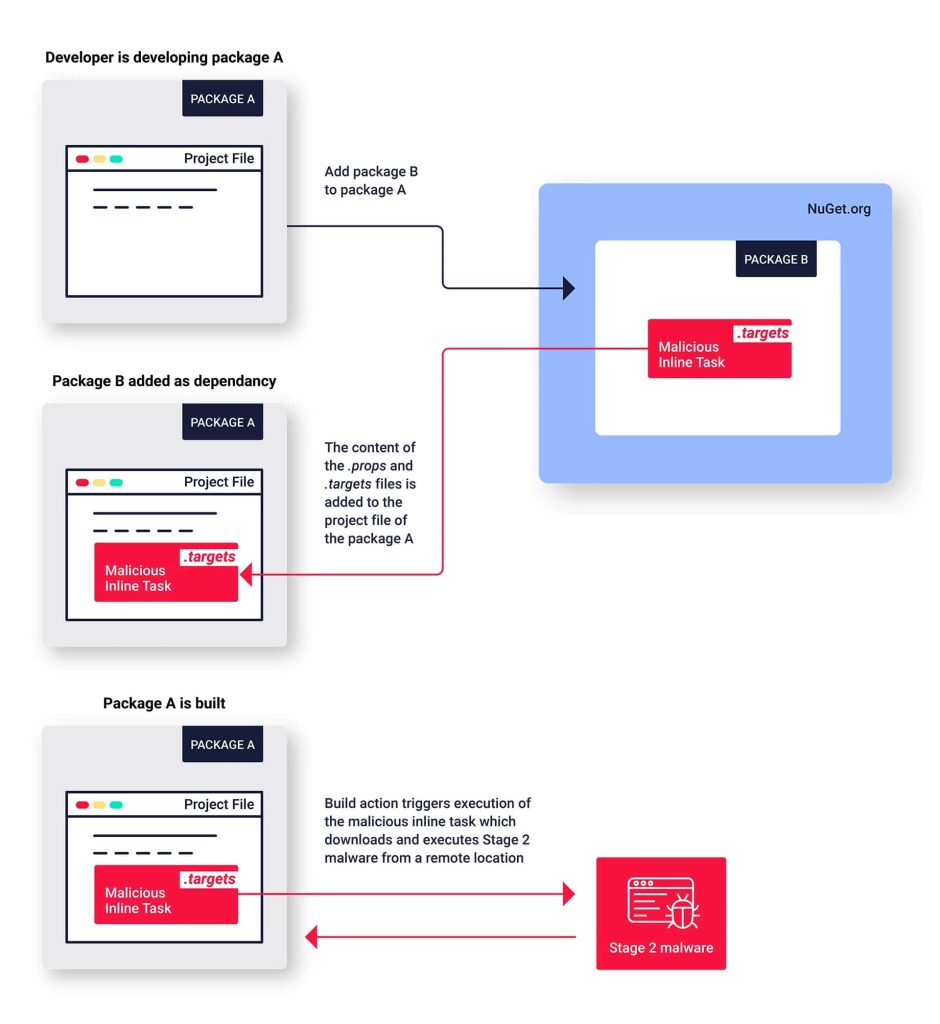
Typosquatting, although common, is unique to NuGet packages. Most malware is placed in the initialization and post-installation PowerShell scripts. However, some packages use a different approach, placing malicious functionality inside the <packageID>.targets file in the “build” directory.
The first NuGet package to use this technique was version 6.5.3 of Pathoschild.Stardew.Mod.Build.Config, which contained malicious functionality in initialization PowerShell scripts but not in version 6.5.3.
When a developer incorporates a compromised package, the “.targets” file gets imported into their project. This allows the embedded malicious code to execute silently during the build process, potentially granting attackers access to steal data, install additional malware, or disrupt critical system functions.
This exploitation technique appears to be inspired by the 2019 “IAmRoot” package, published as a proof-of-concept to demonstrate the vulnerability within NuGet’s MSBuild integrations. Despite ongoing discussions about the security risks associated with this functionality, the issue remains unresolved, leaving developers exposed.
The research reveals multiple waves of malicious packages targeting popular NuGet libraries through typosquatting. These packages disguise malicious code using spacing and tabs, artificially increasing download numbers to make them appear more trustworthy.
These used simple, obfuscated downloaders inserted into legitimate PE binary files using Intermediary Language (IL) Weaving, a .NET programming technique for modifying an application’s code after compilation.
The malicious NuGet packages were removed by the NuGet security team within 24 hours of their detection but the attackers prepared another set of packages, containing benign code in the .targets file.
This discovery goes on to show the nature of emerging cybersecurity threats, requiring consistent attention and strong security measures within the software supply chain. Code repositories and package managers must implement strong vetting procedures to identify and remove malicious packages before they can cause harm.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·